1、X.509简介
X.509是密码学里公钥证书的格式标准。X.509证书已应用在包括TLS/SSL在内的众多网络协议里,同时它也用在很多非在线应用场景里,比如电子签名服务。X.509证书里含有公钥、身份信息(比如网络主机名,组织的名称或个体名称等)和签名信息(可以是证书签发机构CA的签名,也可以是自签名)。
X.509还附带了证书吊销列表和用于从最终对证书进行签名的证书签发机构直到最终可信点为止的证书合法性验证算法。X.509是ITU-T标准化部门基于他们之前的ASN.1定义的一套证书标准。
2、证书组成结构
证书组成结构标准用ASN.1(一种标准的语言)来进行描述. X.509 v3 数字证书结构如下:
证书
版本号
序列号
签名算法
颁发者
证书有效期
此日期前无效
此日期后无效
主题
主题公钥信息
公钥算法
主题公钥
颁发者唯一身份信息(可选项)
主题唯一身份信息(可选项)
扩展信息(可选项)
...
证书签名算法
数字签名
3、证书文件扩展名
X.509有多种常用的扩展名。不过其中的一些还用于其它用途,就是说具有这个扩展名的文件可能并不是证书,比如说可能只是保存了私钥。
- .pem– 隐私增强型电子邮件格式,通常是Base64格式的。
- .cer, .crt, .der– 通常是DER二进制格式的。
- .p7b, .p7c– PKCS#7 SignedData structure without data, just certificate(s) or CRL(s)
- .p12– PKCS#12格式,包含证书的同时可能还包含私钥
- .pfx– PFX,PKCS#12之前的格式(通常用PKCS#12格式,比如由互聯網資訊服務产生的PFX文件)
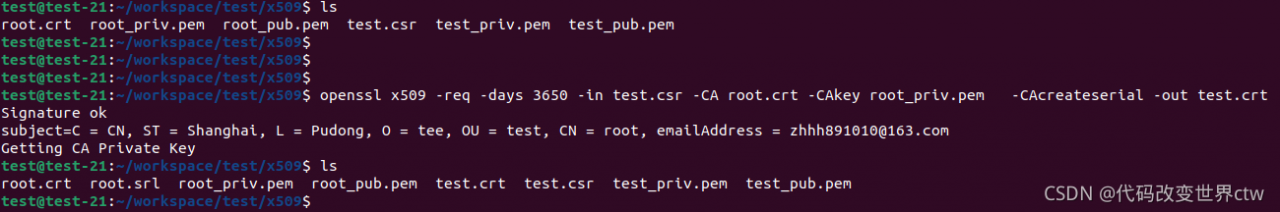
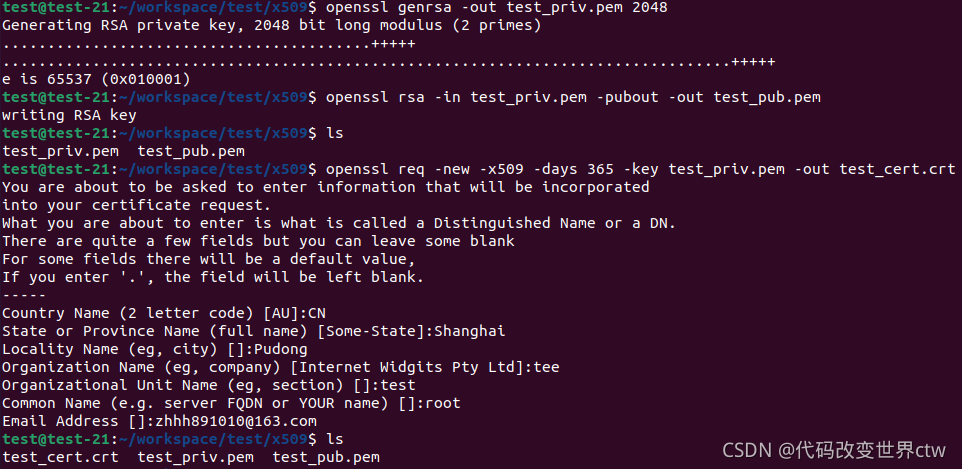
4、生成一个自签名证书的示例
(1)、生成RSA私钥 :openssl genrsa -out test_priv.pem 2048
(2)、从RSA私钥中提取公钥 : openssl rsa -in test_priv.pem -pubout -out test_pub.pem
(3)、生成自签名证书 : openssl req -new -x509 -days 365 -key test_priv.pem -out test_cert.crt
test@test-21:~/workspace/test/x509$ openssl rsa -in test_priv.pem -pubout -out test_pub.pem
writing RSA key
