1.还是学习过程中的app 易果,先抓包
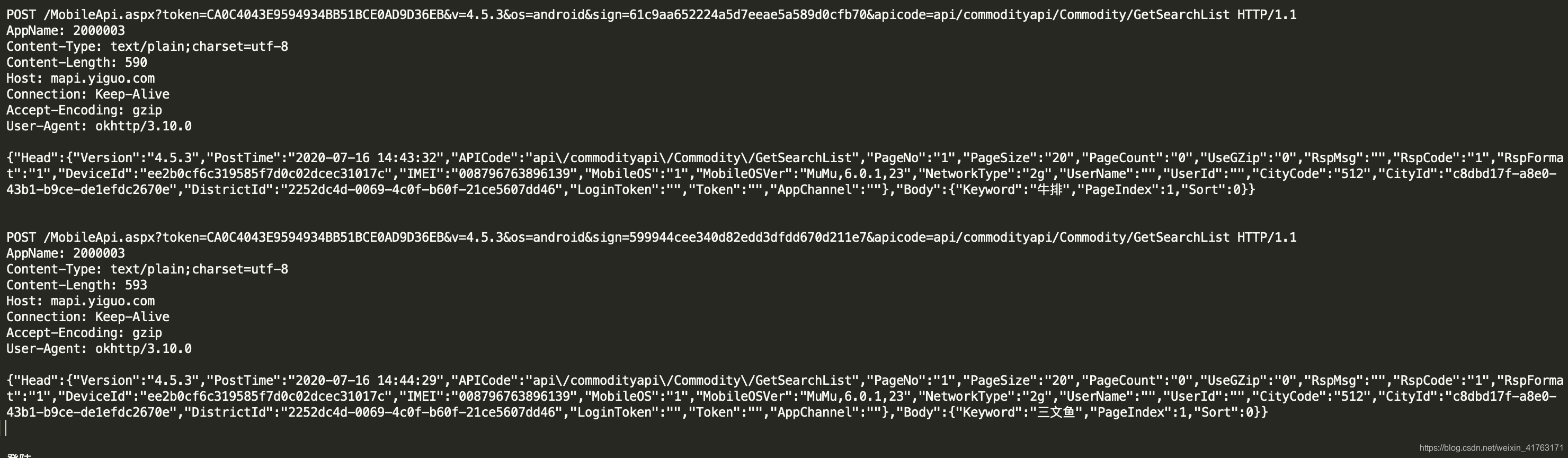
搜索的列表页,2次
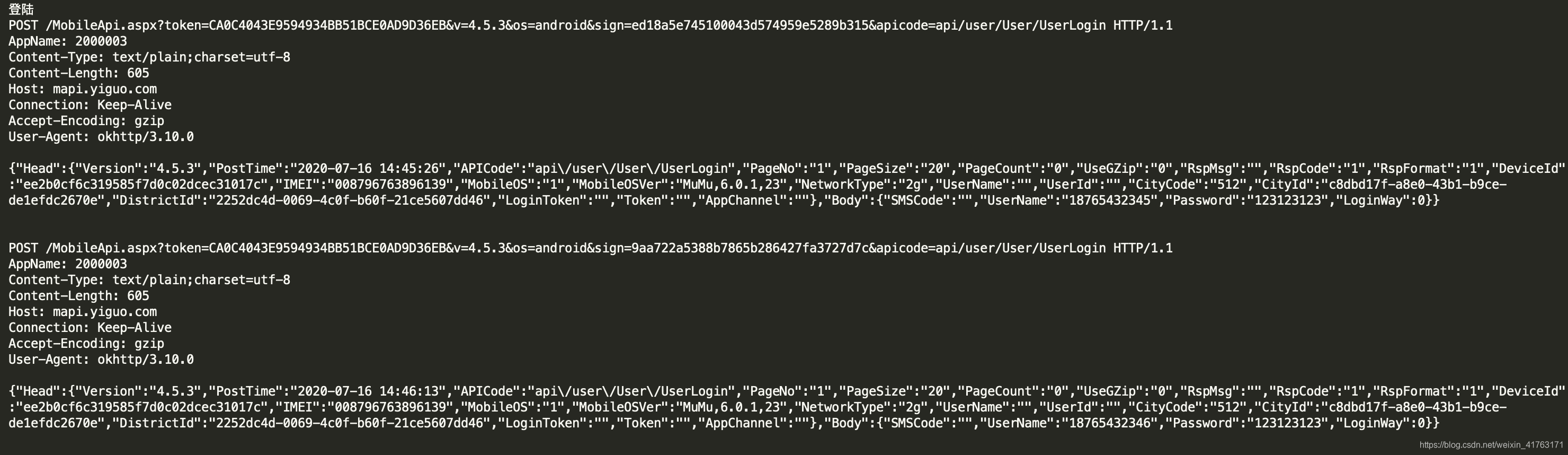
登陆页,2次
通过抓包可以知道,这次还是sign,至于post请求的参数,估计多半也是生成sign的部分。
2.反编译,这次依然没有加固
按照之前的搜索方式“sign ,找半天啥也没找到,都是些没用的,毕竟还有混淆,这次换个搜索方式,用URL的部分去搜索,找到了这么个玩意:
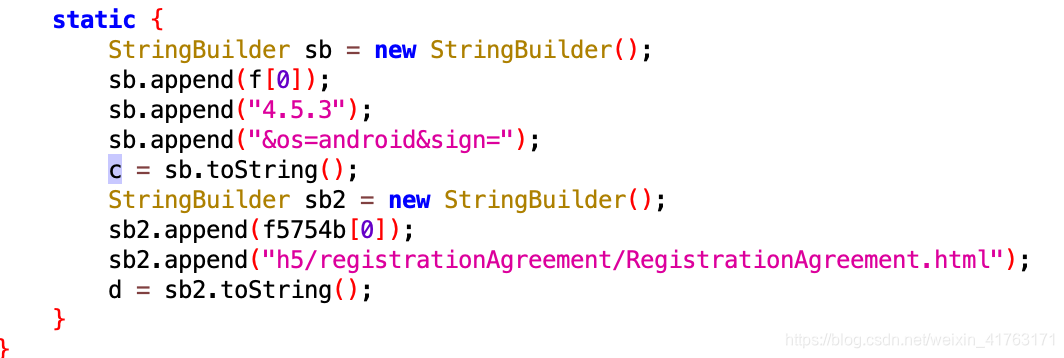
这个就是我们访问链接中的一部分,c肯定就是我们后面访问链接中的一部分组成,会在生成链接的时候被调用的,然后直接看c是在哪调用的,这样就进入了com.yiguo.entity.Session这个类
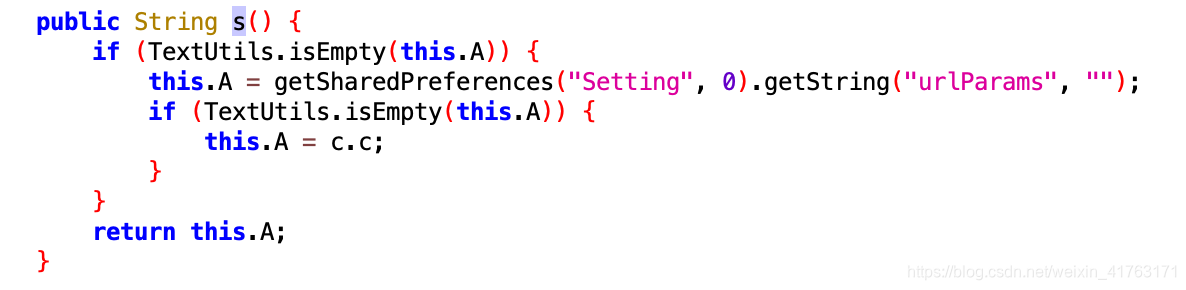
好了,开启frida打印这个s来进行分析,图不贴了,总之打印的就是链接和请求头,继续找这个s在哪被用的,我们通过查找用例找到了这个地方:
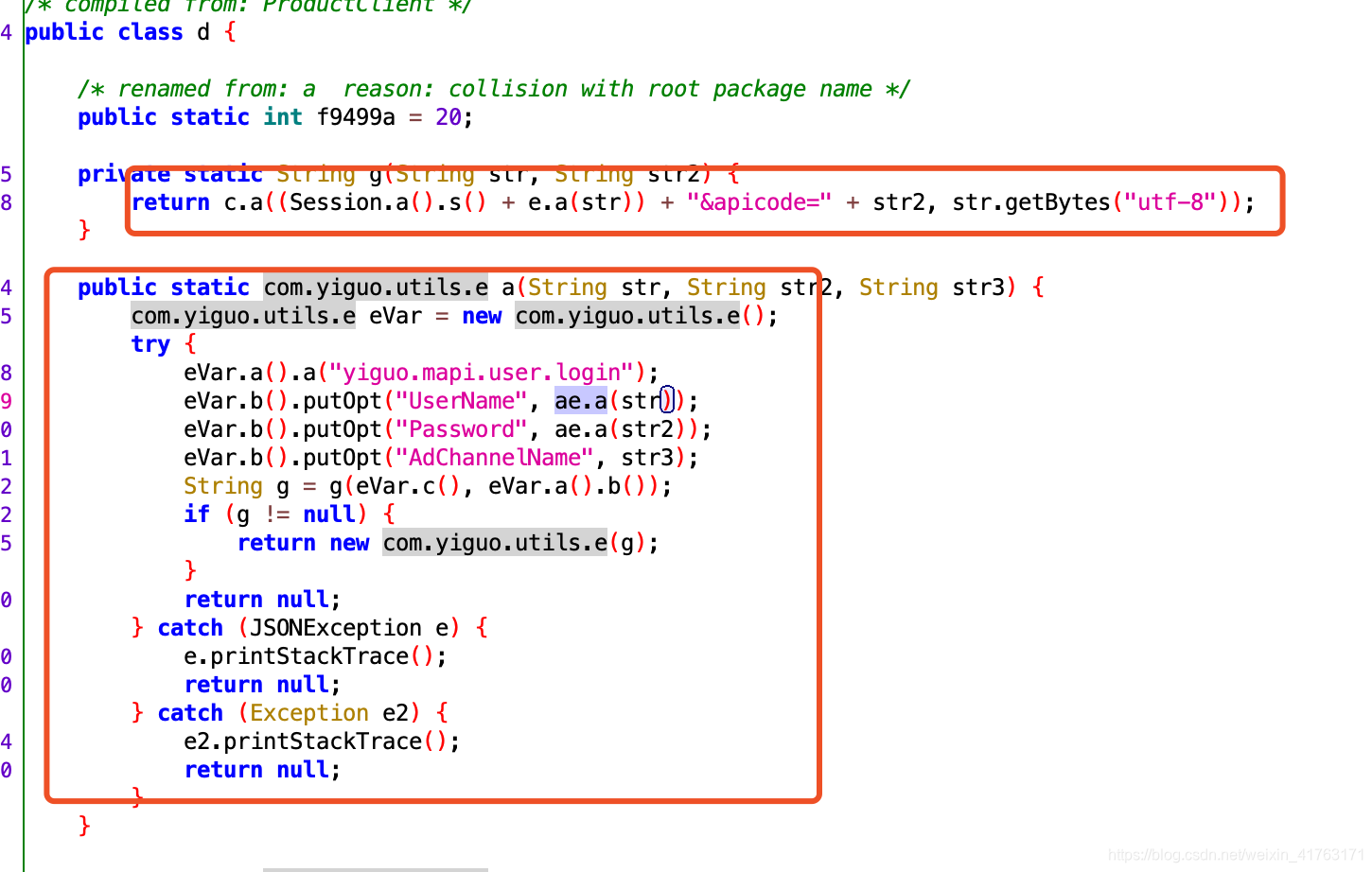
上面的是调用部分,我们继续分析一下,前面是固定的url前半部分,后面是sign的值以及后面的参数,这个时候我们就可以跟进这个e.a(str)方法了,继续找,跳到声明:
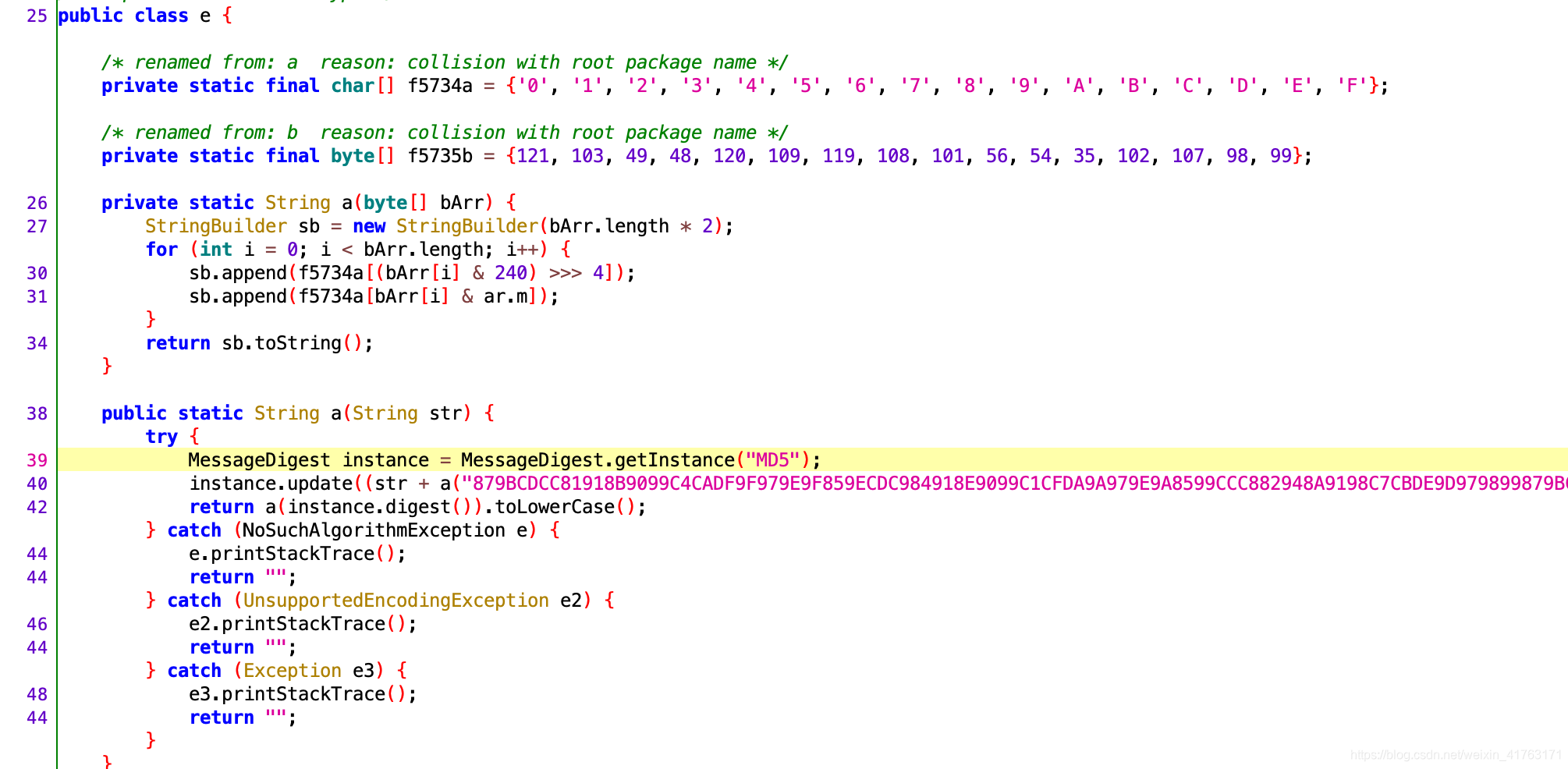
我们打印一下这个a方法,看看是啥:
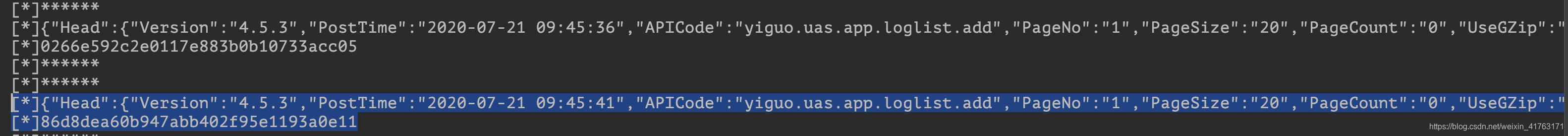
