目录
最近一直在研究OIDC、Oauth、SSO等与用户登录、认证、授权相关的知识,
所以需要快速搭建一个支持通用协议(OIDC、OAUTH…)的统一认证中心,
故在流行的开源免费SSO(single sign-on,单点登录)软件(如IdentityServer、Keycloak、CAS...)中选择了Jboss出品的Keycloak,
Keyclok基于OIDC, Oauth2.0, SAML2协议,并且提供SSO能力,其主要由Java编写(web界面由JS、HTML编写),
具体源码可参见:https://github.com/keycloak/keycloak
接下来介绍如何快速安装、启动Keycloak。
下载启动包keycloak-15.0.2.zip
下载keycloak-15.0.2.zip后解压,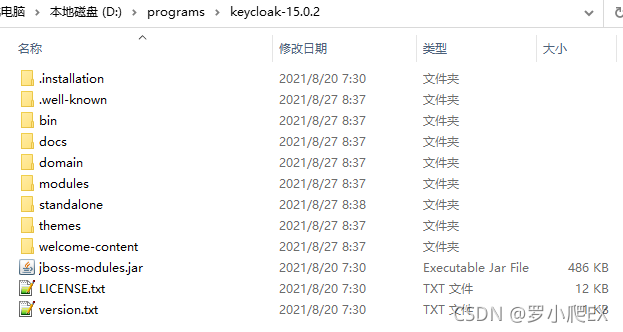
启动keycloak
Linux执行:
bin/standalone.sh
Windows执行:
bin/standalone.bat
启动日志
Calling "D:\programs\keycloak-15.0.2\bin\standalone.conf.bat"
Setting JAVA property to "D:\programs\Java\jdk1.8.0_192\bin\java"
===============================================================================
JBoss Bootstrap Environment
JBOSS_HOME: "D:\programs\keycloak-15.0.2"
JAVA: "D:\programs\Java\jdk1.8.0_192\bin\java"
JAVA_OPTS: "-Dprogram.name=standalone.bat -Xms64M -Xmx512M -XX:MetaspaceSize=96M -XX:MaxMetaspaceSize=256m -Djava.net.preferIPv4Stack=true -Djboss.modules.system.pkgs=org.jboss.byteman -Djava.awt.headless=true "
===============================================================================
08:38:09,720 INFO [org.jboss.modules] (main) JBoss Modules version 1.11.0.Final
08:38:10,272 INFO [org.jboss.msc] (main) JBoss MSC version 1.4.12.Final
08:38:10,280 INFO [org.jboss.threads] (main) JBoss Threads version 2.4.0.Final
08:38:10,378 INFO [org.jboss.as] (MSC service thread 1-1) WFLYSRV0049: Keycloak 15.0.2 (WildFly Core 15.0.1.Final) starting
08:38:10,900 INFO [org.wildfly.security] (ServerService Thread Pool -- 20) ELY00001: WildFly Elytron version 1.15.3.Final
08:38:11,129 INFO [org.jboss.as.controller.management-deprecated] (ServerService Thread Pool -- 22) WFLYCTL0033: Extension 'security' is deprecated and may not be supported in future versions
08:38:11,281 INFO [org.jboss.as.controller.management-deprecated] (Controller Boot Thread) WFLYCTL0028: Attribute 'security-realm' in the resource at address '/core-service=management/management-interface=http-interface' is deprecated, and may be removed in a future version. See the attribute description in the output of the read-resource-description operation to learn more about the deprecation.
08:38:11,295 INFO [org.jboss.as.controller.management-deprecated] (ServerService Thread Pool -- 25) WFLYCTL0028: Attribute 'security-realm' in the resource at address '/subsystem=undertow/server=default-server/https-listener=https' is deprecated, and may be removed in a future version. See the attribute description in the output of the read-resource-description operation to learn more about the deprecation.
08:38:11,370 INFO [org.jboss.as.server] (Controller Boot Thread) WFLYSRV0039: Creating http management service using socket-binding (management-http)
08:38:11,383 INFO [org.xnio] (MSC service thread 1-4) XNIO version 3.8.4.Final
08:38:11,393 INFO [org.xnio.nio] (MSC service thread 1-4) XNIO NIO Implementation Version 3.8.4.Final
08:38:11,415 INFO [org.wildfly.extension.health] (ServerService Thread Pool -- 36) WFLYHEALTH0001: Activating Base Health Subsystem
08:38:11,438 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 37) WFLYCLINF0001: Activating Infinispan subsystem.
