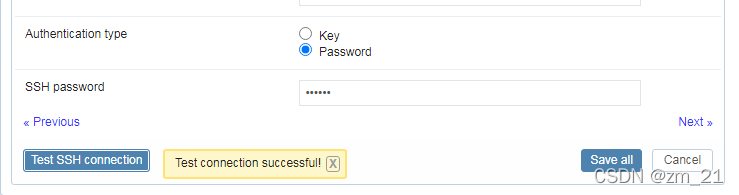
一步一坑,总算能使用,问题还在解决中~~~~,目前看,6.0版本有bug,包括:无法
删除server和无法设置sftp用户名密码等等。下载了8.5,功能都正常了
MONyog是一款MySQL监控工具,可以实时监控SQL运行状态。
现在名字应该是SQL DM,,SQL DM is a MySQL monitoring tool that gives DBAs real-time insights for optimizing the performance of MySQL servers.
下面的Mysql,ssh,sftp 安装在ubuntu上。Monyog安装在window上
1。安装mysql
sudo apt-get install mysql-server mysql-client
注意:
- )修改/etc/mysql/mysql.conf.d/mysqld.cnf中的bind=0.0.0.0,
重启 /etc/init.d/mysql restart
- )授权:
Mysql –uroot -p
> grant all privileges on *.* to ‘root@%’ identified by '123456';
>flush privileges;
3)修改mysql log文件权限,否则报错
chmod 755 /var/log/mysql/*
2。安装ssh
1) sudo apt-get install openssh-server
2) sudo vi /etc/ssh/sshd_config,添加以下内容:
KexAlgorithms diffie-hellman-group1-sha1,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group14-sha1
Ciphers 3des-cbc,blowfish-cbc,aes128-cbc,aes128-ctr,aes256-ctr
3) 重启ssh服务
service sshd restart
3。配置sftp
1) 安装完ssh后,修改sshd_config
sudo vi /etc/ssh/sshd_config
添加以下内容:
#Subsystem sftp /usr/lib/openssh/sftp-server
Subsystem sftp internal-sftp
AllowUsers test testsftp
如果要指定用户或者组访问sftp,需要使用Match模块
注意:1)一定要放在文件末尾,否则其后内容都视为match子元素,
2)对用户或者组的限制一定要有缩进,否则视为所有用户的限制
#Match Group sftp-users
#ChrootDirectory /sftp
#ForceCommand internal-sftp
#AllowTcpForwarding no
#X11Forwarding no
#Match User testsftp
# ChrootDirectory /sftp
# ForceCommand internal-sftp
# AllowTcpForwarding no
# X11Forwarding no
2) 重启ssh服务:
service sshd restart
3) 测试sftp是否安装成功:
sftp testsftp@192.168.31.49
4。安装Monyog
1) 下载Monyog试用版
2) 安装,在服务里启动
访问http://127.0.0.1:5555/
账号:admin,密码:123456
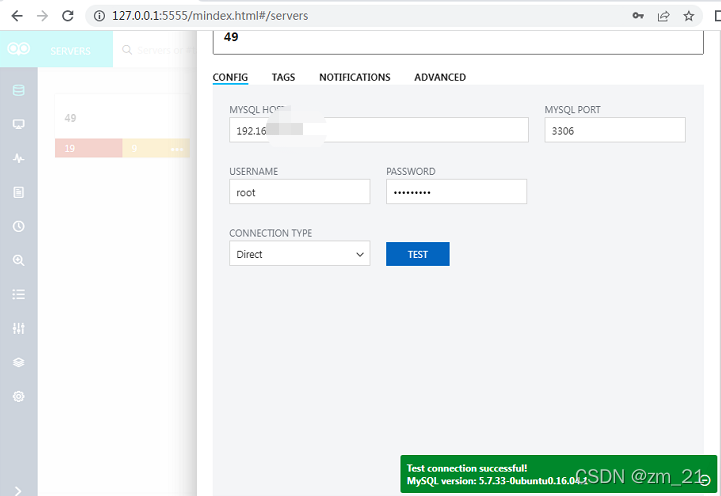
3) 配置mysql后,点击Test..,如下显示成功就可以了
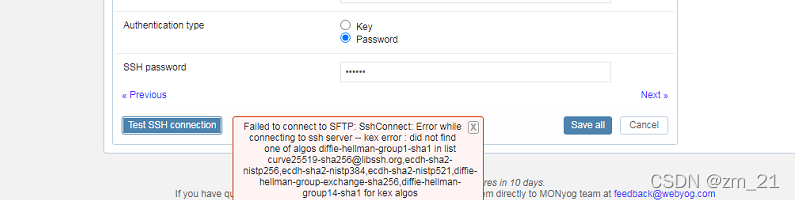
问题1:
Failed to connect to SFTP: SshConnect: Error while connecting to ssh server -- kex error : did not find one of algos diffie-hellman-group1-sha1 in list curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group14-sha1 for kex algos
解决方法:
/etc/ssh/sshd_config末尾添加:
KexAlgorithms diffie-hellman-group1-sha1,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group14-sha1
Ciphers 3des-cbc,blowfish-cbc,aes128-cbc,aes128-ctr,aes256-ctr
重启ssh,然后就可以了