一、请看这里
链接:https://pan.baidu.com/s/101H4AHZJriVj952LaqU6iw
提取码:glnn
--来自百度网盘超级会员V4的分享
最后总结的文档,懒着往网站上贴了。直接下载文档!
二、概念
- 权威dns
提供主机名到IP地址间的映射
- 递归dns
类似于114.。。用于域名查询。迭代权威服务器返回的应答,直到最终查询到ip,返回给客户端。
- 智能dns
可以让用户访问到同线路最近的服务器
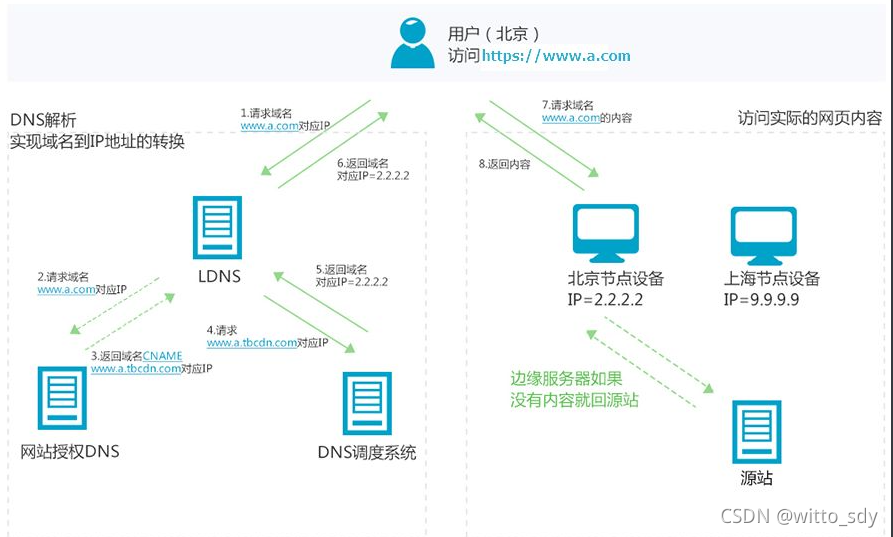
三、智能DNS流程
四、开源方案
1. smartdns
smartdns是python语言编写,基于twisted框架实现的dns server,能够支持针对不同的dns请求根据配置返回不同的解析结果。smartdns获取dns请求的源IP或者客户端IP(支持edns协议的请求可以获取客户端IP),根据本地的静态IP库获取请求IP的特性,包括所在的国家、省份、城市、ISP等,然后根据我们的调度配置返回解析结果。
缺点:
13年产品,早已经不维护了
小米开源的基于twisted实现的智能dns系统:Smartdns - smartdns - 服务器软件 - 深度开源 说明文档
2. bind9
作为权威DNS时:
- Response Rate Limiting (RRL):对DNS增强,以减少放大攻击
- Dynamically-Loadable Zones (DLZ):支持从外部数据库获取Zone数据,但不建议使用在高性的权威DNS。
- Minimum Re-load Time:支持配置文件动态加载。
- HSM Support:支持通过原生的 PKCS#11接口或OpenSSL PKCS#11的接口的HSM( Hardware Security Modules)。
- DNSSEC with In-line Signing:支持NSEC与NSEC3的安全协议的签名。
- Catalog Zones:支持多Zone的目录管理。
- Scalable Master/Slave Hierarchy:支持Master+多Slave组网,Slave从Master同步Zone配置。
作为递归DNS时:
- NXDOMAIN Redirect:当查询一个不存在域名时,转向一个Web页面,它依赖于DLZ特征。
- Flexible Cache Controls:对于不正确或过期的域名记录,灵活的缓存控制。
- Split DNS:通过配置不同的View,来保护部分私有信息。
- Optimum Cache Hit Rate:通过 DNS pre-fetch 技术来优化缓存命中率。
- Resolver rate-limiting:在受攻击下,对权威DNS查询限速,减轻对路径解析器的DDoS攻击影响。
- DNSSEC Validation:支持对DNSSEC的检验。
- GeoIP:支持基于来源不同的递归DNS的请求给出不同的响应。
- Response Policy Zone(RPZ):通过响应策略的Zone来减少对被认为是滥用或非法目的Zone的访问。
双License:ISC 与Mozilla Public 2.0。
3. powerDNS
开发语言:C++,扩展:Lua。
作为权威DNS时:
- Standards compliant serving of DNS information from all relevant databases
- Text files, dynamic scripts in various languages
- Native support for legacy BIND zonefiles
- Leading DNSSEC implementation
- worldwide, hosting >75% of all DNSSEC domains
- Powerful dynamic abilities
- Geographical load balancing
- Content redirection, ‘best answer’ generation
- Supported on generic hardware running generic operating systems
作为递归DNS时:
- Standards compliant resolution of domain names
- Strive for maximum resolution percentage
- or conversely, least customer complaints
- Powerful dynamic abilities
- Content redirection
- ‘best answer’ generation
- query & answer modification
- Filtering
- Supported on generic hardware running generic operating systems
提供相关的工具:
- dnsscope: query/answer latency time statistics
- dnsreplay: replay existing traffic against reference nameservers
- dnsgram: per-time period sampling of traffic to determine overloads
- dnswash: anonimize PCAP traces, hiding IP addresses, for third party analysis
支持API,承载在(Local socket,“raw” TCP/IP,RESTful API direct,)
- Statistics
- Provisioning
- Zone editing
- Master/slave operations
- Log-file investigations
- Configuration (updates)
- Stop/Start/Upgrade/Restart
License:GPL 2.0。
官方网站:https://www.powerdns.com/
文档全面,但基本是英文的。
4. coreDNS
开发语言:GO。
CoreDNS的前身是SkyDNS,它的主要目的是构建一个快速灵活的DNS服务器,让用户可以通过不同方式访问和使用DNS内的数据。它被设计为Caddy网络服务的一个服务器插件。CoreDNS的每个特性都可以被实现为可插拔的中间件,如,日志、基于文件的DNS以及多种后端技术,进而可以拼接多个插件来创建定制化的管道。CoreDNS已经得到扩展,可以直接被Kubernetes访问服务数据,并以KubeDNS的形式提供给用户使用。
CoreDNS同样可以权威与递归DNS,目前官方的中间件已有31个:
- bind: Serve zone data from a file; both DNSSEC (NSEC only) and DNS are supported (file).
