下载附件,为一个压缩包
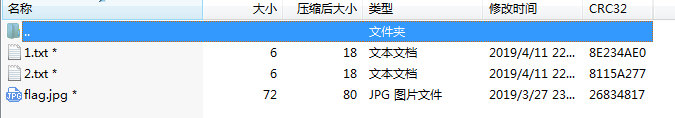
看到1,.txt和2.txt的文件大小很小,只有6个字节,尝试使用crc爆破:
使用CRC32.py进行爆破:


将两张图内的字符串组成密码字典:
s1=["1x5NQ8","9O2a5H","G1qi4N","IsCdeH","NjDZOc","OvJ7Un","P8CUk2","PT0xov","QTqIto","Rh5f6k","XBiGbJ","Z3AdV_","gsombC","mY3L6b","newctf","p7plP7","t3mmQT","vBENeA"]
s2=["17LE1V","53QD05","5Cm55e","6cfFvu","9l8GQb","BzTRNZ","EcSldq","HqVcs7","JpB1Br","LuKbrT","TRyOcs","_5IbAC","bugku_","dpn8Ey","mz9jRH","q5ekFH","w0l8vn","yOOyO0","zRUFdx"]
l=[]
for i in s2:
for j in s1:
l.append(i+j)
with open ('pw.txt', 'w') as fo:
for k in l:
fo.write(k+'\n')使用Advanced Archive Password Recovery进行字典爆破:

得到密码为`bugku_newctf`
解压出flag.jpg。结果无法打开。
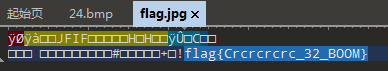
用文本打开,可以看到flag就在文件尾部:
版权声明:本文为qq_26243045原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接和本声明。