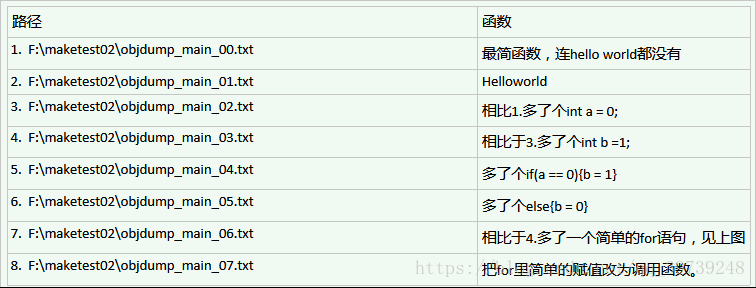
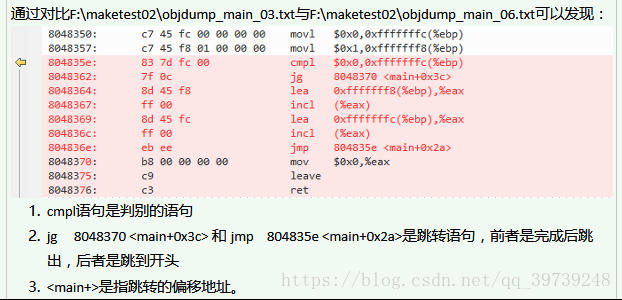
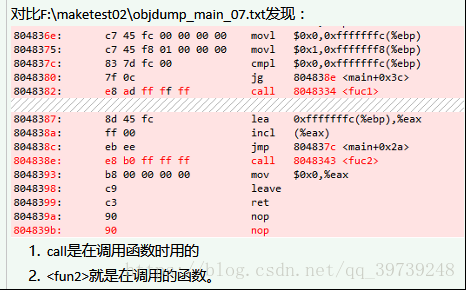
因近期工作需要,需要利用objdump工具剖析程序指定可执行程序,以检查错误函数(语句)。
objdump命令参考:https://blog.csdn.net/zoomdy/article/details/50563680
本文以最简单的程序开始,剖析反汇编之后的程序最小执行系统以及初始化、判断语句、循环语句以及函数及其调用过程在反汇编指令集中的形式,方便在工作过程中的异常程序中寻找异常地址。
文件组成:
最简文件组成:main.c Makefile
Makefile代码:
TRGET = main.out
all: clean $(TRGET)
$(TRGET):main.o
cc main.o -o $(TRGET)
main.o:
clean:
rm -f *.o;rm -f *.out
编辑方式:以挂载的方式挂载到linux系统上,编辑在Window上的NotePad++
从最简程序开始:(这是我能想到最简单的程序了)
#include <stdio.h>
int main()
{
return 0;
}反汇编指令:
objdump -C -S main.out > objdump_main_00.txt
反汇编结果:
main.out: file format elf32-i386
Disassembly of section .init:
08048254 <_init>:
8048254: 55 push %ebp
8048255: 89 e5 mov %esp,%ebp
8048257: 83 ec 08 sub $0x8,%esp
804825a: e8 51 00 00 00 call 80482b0 <call_gmon_start>
804825f: e8 a4 00 00 00 call 8048308 <frame_dummy>
8048264: e8 87 01 00 00 call 80483f0 <__do_global_ctors_aux>
8048269: c9 leave
804826a: c3 ret
Disassembly of section .plt:
0804826c <__libc_start_main@plt-0x10>:
804826c: ff 35 20 95 04 08 pushl 0x8049520
8048272: ff 25 24 95 04 08 jmp *0x8049524
8048278: 00 00 add %al,(%eax)
...
