snmp
- SNMP Agent Default Community Name (public)
修改配置文件/etc/snmp/snmpd.conf将Public改成其他具有复杂度的字符串如Admin123...,保存后重新启动SNMP服务即可。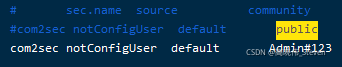
[root@localhost ~]# nmap -sU -p161 -script=snmp-brute 127.0.0.1 Starting Nmap 6.40 ( http://nmap.org ) at 2021-11-09 07:35 CST Nmap scan report for localhost (127.0.0.1) Host is up (0.000033s latency). PORT STATE SERVICE 161/udp closed snmp Nmap done: 1 IP address (1 host up) scanned in 0.27 seconds - SNMP 'GETBULK' Reflection DDoS
使用net-snmp-create-v3-user命令进行snmp v3配置(需要再snmp服务停止的状态下才能生效)[root@VM_Server ~]# net-snmp-create-v3-user Enter a SNMPv3 user name to create: snmpuser Enter authentication pass-phrase: snmpv3@2020md5 Enter encryption pass-phrase: [press return to reuse the authentication pass-phrase] snmpv3@2020des adding the following line to /var/lib/net-snmp/snmpd.conf: createUser snmpuser MD5 "snmpv3@2020md5" DES snmpv3@2020des adding the following line to /etc/snmp/snmpd.conf: rwuser snmpuser生效后可以查看到配置文件中的新增
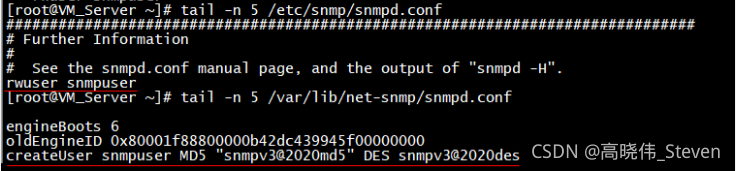
启动snmp服务后,使用snmpwalk命令验证
snmpwalk -v3 -usnmpuser -lauth -aMD5 -A"snmpv3@2020md5" -X"snmpv3@2020des" 127.0.0.1
samba
- SMB Signing not required
修改配置文件/etc/samba/smb.conf,将client signing = mandatory和server signing = mandatory添加到[global]后保存文件,然后重启samba服务[root@localhost ~]# nmap -sS -sV -Pn -p 445 --script="smb-security-mode" 127.0.0.1 Starting Nmap 6.40 ( http://nmap.org ) at 2021-11-09 07:22 CST Nmap scan report for localhost (127.0.0.1) Host is up (0.000032s latency). PORT STATE SERVICE VERSION 445/tcp open netbios-ssn Samba smbd 3.X (workgroup: LOCALHOST) Host script results: | smb-security-mode: | Account that was used for smb scripts: guest | User-level authentication | SMB Security: Challenge/response passwords supported |_ Message signing required Service detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 6.38 seconds
ssh
- SSH Server CBC Mode Ciphers Enabled
修改/etc/ssh/sshd_config文件,最后一行添加如下内容
Ciphers aes128-ctr,aes192-ctr,aes256-ctr,arcfour256,arcfour128,arcfour Macs hmac-sha1,hmac-ripemd160使用ssh命令验证
ssh -vv -oCiphers=aes128-cbc,3des-cbc,blowfish-cbc 目标IP ssh -vv -oMACs=hmac-md5 目标IP
使用Nmap验证nmap --script ssh2-enum-algos -sV -p 22 目标IP
版权声明:本文为superbfly原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接和本声明。