08:38:11,455 INFO [org.wildfly.extension.io] (ServerService Thread Pool -- 38) WFLYIO001: Worker 'default' has auto-configured to 12 IO threads with 96 max task threads based on your 6 available processors
08:38:11,457 WARN [org.jboss.as.txn] (ServerService Thread Pool -- 51) WFLYTX0013: The node-identifier attribute on the /subsystem=transactions is set to the default value. This is a danger for environments running multiple servers. Please make sure the attribute value is unique.
08:38:11,480 INFO [org.jboss.as.naming] (ServerService Thread Pool -- 46) WFLYNAM0001: Activating Naming Subsystem
08:38:11,485 INFO [org.jboss.as.jaxrs] (ServerService Thread Pool -- 39) WFLYRS0016: RESTEasy version 3.15.1.Final
08:38:11,494 INFO [org.jboss.as.security] (ServerService Thread Pool -- 49) WFLYSEC0002: Activating Security Subsystem
08:38:11,500 INFO [org.wildfly.extension.metrics] (ServerService Thread Pool -- 45) WFLYMETRICS0001: Activating Base Metrics Subsystem
08:38:11,510 WARN [org.wildfly.extension.elytron] (MSC service thread 1-7) WFLYELY00023: KeyStore file 'D:\programs\keycloak-15.0.2\standalone\configuration\application.keystore' does not exist. Used blank.
08:38:11,527 INFO [org.jboss.as.security] (MSC service thread 1-3) WFLYSEC0001: Current PicketBox version=5.0.3.Final-redhat-00007
08:38:11,540 INFO [org.jboss.as.connector] (MSC service thread 1-4) WFLYJCA0009: Starting Jakarta Connectors Subsystem (WildFly/IronJacamar 1.4.27.Final)
08:38:11,578 INFO [org.jboss.as.connector.subsystems.datasources] (ServerService Thread Pool -- 31) WFLYJCA0004: Deploying JDBC-compliant driver class org.h2.Driver (version 1.4)
08:38:11,601 INFO [org.wildfly.extension.undertow] (MSC service thread 1-7) WFLYUT0003: Undertow 2.2.5.Final starting
08:38:11,603 WARN [org.wildfly.extension.elytron] (MSC service thread 1-7) WFLYELY01084: KeyStore D:\programs\keycloak-15.0.2\standalone\configuration\application.keystore not found, it will be auto generated on first use with a self-signed certificate for host localhost
08:38:11,620 INFO [org.jboss.remoting] (MSC service thread 1-8) JBoss Remoting version 5.0.20.Final
08:38:11,628 INFO [org.jboss.as.connector.deployers.jdbc] (MSC service thread 1-4) WFLYJCA0018: Started Driver service with driver-name = h2
08:38:11,629 WARN [org.wildfly.clustering.web.undertow] (ServerService Thread Pool -- 52) WFLYCLWEBUT0007: No routing provider found for default-server; using legacy provider based on static configuration
08:38:11,660 INFO [org.jboss.as.naming] (MSC service thread 1-8) WFLYNAM0003: Starting Naming Service
08:38:11,685 INFO [org.jboss.as.mail.extension] (MSC service thread 1-6) WFLYMAIL0001: Bound mail session [java:jboss/mail/Default]
08:38:11,698 INFO [org.jboss.as.ejb3] (MSC service thread 1-8) WFLYEJB0482: Strict pool mdb-strict-max-pool is using a max instance size of 24 (per class), which is derived from the number of CPUs on this host.
08:38:11,699 INFO [org.jboss.as.ejb3] (MSC service thread 1-7) WFLYEJB0481: Strict pool slsb-strict-max-pool is using a max instance size of 96 (per class), which is derived from thread worker pool sizing.
08:38:11,716 INFO [org.wildfly.extension.undertow] (ServerService Thread Pool -- 52) WFLYUT0014: Creating file handler for path 'D:\programs\keycloak-15.0.2/welcome-content' with options [directory-listing: 'false', follow-symlink: 'false', case-sensitive: 'true', safe-symlink-paths: '[]']
08:38:11,813 INFO [org.wildfly.extension.undertow] (MSC service thread 1-8) WFLYUT0012: Started server default-server.
08:38:11,816 INFO [org.wildfly.extension.undertow] (MSC service thread 1-7) Queuing requests.