0804827c <__libc_start_main@plt>:
804827c: ff 25 28 95 04 08 jmp *0x8049528
8048282: 68 00 00 00 00 push $0x0
8048287: e9 e0 ff ff ff jmp 804826c <_init+0x18>
Disassembly of section .text:
0804828c <_start>:
804828c: 31 ed xor %ebp,%ebp
804828e: 5e pop %esi
804828f: 89 e1 mov %esp,%ecx
8048291: 83 e4 f0 and $0xfffffff0,%esp
8048294: 50 push %eax
8048295: 54 push %esp
8048296: 52 push %edx
8048297: 68 ac 83 04 08 push $0x80483ac
804829c: 68 58 83 04 08 push $0x8048358
80482a1: 51 push %ecx
80482a2: 56 push %esi
80482a3: 68 34 83 04 08 push $0x8048334
80482a8: e8 cf ff ff ff call 804827c <__libc_start_main@plt>
80482ad: f4 hlt
80482ae: 90 nop
80482af: 90 nop
080482b0 <call_gmon_start>:
80482b0: 55 push %ebp
80482b1: 89 e5 mov %esp,%ebp
80482b3: 53 push %ebx
80482b4: e8 00 00 00 00 call 80482b9 <call_gmon_start+0x9>
80482b9: 5b pop %ebx
80482ba: 81 c3 63 12 00 00 add $0x1263,%ebx
80482c0: 52 push %edx
80482c1: 8b 83 fc ff ff ff mov 0xfffffffc(%ebx),%eax
80482c7: 85 c0 test %eax,%eax
80482c9: 74 02 je 80482cd <call_gmon_start+0x1d>
80482cb: ff d0 call *%eax
80482cd: 58 pop %eax
80482ce: 5b pop %ebx
80482cf: c9 leave
80482d0: c3 ret
80482d1: 90 nop
80482d2: 90 nop
80482d3: 90 nop
080482d4 <__do_global_dtors_aux>:
80482d4: 55 push %ebp
80482d5: 89 e5 mov %esp,%ebp
80482d7: 83 ec 08 sub $0x8,%esp
80482da: 80 3d 38 95 04 08 00 cmpb $0x0,0x8049538
80482e1: 74 0f je 80482f2 <__do_global_dtors_aux+0x1e>
80482e3: eb 1f jmp 8048304 <__do_global_dtors_aux+0x30>
80482e5: 8d 76 00 lea 0x0(%esi),%esi
80482e8: 83 c0 04 add $0x4,%eax
80482eb: a3 34 95 04 08 mov %eax,0x8049534
80482f0: ff d2 call *%edx
80482f2: a1 34 95 04 08 mov 0x8049534,%eax
80482f7: 8b 10 mov (%eax),%edx
80482f9: 85 d2 test %edx,%edx
80482fb: 75 eb jne 80482e8 <__do_global_dtors_aux+0x14>
80482fd: c6 05 38 95 04 08 01 movb $0x1,0x8049538
8048304: c9 leave
8048305: c3 ret
8048306: 89 f6 mov %esi,%esi
08048308 <frame_dummy>:
8048308: 55 push %ebp
8048309: 89 e5 mov %esp,%ebp
804830b: 83 ec 08 sub $0x8,%esp
804830e: a1 4c 94 04 08 mov 0x804944c,%eax
8048313: 85 c0 test %eax,%eax
8048315: 74 19 je 8048330 <frame_dummy+0x28>
8048317: b8 00 00 00 00 mov $0x0,%eax
804831c: 85 c0 test %eax,%eax
804831e: 74 10 je 8048330 <frame_dummy+0x28>
8048320: 83 ec 0c sub $0xc,%esp
8048323: 68 4c 94 04 08 push $0x804944c
8048328: ff d0 call *%eax
804832a: 83 c4 10 add $0x10,%esp
804832d: 8d 76 00 lea 0x0(%esi),%esi
8048330: c9 leave
8048331: c3 ret
8048332: 90 nop
8048333: 90 nop
08048334 <main>:
8048334: 55 push %ebp
8048335: 89 e5 mov %esp,%ebp
8048337: 83 ec 08 sub $0x8,%esp
804833a: 83 e4 f0 and $0xfffffff0,%esp
804833d: b8 00 00 00 00 mov $0x0,%eax
8048342: 83 c0 0f add $0xf,%eax
8048345: 83 c0 0f add $0xf,%eax
8048348: c1 e8 04 shr $0x4,%eax
804834b: c1 e0 04 shl $0x4,%eax
804834e: 29 c4 sub %eax,%esp
8048350: b8 00 00 00 00 mov $0x0,%eax
8048355: c9 leave
8048356: c3 ret
8048357: 90 nop
08048358 <__libc_csu_init>:
8048358: 55 push %ebp
8048359: 89 e5 mov %esp,%ebp
804835b: 57 push %edi
804835c: 56 push %esi
804835d: 53 push %ebx
804835e: 83 ec 0c sub $0xc,%esp
8048361: e8 00 00 00 00 call 8048366 <__libc_csu_init+0xe>