可以看到上面就是传入的参数,下面是一个md5的返回值,继续分析,这个里面的a是传入了两个参数,然后再和传入的str拼接起来生成了之前a方法传入的str,我们这里直接可以打印看是什么
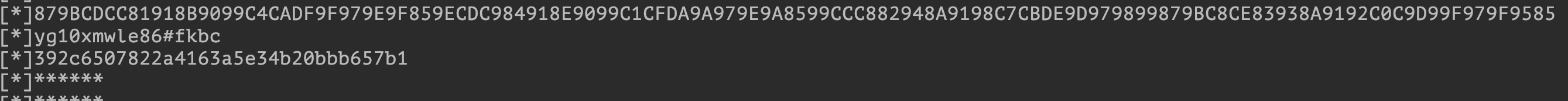
第一串就是上面明文的那一串,然后第二串也是a(str1,str2)返回的固定值,于是第三个参数也是固定的了,那么最终的参数就是原本的那一长串请求头,加上后面的固定值,再md5即可。
第一串:{"Head":{"Version":"4.5.3","PostTime":"2020-07-21 10:22:42","APICode":"yiguo.uas.app.loglist.add","PageNo":"1","PageSize":"20","PageCount":"0","UseGZip":"1","RspMsg":"","RspCode":"1","RspFormat":"1","DeviceId":"ee2b0cf6c319585f7d0c02dcec31017c","IMEI":"008796763896139","MobileOS":"1","MobileOSVer":"MuMu,6.0.1,23","NetworkType":"2g","UserName":"","UserId":"","CityCode":"512","CityId":"c8dbd17f-a8e0-43b1-b9ce-de1efdc2670e","DistrictId":"2252dc4d-0069-4c0f-b60f-21ce5607dd46","