08:38:11,824 INFO [org.wildfly.extension.undertow] (MSC service thread 1-7) WFLYUT0018: Host default-host starting
08:38:11,850 INFO [org.jboss.as.patching] (MSC service thread 1-8) WFLYPAT0050: Keycloak cumulative patch ID is: base, one-off patches include: none
08:38:11,862 WARN [org.jboss.as.domain.management.security] (MSC service thread 1-3) WFLYDM0111: Keystore D:\programs\keycloak-15.0.2\standalone\configuration\application.keystore not found, it will be auto generated on first use with a self signed certificate for host localhost
08:38:11,864 INFO [org.jboss.as.server.deployment.scanner] (MSC service thread 1-2) WFLYDS0013: Started FileSystemDeploymentService for directory D:\programs\keycloak-15.0.2\standalone\deployments
08:38:11,870 INFO [org.jboss.as.server.deployment] (MSC service thread 1-7) WFLYSRV0027: Starting deployment of "keycloak-server.war" (runtime-name: "keycloak-server.war")
08:38:11,956 INFO [org.wildfly.extension.undertow] (MSC service thread 1-7) WFLYUT0006: Undertow HTTP listener default listening on 127.0.0.1:8080
08:38:12,029 INFO [org.jboss.as.ejb3] (MSC service thread 1-7) WFLYEJB0493: Jakarta Enterprise Beans subsystem suspension complete
08:38:12,081 INFO [org.jboss.as.connector.subsystems.datasources] (MSC service thread 1-5) WFLYJCA0001: Bound data source [java:jboss/datasources/KeycloakDS]
08:38:12,081 INFO [org.jboss.as.connector.subsystems.datasources] (MSC service thread 1-2) WFLYJCA0001: Bound data source [java:jboss/datasources/ExampleDS]
08:38:12,270 INFO [org.wildfly.extension.undertow] (MSC service thread 1-2) WFLYUT0006: Undertow HTTPS listener https listening on 127.0.0.1:8443
08:38:12,539 INFO [org.infinispan.CONTAINER] (ServerService Thread Pool -- 54) ISPN000128: Infinispan version: Infinispan 'Corona Extra' 11.0.9.Final
08:38:12,567 INFO [org.infinispan.CONFIG] (MSC service thread 1-5) ISPN000152: Passivation configured without an eviction policy being selected. Only manually evicted entities will be passivated.
08:38:12,568 INFO [org.infinispan.CONFIG] (MSC service thread 1-5) ISPN000152: Passivation configured without an eviction policy being selected. Only manually evicted entities will be passivated.
08:38:12,619 INFO [org.infinispan.PERSISTENCE] (ServerService Thread Pool -- 54) ISPN000556: Starting user marshaller 'org.wildfly.clustering.infinispan.spi.marshalling.InfinispanProtoStreamMarshaller'
08:38:12,619 INFO [org.infinispan.PERSISTENCE] (ServerService Thread Pool -- 55) ISPN000556: Starting user marshaller 'org.wildfly.clustering.infinispan.marshalling.jboss.JBossMarshaller'
08:38:12,788 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 54) WFLYCLINF0002: Started http-remoting-connector cache from ejb container
08:38:12,802 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 66) WFLYCLINF0002: Started offlineClientSessions cache from keycloak container
08:38:12,803 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 56) WFLYCLINF0002: Started offlineSessions cache from keycloak container
08:38:12,803 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 62) WFLYCLINF0002: Started authenticationSessions cache from keycloak container
08:38:12,804 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 59) WFLYCLINF0002: Started actionTokens cache from keycloak container
08:38:12,805 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 57) WFLYCLINF0002: Started work cache from keycloak container
08:38:12,802 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 58) WFLYCLINF0002: Started loginFailures cache from keycloak container
08:38:12,804 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 64) WFLYCLINF0002: Started sessions cache from keycloak container
08:38:12,803 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 63) WFLYCLINF0002: Started clientSessions cache from keycloak container
08:38:12,825 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 54) WFLYCLINF0002: Started realms cache from keycloak container
08:38:12,825 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 61) WFLYCLINF0002: Started users cache from keycloak container
08:38:12,825 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 60) WFLYCLINF0002: Started keys cache from keycloak container
08:38:12,827 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 55) WFLYCLINF0002: Started authorization cache from keycloak container
08:38:12,901 WARN [org.jboss.as.server.deployment] (MSC service thread 1-4) WFLYSRV0273: Excluded subsystem webservices via jboss-deployment-structure.xml does not exist.