- dnssec: Sign zone data on-the-fly
- cache: Caching
- etcd: Use etcd as a backend, i.e., a 101.5% replacement for SkyDNS
- kubernetes: Use k8s (kubernetes) as a backend
- proxy: Serve as a proxy to forward queries to some other (recursive) nameserver
- loadbalance:Load balancing of responses
- rewrite: Rewrite queries (qtype, qclass and qname)
- …
License: Apache-2.0。
官方网站:https://coredns.io/
五、bind9安装配置
安装环境centos7
- 1. 安装
yum install -y bind- 2. 配置
/etc/named.conf
acl beijingnet {
172.17.101.57;
172.17.101.56;
127.0.0.1;
};
acl shanghainet {
172.17.101.58;
};
options {
//listen-on port 53 { 127.0.0.1; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
//allow-query { localhost; };
allow-query { any; };
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable yes;
dnssec-validation yes;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.root.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
//test
view beijingview {
match-clients { beijingnet; };
zone "123.cn" {
type master;
file "123.cn.zone.beijing";
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
};
view shanghaiview {
match-clients { shanghainet; };
zone "123.cn" {
type master;
file "123.cn.zone.shanghai";
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
};
view otherview {
match-clients { any; };
include "/etc/named.rfc1912.zones.any";
};
//include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
[root@test58 named]# cat /etc/named.rfc1912.zones.any
zone "123.cn" IN {
type master;
file "123.cn.zone";
};[root@test58 named]# cat 123.cn.zone
$TTL 1D
@ IN SOA dns1 rname.invalid. (
7 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
@ NS dns1
@ NS dns2
dns1 A 172.17.101.58
dns2 A 172.17.101.30
www A 172.3.0.111
web A 172.3.0.2
mail A 172.3.0.5[root@test58 named]# cat 123.cn.zone.beijing
$TTL 1D
@ IN SOA dns1 rname.invalid. (
7 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
@ NS dns1
@ NS dns2
dns1 A 172.17.101.58
dns2 A 172.17.101.30
www A 172.10.101.10
web A 172.10.101.20
mail A 172.10.101.30[root@test58 named]# cat 123.cn.zone.shanghai
$TTL 1D
@ IN SOA dns1 rname.invalid. (
7 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
@ NS dns1
@ NS dns2
dns1 NS 172.17.101.58
dns2 NS 172.17.101.30
www A 127.0.0.1
web A 127.0.0.2
mail A 127.0.0.4- 3. 测试
使用dig命令测试,首先安装
yum install -y bind-utils101.57上的测试结果:ANSWER部分即为返回的ip
[root@test57 ~]# dig www.123.cn @172.17.101.58
; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7_9.7 <<>> www.123.cn @172.17.101.58
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 10279
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.123.cn. IN A
;; ANSWER SECTION:
www.123.cn. 86400 IN A 172.10.101.10
;; AUTHORITY SECTION:
123.cn. 86400 IN NS dns2.123.cn.
123.cn. 86400 IN NS dns1.123.cn.
;; ADDITIONAL SECTION:
dns1.123.cn. 86400 IN A 172.17.101.58
dns2.123.cn. 86400 IN A 172.17.101.30
;; Query time: 2 msec
;; SERVER: 172.17.101.58#53(172.17.101.58)
;; WHEN: 一 9月 13 11:35:16 CST 2021
;; MSG SIZE rcvd: 124
可以看到,101.57配置在beijingnet部分,返回的www对应的address101.10
dig 地址 @使用的网关