LoginToken":"","Token":"","AppChannel":""},"Body":{"city":"广州","ygm_project_id":"2000001","app_channel":"","ygm_actions":[{"posttime":"2020-07-21 10:22:39","ygm_action_type":"0","ygm_action_page":"page.search","ygm_action_code":"ygm.search.view","ygm_action_referrer":"page.category.result","ygm_action_referrer_tag":"","ygm_action_tag":"","ygm_action_commdity_id":"","ygm_action_group":"","screen_width":"900","screen_height":"1440","ygm_action_component_id":"","ygm_action_coupon_code":"","ygm_action_category_id":"","ygm_action_tab_id":"","ygm_action_url":"","ygm_activity_id":"","ygm_action_ad_id":"","ygm_action_promotioninfo_id":"","ygm_action_category_highid":"","ygm_page_id":"","referrer":"","ext_1":"","ext_2":"","ext_3":"","ext_4":"","ext_5":"","ext_6":"","ext_7":"","ext_8":"","keyword":""},{"posttime":"2020-07-21 10:22:40","ygm_action_type":"1","ygm_action_page":"ygm.search.home","ygm_action_code":"ygm.search.home.history.click","ygm_action_referrer":"","ygm_action_referrer_tag":"","ygm_action_tag":"牛排","ygm_action_commdity_id":"","ygm_action_group":"","screen_width":"900","screen_height":"1440","ygm_action_component_id":"","ygm_action_coupon_code":"","ygm_action_category_id":"","ygm_action_tab_id":"","ygm_action_url":"","ygm_activity_id":"","ygm_action_ad_id":"","ygm_action_promotioninfo_id":"","ygm_action_category_highid":"","ygm_page_id":"","referrer":"","ext_1":"","ext_2":"","ext_3":"","ext_4":"","ext_5":"","ext_6":"","ext_7":"","ext_8":"","keyword":""}]}}