08:38:13,305 INFO [org.keycloak.services] (ServerService Thread Pool -- 55) KC-SERVICES0001: Loading config from standalone.xml or domain.xml
08:38:13,454 INFO [org.keycloak.url.DefaultHostnameProviderFactory] (ServerService Thread Pool -- 55) Frontend: <request>, Admin: <frontend>, Backend: <request>
08:38:13,691 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 55) WFLYCLINF0002: Started realmRevisions cache from keycloak container
08:38:13,696 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 55) WFLYCLINF0002: Started userRevisions cache from keycloak container
08:38:13,702 INFO [org.jboss.as.clustering.infinispan] (ServerService Thread Pool -- 55) WFLYCLINF0002: Started authorizationRevisions cache from keycloak container
08:38:13,703 INFO [org.keycloak.connections.infinispan.DefaultInfinispanConnectionProviderFactory] (ServerService Thread Pool -- 55) Node name: luohq-1, Site name: null
08:38:14,560 INFO [org.keycloak.connections.jpa.DefaultJpaConnectionProviderFactory] (ServerService Thread Pool -- 55) Database info: {databaseUrl=jdbc:h2:D:\programs\keycloak-15.0.2\standalone\data/keycloak, databaseUser=SA, databaseProduct=H2 1.4.197 (2018-03-18), databaseDriver=H2 JDBC Driver 1.4.197 (2018-03-18)}
08:38:15,685 INFO [org.keycloak.connections.jpa.updater.liquibase.LiquibaseJpaUpdaterProvider] (ServerService Thread Pool -- 55) Initializing database schema. Using changelog META-INF/jpa-changelog-master.xml
08:38:16,755 INFO [org.hibernate.jpa.internal.util.LogHelper] (ServerService Thread Pool -- 55) HHH000204: Processing PersistenceUnitInfo [
name: keycloak-default
...]
08:38:16,798 INFO [org.hibernate.Version] (ServerService Thread Pool -- 55) HHH000412: Hibernate Core {5.3.20.Final}
