1、Python生成RSA秘钥,与签名验证
# rsa签名,保存私钥公钥到本地
from cryptography.hazmat.primitives.asymmetric import padding
from cryptography.hazmat.primitives import hashes
from cryptography.hazmat.primitives import serialization
from OpenSSL import crypto
rsa_key = crypto.rsa.generate_private_key(65537,2048)
print(rsa_key) #生成的是RSA私钥对象
sign_dat = rsa_key.sign(b'123456',padding.PKCS1v15(), hashes.SHA256())
verify_pass = rsa_key.public_key().verify(sign_dat,b'123456', padding.PKCS1v15(), hashes.SHA256())
print(verify_pass) #验证成功,函数默认返回None
with open('sign.data', 'wb') as f1:
f1.write(sign_dat)
pem_pri=rsa_key.private_bytes(
encoding=serialization.Encoding.PEM,
format=serialization.PrivateFormat.TraditionalOpenSSL,
encryption_algorithm=serialization.NoEncryption())
with open('rsa_key.pem', 'wb') as f2:
f2.write(pem_pri)
pem_pub=rsa_key.public_key().public_bytes(encoding=serialization.Encoding.PEM,
format=serialization.PublicFormat.SubjectPublicKeyInfo)
with open('pub_key.pem', 'wb') as f3:
f3.write(pem_pub)
2、openssl验证签名
openssl dgst -sha256 -verify pub_key.pem -signature sign.data src.txt
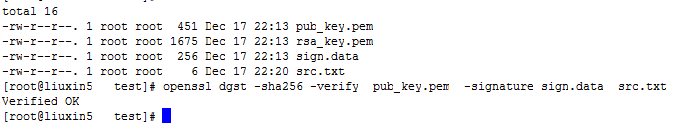
3、外部rsa秘钥使用Python签名
#openssl 的外部私钥 rsa 签名
from cryptography.hazmat.primitives import serialization
from cryptography.hazmat.backends import default_backend
from cryptography.hazmat.primitives.asymmetric import padding
from cryptography.hazmat.primitives import hashes
with open('rsa_key.pem', 'rb') as fr:
pem_pri=fr.read()
new_key = serialization.load_pem_private_key(pem_pri, password=None, backend=default_backend())
print(new_key) #RSA私钥对象
dat = new_key.sign(b'123456', padding.PKCS1v15(), hashes.SHA256())
with open('pub_key.pem', 'rb') as fp:
pem_pubkey=fp.read()
new_pubkey = serialization.load_pem_public_key(pem_pubkey, backend=default_backend())
result = new_pubkey.verify(dat, b'123456', padding.PKCS1v15(), hashes.SHA256())
print(result)
版权声明:本文为qq_38493182原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接和本声明。