第二串:392c6507822a4163a5e34b20bbb657b1
我们在线md5看看
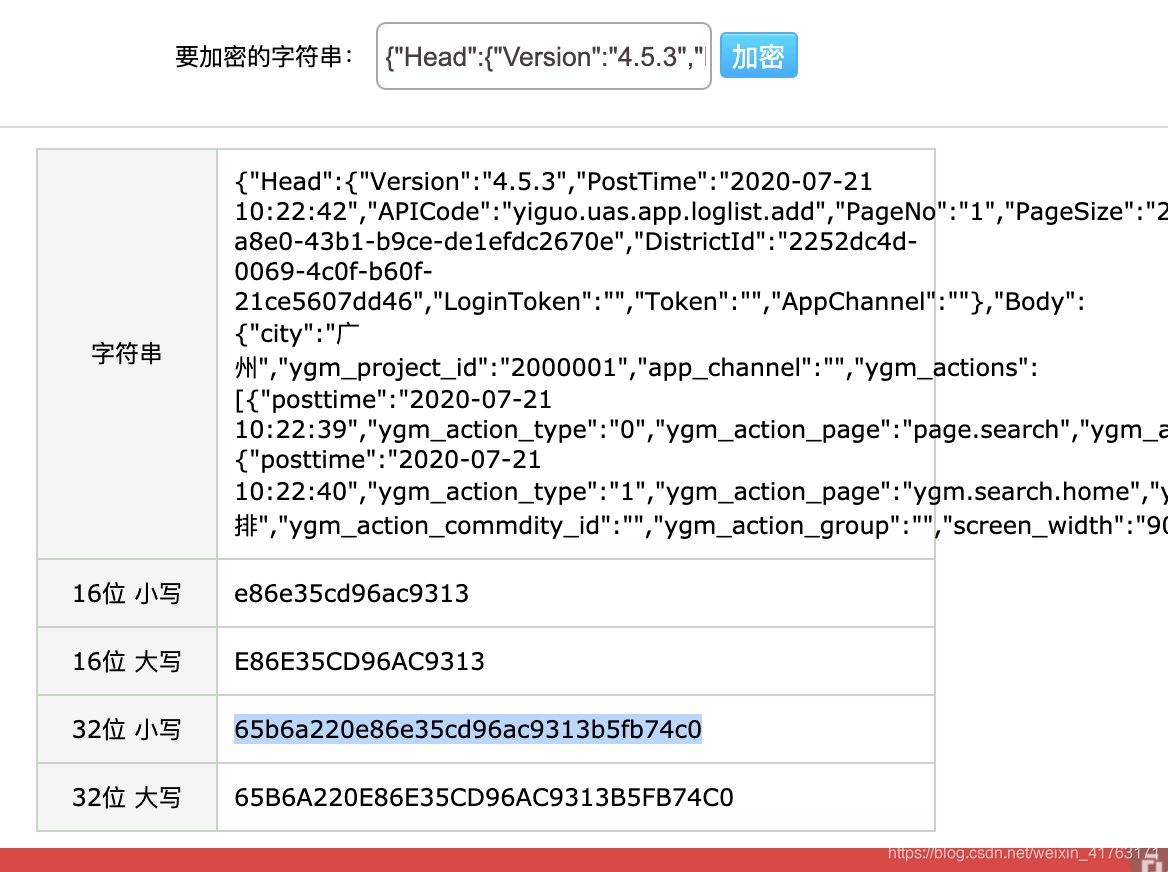
现在就可以自己构造咯~懒得弄的话主动调用也可以。
之前的分析就这样了,现在是想把这个APP可以实现自动调用sign做rpc,选择用平头哥+sekiro
先抓包分析一下搜索结果:
post请求,携带的参数是:
{"Head":{"Version":"4.5.4","PostTime":"2021-03-05 10:25:07","APICode":"api\/commodityapi\/Commodity\/GetSearchList","PageNo":"1","PageSize":"20","PageCount":"0","UseGZip":"0","RspMsg":"","RspCode":"1","RspFormat":"1","DeviceId":"4095a30e9d073564c09487a3f24a2364","IMEI":"","MobileOS":"1","MobileOSVer":"MI 9 SE,10,29","NetworkType":"2g","UserName":"","UserId":"","CityCode":"16","CityId":"3a5c6df3-9ca1-41a8-bc9c-453050bb7897","DistrictId":"e6675810-bcb5-4bc7-