08:38:16,799 INFO [org.hibernate.cfg.Environment] (ServerService Thread Pool -- 55) HHH000206: hibernate.properties not found
08:38:16,896 INFO [org.hibernate.annotations.common.Version] (ServerService Thread Pool -- 55) HCANN000001: Hibernate Commons Annotations {5.0.5.Final}
08:38:17,009 INFO [org.hibernate.dialect.Dialect] (ServerService Thread Pool -- 55) HHH000400: Using dialect: org.hibernate.dialect.H2Dialect
08:38:17,036 INFO [org.hibernate.envers.boot.internal.EnversServiceImpl] (ServerService Thread Pool -- 55) Envers integration enabled? : true
08:38:17,336 INFO [org.hibernate.orm.beans] (ServerService Thread Pool -- 55) HHH10005002: No explicit CDI BeanManager reference was passed to Hibernate, but CDI is available on the Hibernate ClassLoader.
08:38:17,376 INFO [org.hibernate.validator.internal.util.Version] (ServerService Thread Pool -- 55) HV000001: Hibernate Validator 6.0.22.Final
08:38:18,107 INFO [org.hibernate.hql.internal.QueryTranslatorFactoryInitiator] (ServerService Thread Pool -- 55) HHH000397: Using ASTQueryTranslatorFactory
08:38:18,419 INFO [org.keycloak.services] (ServerService Thread Pool -- 55) KC-SERVICES0050: Initializing master realm
08:38:19,789 INFO [org.jboss.resteasy.resteasy_jaxrs.i18n] (ServerService Thread Pool -- 55) RESTEASY002225: Deploying javax.ws.rs.core.Application: class org.keycloak.services.resources.KeycloakApplication
08:38:19,791 INFO [org.jboss.resteasy.resteasy_jaxrs.i18n] (ServerService Thread Pool -- 55) RESTEASY002205: Adding provider class org.keycloak.services.filters.KeycloakSecurityHeadersFilter from Application class org.keycloak.services.resources.KeycloakApplication