8048366: 5b pop %ebx
8048367: 81 c3 b6 11 00 00 add $0x11b6,%ebx
804836d: e8 e2 fe ff ff call 8048254 <_init>
8048372: 8d 83 20 ff ff ff lea 0xffffff20(%ebx),%eax
8048378: 8d 93 20 ff ff ff lea 0xffffff20(%ebx),%edx
804837e: 89 45 f0 mov %eax,0xfffffff0(%ebp)
8048381: 29 d0 sub %edx,%eax
8048383: 31 f6 xor %esi,%esi
8048385: c1 f8 02 sar $0x2,%eax
8048388: 39 c6 cmp %eax,%esi
804838a: 73 16 jae 80483a2 <__libc_csu_init+0x4a>
804838c: 89 d7 mov %edx,%edi
804838e: 89 f6 mov %esi,%esi
8048390: ff 14 b2 call *(%edx,%esi,4)
8048393: 8b 4d f0 mov 0xfffffff0(%ebp),%ecx
8048396: 29 f9 sub %edi,%ecx
8048398: 46 inc %esi
8048399: c1 f9 02 sar $0x2,%ecx
804839c: 39 ce cmp %ecx,%esi
804839e: 89 fa mov %edi,%edx
80483a0: 72 ee jb 8048390 <__libc_csu_init+0x38>
80483a2: 83 c4 0c add $0xc,%esp
80483a5: 5b pop %ebx
80483a6: 5e pop %esi
80483a7: 5f pop %edi
80483a8: c9 leave
80483a9: c3 ret
80483aa: 89 f6 mov %esi,%esi
080483ac <__libc_csu_fini>:
80483ac: 55 push %ebp
80483ad: 89 e5 mov %esp,%ebp
80483af: 57 push %edi
80483b0: 56 push %esi
80483b1: 53 push %ebx
80483b2: e8 00 00 00 00 call 80483b7 <__libc_csu_fini+0xb>
80483b7: 5b pop %ebx
80483b8: 81 c3 65 11 00 00 add $0x1165,%ebx
80483be: 8d 83 20 ff ff ff lea 0xffffff20(%ebx),%eax
80483c4: 8d bb 20 ff ff ff lea 0xffffff20(%ebx),%edi
80483ca: 29 f8 sub %edi,%eax
80483cc: c1 f8 02 sar $0x2,%eax
80483cf: 83 ec 0c sub $0xc,%esp
80483d2: 8d 70 ff lea 0xffffffff(%eax),%esi
80483d5: eb 05 jmp 80483dc <__libc_csu_fini+0x30>
80483d7: 90 nop
80483d8: ff 14 b7 call *(%edi,%esi,4)
80483db: 4e dec %esi
80483dc: 83 fe ff cmp $0xffffffff,%esi
80483df: 75 f7 jne 80483d8 <__libc_csu_fini+0x2c>
80483e1: e8 2e 00 00 00 call 8048414 <_fini>
80483e6: 83 c4 0c add $0xc,%esp
80483e9: 5b pop %ebx
80483ea: 5e pop %esi
80483eb: 5f pop %edi
80483ec: c9 leave
80483ed: c3 ret
80483ee: 90 nop
80483ef: 90 nop
080483f0 <__do_global_ctors_aux>:
80483f0: 55 push %ebp
80483f1: 89 e5 mov %esp,%ebp
80483f3: 53 push %ebx
80483f4: 52 push %edx
80483f5: bb 3c 94 04 08 mov $0x804943c,%ebx
80483fa: a1 3c 94 04 08 mov 0x804943c,%eax
80483ff: eb 0a jmp 804840b <__do_global_ctors_aux+0x1b>
8048401: 8d 76 00 lea 0x0(%esi),%esi
8048404: 83 eb 04 sub $0x4,%ebx
8048407: ff d0 call *%eax
8048409: 8b 03 mov (%ebx),%eax
804840b: 83 f8 ff cmp $0xffffffff,%eax
804840e: 75 f4 jne 8048404 <__do_global_ctors_aux+0x14>
8048410: 58 pop %eax
8048411: 5b pop %ebx
8048412: c9 leave
8048413: c3 ret
Disassembly of section .fini:
08048414 <_fini>:
8048414: 55 push %ebp
8048415: 89 e5 mov %esp,%ebp
8048417: 53 push %ebx
8048418: e8 00 00 00 00 call 804841d <_fini+0x9>
804841d: 5b pop %ebx
804841e: 81 c3 ff 10 00 00 add $0x10ff,%ebx
8048424: 50 push %eax
8048425: e8 aa fe ff ff call 80482d4 <__do_global_dtors_aux>
804842a: 59 pop %ecx
804842b: 5b pop %ebx
804842c: c9 leave
804842d: c3 ret
由此可见执行程序的最简形式,也是最基本的组成部分:.init段、.plt段、.text段等。
在此基础之上分别在main函数里添加初始化语句,反汇编之,并利用BCompare等软件对比不同,即可发现初始化语句在反汇编指令中的形式,方便之后对较大程序的反汇编指令阅读。
以下为本次实验步骤:
这里给出for语句以及调用函数时反汇编指令,初始化、调用系统函数等语句的反汇编,读者可利用main.c和Makefile以及objdump指令自行实验。
版权声明:本文为qq_39739248原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接和本声明。