80f3-c353b2f1ee41","LoginToken":"","Token":"","AppChannel":"ali_store"},"Body":{"Keyword":"苹果","PageIndex":1,"Sort":0}}
第二次:
https://mapi.yiguo.com/MobileApi.aspx?token=CA0C4043E9594934BB51BCE0AD9D36EB&v=4.5.4&os=android&sign=0d976d36d87a760da44cdbe447977d4e&apicode=api/commodityapi/Commodity/GetSearchList
{"Head":{"Version":"4.5.4","PostTime":"2021-03-05 10:21:14","APICode":"api\/commodityapi\/Commodity\/GetSearchList","PageNo":"1","PageSize":"20","PageCount":"0","UseGZip":"0","RspMsg":"","RspCode":"1","RspFormat":"1","DeviceId":"4095a30e9d073564c09487a3f24a2364","IMEI":"","MobileOS":"1","MobileOSVer":"MI 9 SE,10,29","NetworkType":"2g","UserName":"","UserId":"","CityCode":"16","CityId":"3a5c6df3-9ca1-41a8-bc9c-453050bb7897","DistrictId":"e6675810-bcb5-4bc7-80f3-c353b2f1ee41","LoginToken":"","Token":"","AppChannel":"ali_store"},"Body":{"Keyword":"牛肉","PageIndex":1,"Sort":0}}
对比之后,可以发现还是sign的加密参数。
那就继续hook这个类:com.yglibary.a.e 使用objection发现就是这个类的a方法,看到整个流程就是固定传入2个写死的参数,拼接上下面这一串:
{"Head":{"Version":"4.5.4","PostTime":"2021-03-05 11:13:37","APICode":"api\/commodityapi\/Commodity\/GetSearchList","PageNo":"1","PageSize":"20","PageCount":"0","UseGZip":"0","RspMsg":"","RspCode":"1","RspFormat":"1","DeviceId":"4095a30e9d073564c09487a3f24a2364","IMEI":"","MobileOS":"1","MobileOSVer":"MI 9 SE,10,29","NetworkType":"2g","UserName":"","UserId":"","CityCode":"16","CityId":"3a5c6df3-9ca1-41a8-bc9c-453050bb7897","DistrictId":"e6675810-bcb5-4bc7-80f3-c353b2f1ee41","LoginToken":"","Token":"","AppChannel":"ali_store"},"Body":{"Keyword":"牛肉","PageIndex":1,"Sort":0}}
然后进行MD5,再调用a(),那么我们只要改动上面这一串里面的关键字和时间等就可以开始调用这个方法了
按说是应该先用frdia来确认一下是否能调用的,但是不管了直接干。开始我写
![]()
来直接调用发现不成功,然后观察得知这个是静态方法,但是:
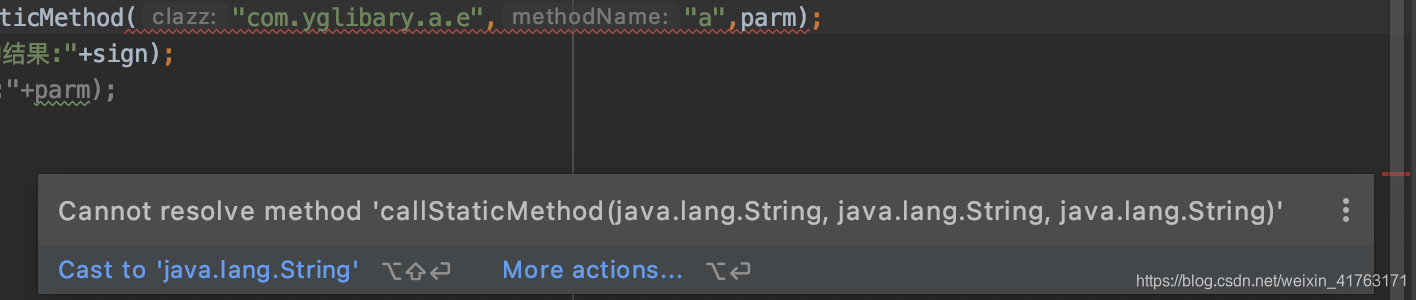
这里报错了,也就是说这个地方要传递的不是类名,而是一个类才可以,于是就要先找到这个类:
Class<?> temp_c = RposedHelpers.findClass("com.yglibary.a.e",lpparam.classLoader);然后再传递temp_c进去
String sign = (String) RposedHelpers.callStaticMethod(temp_c,"a",new_parm);这样才能调用成功,不然就会报找不到这个方法,最后整个的写法是:
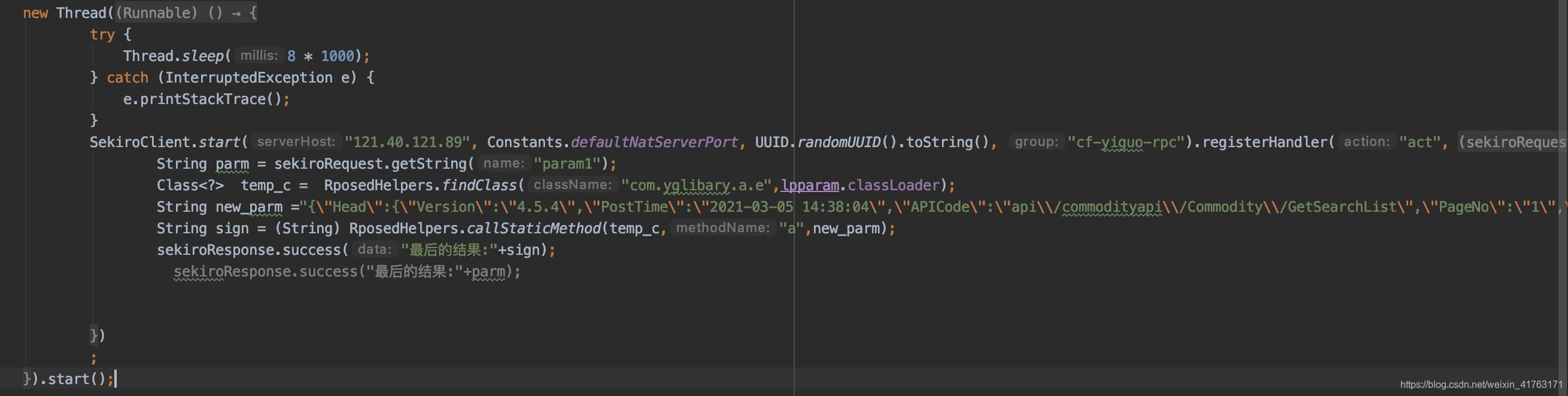
就能直接调用加密方法了,效果如下:
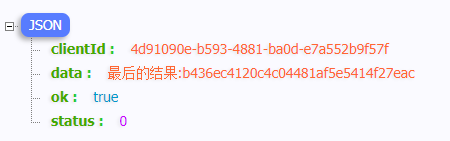
但是这种简单的加密参数还真是简单,难得确实很难。。。下一篇我要用这个app内部自己发送请求的方法来直接获取返回的结果