test@test-21:~/workspace/test/x509$ ls
test_priv.pem test_pub.pem
test@test-21:~/workspace/test/x509$openssl req -new -x509 -days 365 -key test_priv.pem -out test_cert.crt
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:Shanghai
Locality Name (eg, city) []:Pudong
Organization Name (eg, company) [Internet Widgits Pty Ltd]:tee
Organizational Unit Name (eg, section) []:testtest
Common Name (e.g. server FQDN or YOUR name) []:root
Email Address []:zhhh891010@163.com
test@test-21:~/workspace/test/x509$
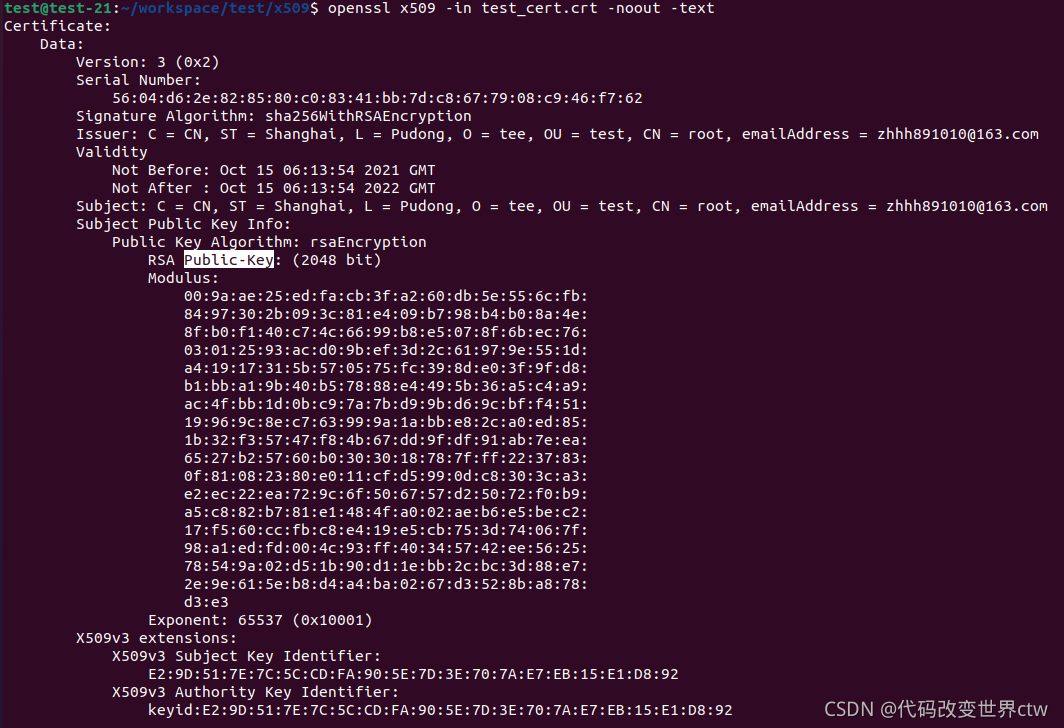
(4)、查看证书 :openssl x509 -in test_cert.crt -noout -text
test@test-21:~/workspace/test/x509$ openssl x509 -in test_cert.crt -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
56:04:d6:2e:82:85:80:c0:83:41:bb:7d:c8:67:79:08:c9:46:f7:62
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = Shanghai, L = Pudong, O = tee, OU = test, CN = root, emailAddress = zhhh891010@163.com
Validity
Not Before: Oct 15 06:13:54 2021 GMT
Not After : Oct 15 06:13:54 2022 GMT
Subject: C = CN, ST = Shanghai, L = Pudong, O = tee, OU = test, CN = root, emailAddress = zhhh891010@163.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:9a:ae:25:ed:fa:cb:3f:a2:60:db:5e:55:6c:fb:
84:97:30:2b:09:3c:81:e4:09:b7:98:b4:b0:8a:4e:
8f:b0:f1:40:c7:4c:66:99:b8:e5:07:8f:6b:ec:76:
03:01:25:93:ac:d0:9b:ef:3d:2c:61:97:9e:55:1d:
a4:19:17:31:5b:57:05:75:fc:39:8d:e0:3f:9f:d8:
b1:bb:a1:9b:40:b5:78:88:e4:49:5b:36:a5:c4:a9:
ac:4f:bb:1d:0b:c9:7a:7b:d9:9b:d6:9c:bf:f4:51:
19:96:9c:8e:c7:63:99:9a:1a:bb:e8:2c:a0:ed:85:
1b:32:f3:57:47:f8:4b:67:dd:9f:df:91:ab:7e:ea:
65:27:b2:57:60:b0:30:30:18:78:7f:ff:22:37:83:
0f:81:08:23:80:e0:11:cf:d5:99:0d:c8:30:3c:a3:
e2:ec:22:ea:72:9c:6f:50:67:57:d2:50:72:f0:b9:
a5:c8:82:b7:81:e1:48:4f:a0:02:ae:b6:e5:be:c2:
17:f5:60:cc:fb:c8:e4:19:e5:cb:75:3d:74:06:7f:
98:a1:ed:fd:00:4c:93:ff:40:34:57:42:ee:56:25:
78:54:9a:02:d5:1b:90:d1:1e:bb:2c:bc:3d:88:e7:
2e:9e:61:5e:b8:d4:a4:ba:02:67:d3:52:8b:a8:78:
d3:e3
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
E2:9D:51:7E:7C:5C:CD:FA:90:5E:7D:3E:70:7A:E7:EB:15:E1:D8:92
X509v3 Authority Key Identifier:
keyid:E2:9D:51:7E:7C:5C:CD:FA:90:5E:7D:3E:70:7A:E7:EB:15:E1:D8:92
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
7a:65:b2:ff:52:10:92:b5:d8:d1:13:61:e7:4c:4b:b7:8e:02:
fe:22:93:cf:9c:c9:bf:b6:cc:04:e2:d7:eb:51:59:9c:b6:1b:
e2:eb:5a:19:b8:bf:87:01:2f:f5:c1:5b:2c:e9:0c:e4:c9:b4:
ff:5b:54:98:e6:c1:06:09:3d:5a:6c:ec:a3:03:5b:d2:7e:e0:
32:c2:2e:de:42:95:5e:57:3f:1c:a3:67:44:8b:61:e2:21:88:
4a:1a:86:bb:ed:5b:46:8f:87:4e:f6:d4:f6:ff:7a:b2:c1:62:
b4:33:ff:05:18:10:5a:4f:12:89:ff:8a:cc:3e:57:69:9f:81:
3a:e3:17:d1:30:f0:b0:33:d3:ce:49:c1:d1:b6:a0:98:9c:7f:
8b:8a:b1:e4:0e:5e:a0:13:6d:c9:48:44:8f:4c:6c:63:34:a2:
9d:7b:c1:dd:0f:27:5f:8f:5b:08:46:46:c9:25:77:6a:62:dc:
ff:bf:ac:77:db:be:4c:6a:2f:51:6d:a9:1a:62:9d:3c:bf:51:
63:8d:15:32:88:c0:68:a2:f5:13:b8:60:99:58:6e:b8:c8:2b:
95:d8:cf:d1:71:6a:14:8c:98:4a:03:e6:f6:89:18:4d:70:87:
b6:05:ae:13:8b:88:b1:31:04:90:c9:92:6b:11:be:6d:4d:bc:
71:ac:5a:ee
test@test-21:~/workspace/test/x509$
5、生成签名请求及CA 签名
在上一节中RSA 2048的密钥对已经生成(test_priv.pem test_pub.pem)![]()
(1)、使用 RSA私钥生成 CSR 签名请求 : openssl req -new -key test_priv.pem -out test.csr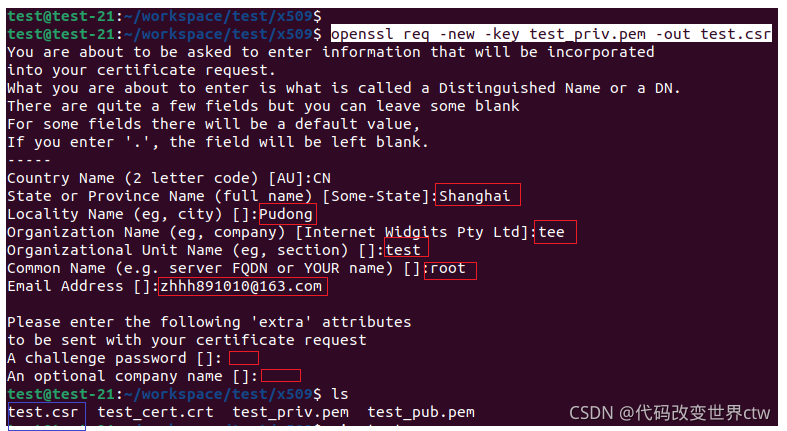
(2)、查看这个CSR 文件 :openssl req -noout -text -in test.csr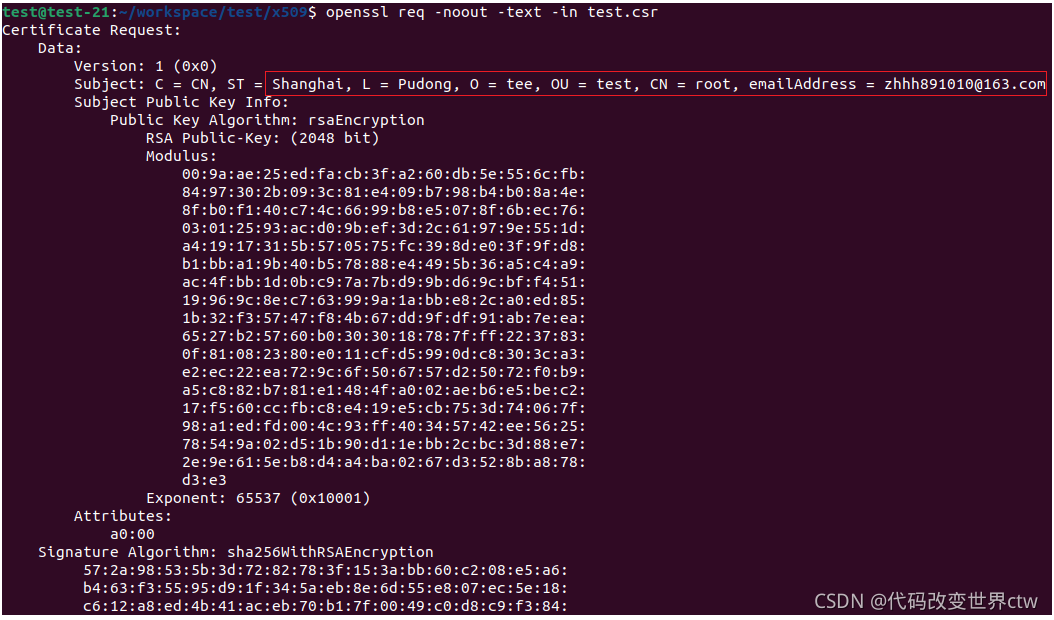
(3)、用“生成自签名证书的方法,生成CA证书”
(4)、使用 CA 证书及CA密钥 对请求签发证书进行签发,生成 x509证书 openssl x509 -req -days 3650 -in test.csr -CA root.crt -CAkey root_priv.pem -CAcreateserial -out test.crt