08:38:19,792 INFO [org.jboss.resteasy.resteasy_jaxrs.i18n] (ServerService Thread Pool -- 55) RESTEASY002200: Adding class resource org.keycloak.services.resources.ThemeResource from Application class org.keycloak.services.resources.KeycloakApplication
08:38:19,792 INFO [org.jboss.resteasy.resteasy_jaxrs.i18n] (ServerService Thread Pool -- 55) RESTEASY002205: Adding provider class org.keycloak.services.error.KeycloakErrorHandler from Application class org.keycloak.services.resources.KeycloakApplication
08:38:19,792 INFO [org.jboss.resteasy.resteasy_jaxrs.i18n] (ServerService Thread Pool -- 55) RESTEASY002200: Adding class resource org.keycloak.services.resources.JsResource from Application class org.keycloak.services.resources.KeycloakApplication
08:38:19,793 INFO [org.jboss.resteasy.resteasy_jaxrs.i18n] (ServerService Thread Pool -- 55) RESTEASY002220: Adding singleton resource org.keycloak.services.resources.RealmsResource from Application class org.keycloak.services.resources.KeycloakApplication
08:38:19,793 INFO [org.jboss.resteasy.resteasy_jaxrs.i18n] (ServerService Thread Pool -- 55) RESTEASY002220: Adding singleton resource org.keycloak.services.resources.RobotsResource from Application class org.keycloak.services.resources.KeycloakApplication
08:38:19,793 INFO [org.jboss.resteasy.resteasy_jaxrs.i18n] (ServerService Thread Pool -- 55) RESTEASY002220: Adding singleton resource org.keycloak.services.resources.admin.AdminRoot from Application class org.keycloak.services.resources.KeycloakApplication
08:38:19,794 INFO [org.jboss.resteasy.resteasy_jaxrs.i18n] (ServerService Thread Pool -- 55) RESTEASY002210: Adding provider singleton org.keycloak.services.util.ObjectMapperResolver from Application class org.keycloak.services.resources.KeycloakApplication
