目录
easyre
用notepad++打开文件,直接用搜索就搜索出来flag{this_Is_a_EaSyRe}
用DIE打开,搜txt:flag,可发现flag
reverse1
reverse1 注意:得到的 flag 请包上 flag{} 提交
用DIE打开发现为64位,用ida打开,shift+F12查看Strings window窗口,this is the right flag!'点进去,发现页面,然后在那一行右键List cross references to,然后点击ok。
进入汇编语言中,如果看不懂,可以按下F5,变成伪代码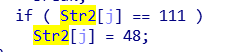
发现str2,点进去,发现{hello_world},然后在分析伪代码,右键111转换为char格式。
if ( Str2[j] == 'o' )
Str2[j] = '0';
发现是将o转换为0,所以得出flag{hell0_w0rld}
reverse2
用DIE打开发现为64位,用ida打开,shift+F12查看Strings window窗口,this is the right flag!'点进去,发现页面,然后在那一行右键List cross references to,然后点击ok。F5
if ( *(&flag + i) == 'i' || *(&flag + i) == 'r' )
*(&flag + i) = '1';
双击flag常量,发现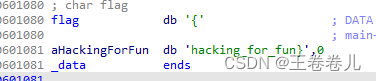
将hacking_for_fun中i和r替换为1,得到flag{hack1ng_fo1_fun}}
内涵的软件
发现为32位,用32为打开发现
v2 = "DBAPP{49d3c93df25caad81232130f3d2ebfad}";
试试flag{49d3c93df25caad81232130f3d2ebfad}出现答案。
新年快乐
用od工具包查壳提取,发现为32为有壳,先脱壳,od工具包内查壳脱壳工具,脱壳后用ida打开得到代码
int __cdecl main(int argc, const char **argv, const char **envp)
{
int result; // eax
char v4; // [esp+12h] [ebp-3Ah]
__int16 v5; // [esp+20h] [ebp-2Ch]
__int16 v6; // [esp+22h] [ebp-2Ah]sub_401910();
strcpy(&v4, "HappyNewYear!"); //strcpy函数为stringcopy缩写,将HappyNewYear!复制到v4中
v5 = 0;
memset(&v6, 0, '\x1E');
printf("please input the true flag:");
scanf("%s", &v5);
if ( !strncmp((const char *)&v5, &v4, strlen(&v4)) )
result = puts("this is true flag!");
else
result = puts("wrong!");
return result;
}
猜测flag为HappyNewYear!
xor
key = [ 'f',0xA,'k',0xC,'w','&','O','.','@',0x11,'x',0xD,'Z',';','U',0x11,'p',0x19,'F',0x1F,'v','"','M','#','D',0xE,'g',6,'h',0xF,'G','2','O' ]
flag = "f"
x = 0
for i in range(0,len(key)-1):
if isinstance(key[i],str):
if isinstance(key[i+1],str): x = ord(key[i]) ^ ord(key[i+1]) # key[i],key[i+1]同时为字符串
else: x = ord(key[i]) ^ key[i+1] # key[i]为字符串,key[i+1]为整数
else:
if isinstance(key[i+1],str): x = key[i] ^ ord(key[i+1]) # key[i]为整数,key[i+1]为字符串
else: x = key[i] ^ key[i+1] # key[i],key[i+1]同时为整数
flag = flag + chr(x)
print(flag)
flag{QianQiuWanDai_YiTongJiangHu}
helloword
apk文件,需要用android killer工具打开
直接用工程搜索搜flag{得到文件打开发现
flag{7631a988259a00816deda84afb29430a}
主文件在这里
reverse3
点击main_0跟进,来到主函数,如下(重要的语句已经做好了标记):
接下来先查看一下Str2这个字符串是啥,点进去,
再跟进sub_411AB0函数,如下(太长了叭…):
void *__cdecl sub_411AB0(char *a1, unsigned int a2, int *a3)
{
int v4; // STE0_4