08:38:19,794 INFO [org.jboss.resteasy.resteasy_jaxrs.i18n] (ServerService Thread Pool -- 55) RESTEASY002220: Adding singleton resource org.keycloak.services.resources.WelcomeResource from Application class org.keycloak.services.resources.KeycloakApplication
08:38:19,854 INFO [org.wildfly.extension.undertow] (ServerService Thread Pool -- 55) WFLYUT0021: Registered web context: '/auth' for server 'default-server'
08:38:19,893 INFO [org.jboss.as.server] (ServerService Thread Pool -- 43) WFLYSRV0010: Deployed "keycloak-server.war" (runtime-name : "keycloak-server.war")
08:38:19,919 INFO [org.jboss.as.server] (Controller Boot Thread) WFLYSRV0212: Resuming server
08:38:19,921 INFO [org.jboss.as] (Controller Boot Thread) WFLYSRV0025: Keycloak 15.0.2 (WildFly Core 15.0.1.Final) started in 10563ms - Started 594 of 872 services (584 services are lazy, passive or on-demand)
08:38:19,922 INFO [org.jboss.as] (Controller Boot Thread) WFLYSRV0060: Http management interface listening on http://127.0.0.1:9990/management
08:38:19,923 INFO [org.jboss.as] (Controller Boot Thread) WFLYSRV0051: Admin console listening on http://127.0.0.1:9990
创建admin用户
浏览器访问http://localhost:8080/auth界面,然后输入管理员用户密码,如下图:
注:
这个8080端口可以通过修改standalone/configuration/standalone.xml文件进行重置

登录控制台
账户密码输入完成后,可点击左侧Administration Console(http://localhost:8080/auth/admin)跳转到控制台登录界面
控制台登录界面
输入刚才创建的管理员账号密码进行登录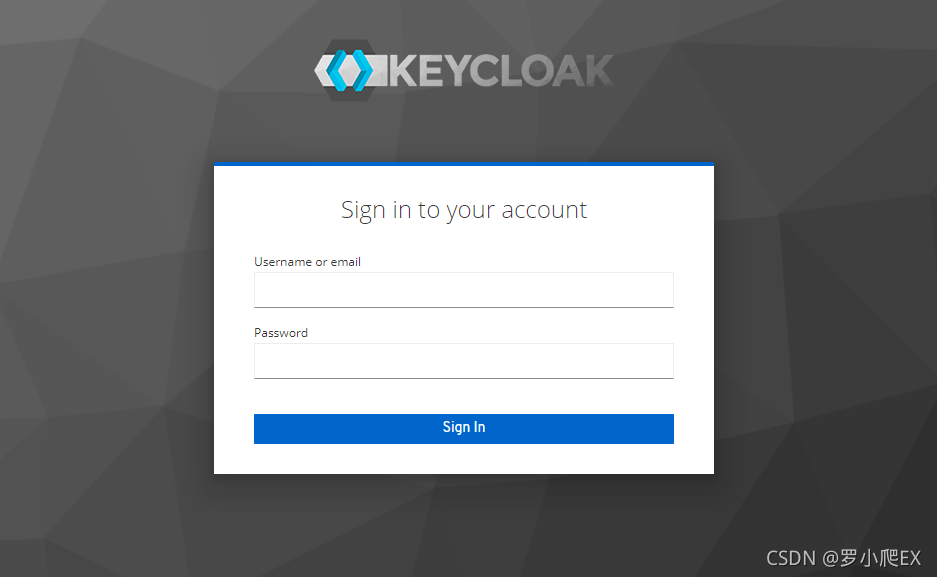
控制台首页
新建realm
realm领域,即用户池的概念,即realm下可以新建多个client(客户端,即需要认证的应用),
即在同一个realm下的不同client可以共享realm下的用户信息,
也就是说我们realm下的同一个用户可以在realm下的不同client进行登录(SSO)。
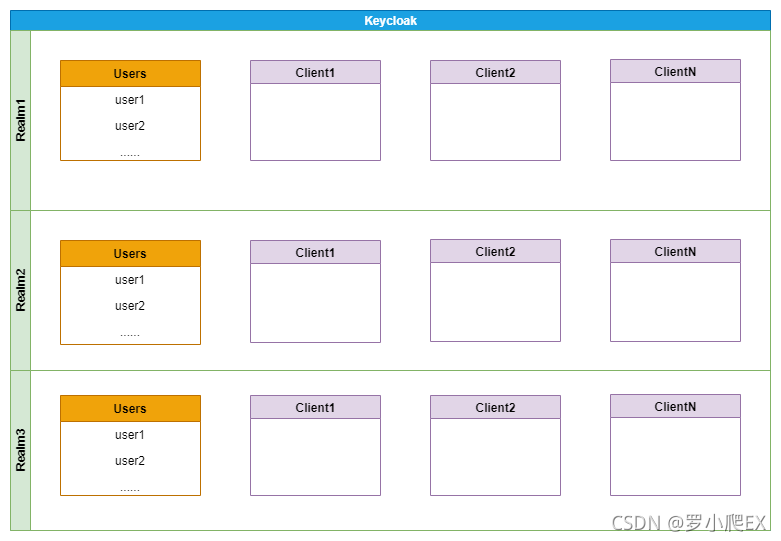
新建用户
选中新建的realm,然后点击左侧菜单Manage -> Users -> 右上角按钮Add user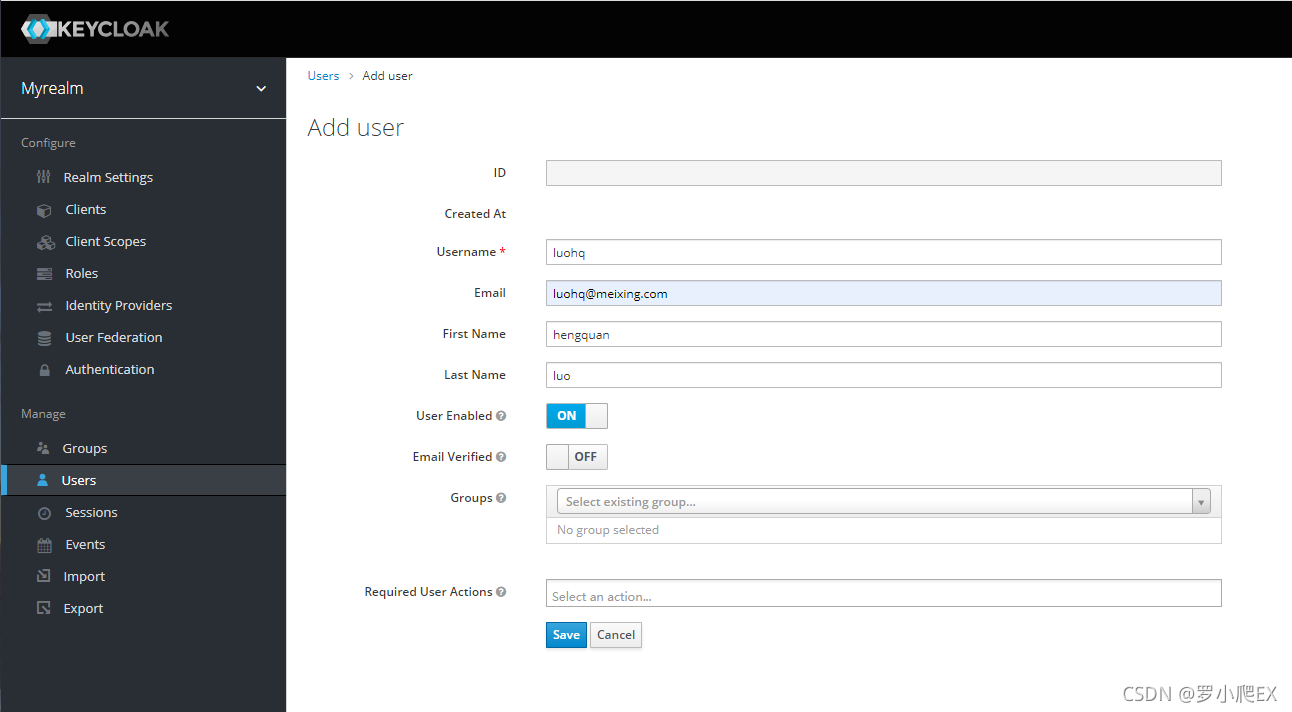