int v5; // STE0_4
int v6; // STE0_4
int v7; // [esp+D4h] [ebp-38h]
signed int i; // [esp+E0h] [ebp-2Ch]
unsigned int v9; // [esp+ECh] [ebp-20h]
int v10; // [esp+ECh] [ebp-20h]
signed int v11; // [esp+ECh] [ebp-20h]
void *Dst; // [esp+F8h] [ebp-14h]
char *v13; // [esp+104h] [ebp-8h]if ( !a1 || !a2 )
return 0;
v9 = a2 / 3;
if ( (signed int)(a2 / 3) % 3 )
++v9;
v10 = 4 * v9;
*a3 = v10;
Dst = malloc(v10 + 1);
if ( !Dst )
return 0;
j_memset(Dst, 0, v10 + 1);
v13 = a1;
v11 = a2;
v7 = 0;
while ( v11 > 0 )
{
byte_41A144[2] = 0;
byte_41A144[1] = 0;
byte_41A144[0] = 0;
for ( i = 0; i < 3 && v11 >= 1; ++i )
{
byte_41A144[i] = *v13;
--v11;
++v13;
}
if ( !i )
break;
switch ( i )
{
case 1:
*((_BYTE *)Dst + v7) = aAbcdefghijklmn[(signed int)(unsigned __int8)byte_41A144[0] >> 2];
v4 = v7 + 1;
*((_BYTE *)Dst + v4++) = aAbcdefghijklmn[((byte_41A144[1] & 0xF0) >> 4) | 16 * (byte_41A144[0] & 3)];
*((_BYTE *)Dst + v4++) = aAbcdefghijklmn[64];
*((_BYTE *)Dst + v4) = aAbcdefghijklmn[64];
v7 = v4 + 1;
break;
case 2:
*((_BYTE *)Dst + v7) = aAbcdefghijklmn[(signed int)(unsigned __int8)byte_41A144[0] >> 2];
v5 = v7 + 1;
*((_BYTE *)Dst + v5++) = aAbcdefghijklmn[((byte_41A144[1] & 0xF0) >> 4) | 16 * (byte_41A144[0] & 3)];
*((_BYTE *)Dst + v5++) = aAbcdefghijklmn[((byte_41A144[2] & 0xC0) >> 6) | 4 * (byte_41A144[1] & 0xF)];
*((_BYTE *)Dst + v5) = aAbcdefghijklmn[64];
v7 = v5 + 1;
break;
case 3:
*((_BYTE *)Dst + v7) = aAbcdefghijklmn[(signed int)(unsigned __int8)byte_41A144[0] >> 2];
v6 = v7 + 1;
*((_BYTE *)Dst + v6++) = aAbcdefghijklmn[((byte_41A144[1] & 0xF0) >> 4) | 16 * (byte_41A144[0] & 3)];
*((_BYTE *)Dst + v6++) = aAbcdefghijklmn[((byte_41A144[2] & 0xC0) >> 6) | 4 * (byte_41A144[1] & 0xF)];
*((_BYTE *)Dst + v6) = aAbcdefghijklmn[byte_41A144[2] & 0x3F];
v7 = v6 + 1;
break;
}
}
*((_BYTE *)Dst + v7) = 0;
return Dst;
加密过程十分复杂,但是后面我们注意到一个名叫aAbcdefghijklmn的数组,有点怪怪的我们点进去看看
哦嚯!这不是base64编码嘛!
我们直接将Str2字符串减去 j,再将其base64逆运算(base64是一个可逆的加密算法)就可以得到结果!
python代码如下:
import base64
str = 'e3nifIH9b_C@n@dH'
flag = ''
index = ''
for i in range(0,len(str)):
index = chr(ord(str[i]) - i)
flag += index
flag = base64.b64decode(flag)
print(flag)
运行,flag出来了!!!{i_l0ve_you}
不一样的flag
打开查看程序发现上下左右,查看程序
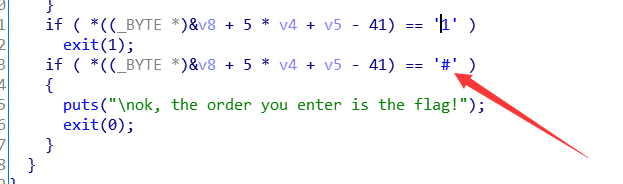
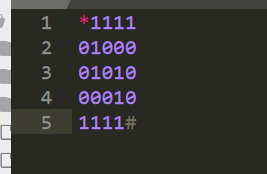
直接按照命令来进行走
走0不走1
得到字符串:222441144222