设置密码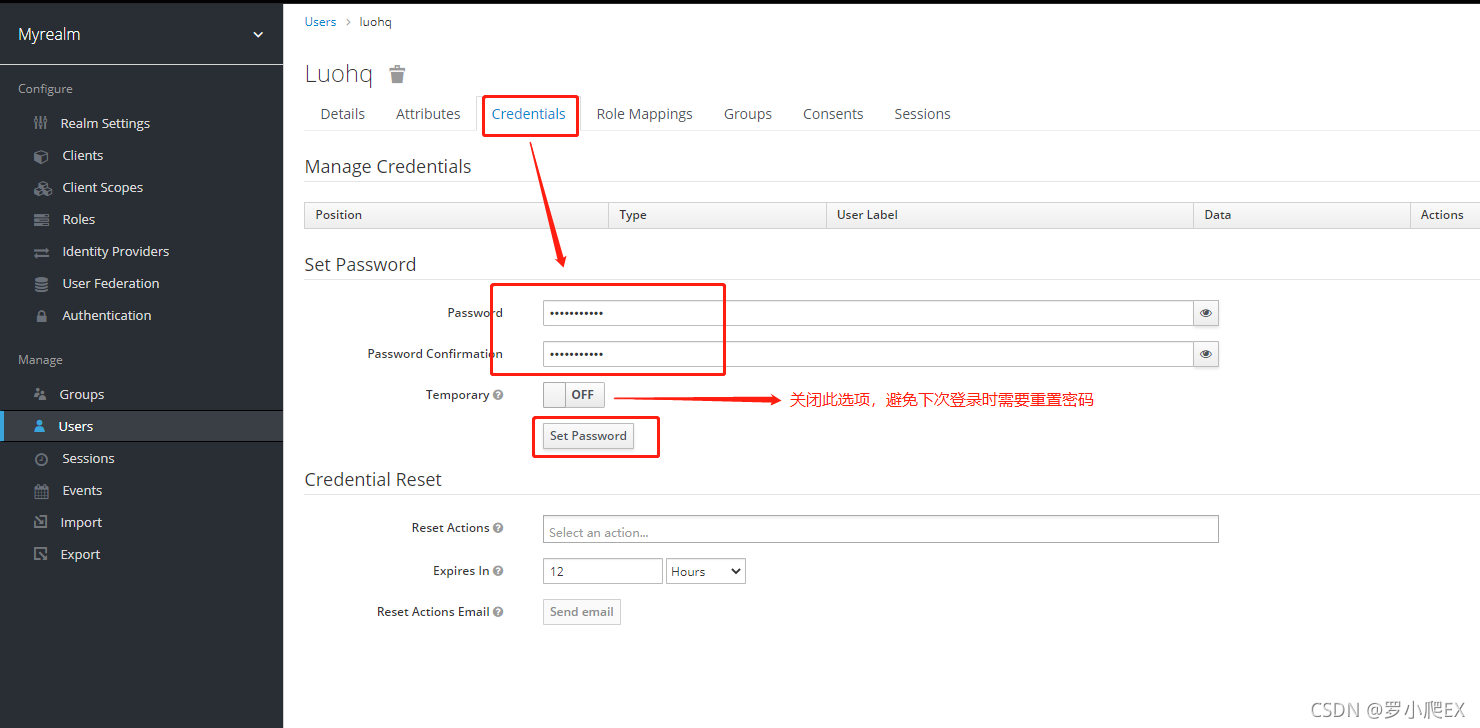
之后便可以进入Account Console(http://localhost:8080/auth/realms/myrealm/account/#/),用新创建的用户登录后,用户即可进行账户信息的管理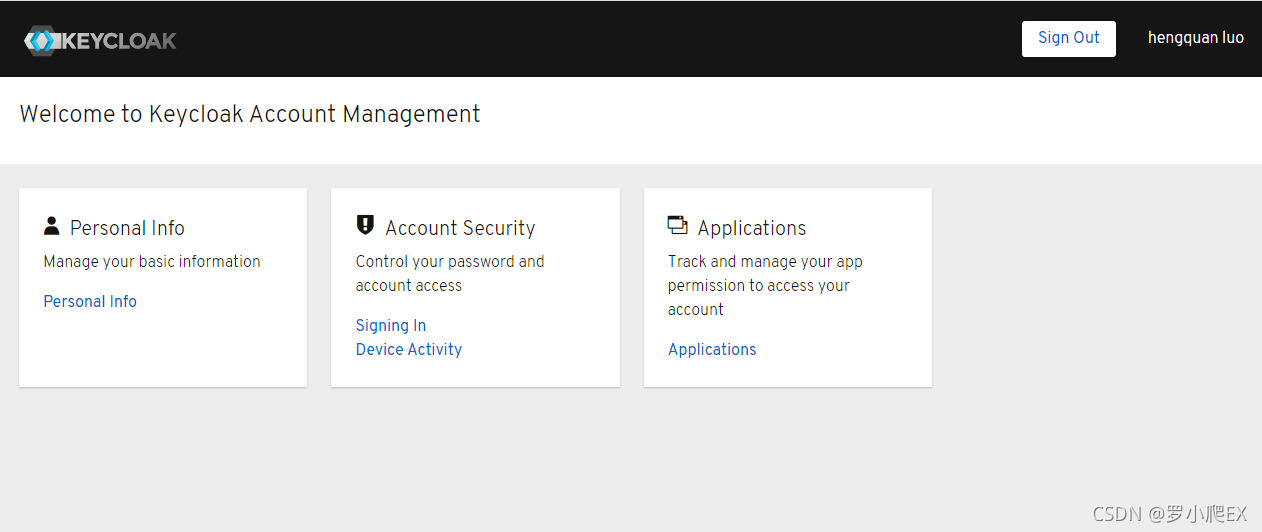
新建client
新建一个client,该client对应keycloak官方示例网站https://www.keycloak.org/app/,且客户端协议默认为openid-connect,
即将https://www.keycloak.org/app/配置为当前搭建Keycloak下myrealm的一个client,
可以通过当前搭建的keycloak进行登录,登录成功后跳转到https://www.keycloak.org/app/。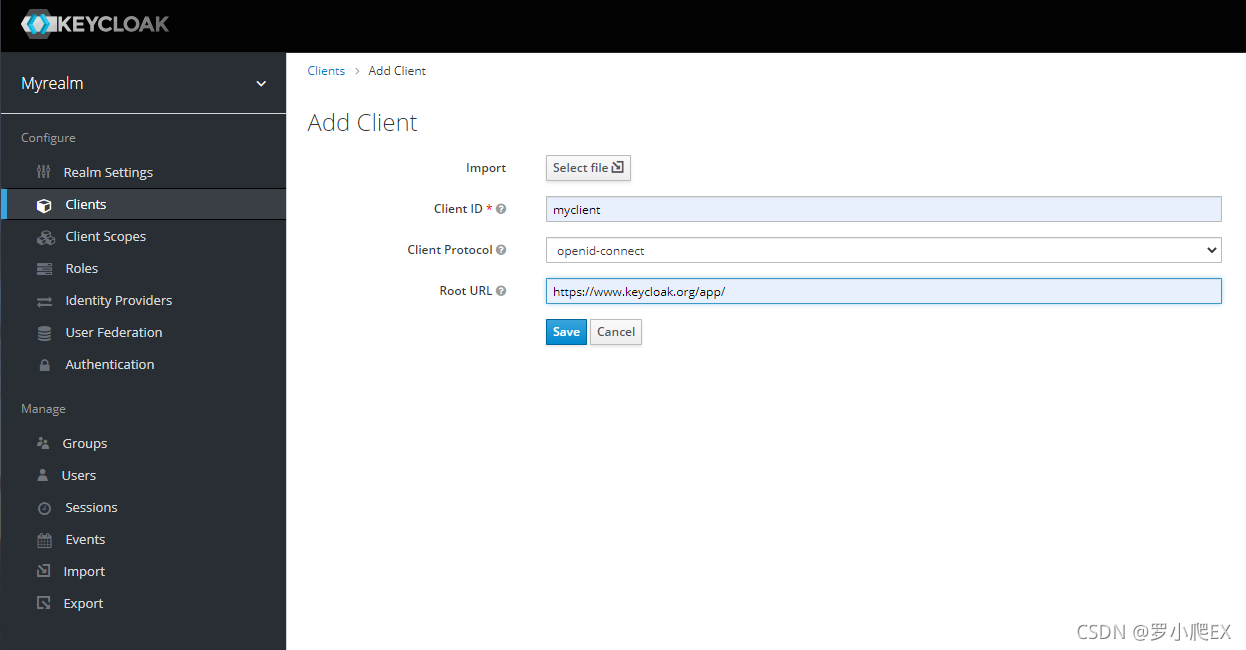
最后,我们需要使用到 OpenID 的一些 URI,这些 URI 会 OAuth 客户端中用到
http://localhost:8080/auth/realms/myrealm/.well-known/openid-configuration
TODO:全局域名修改,上图配置仅部分url生效
如下为获取到的oidc协议配置信息
{
"issuer": "http://localhost:8080/auth/realms/myrealm",
"authorization_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/auth",
"token_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/token",
"introspection_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/token/introspect",
"userinfo_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/userinfo",
"end_session_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/logout",
"jwks_uri": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/certs",
"check_session_iframe": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/login-status-iframe.html",
"grant_types_supported": ["authorization_code", "implicit", "refresh_token", "password", "client_credentials", "urn:ietf:params:oauth:grant-type:device_code", "urn:openid:params:grant-type:ciba"],
"response_types_supported": ["code", "none", "id_token", "token", "id_token token", "code id_token", "code token", "code id_token token"],
"subject_types_supported": ["public", "pairwise"],
"id_token_signing_alg_values_supported": ["PS384", "ES384", "RS384", "HS256", "HS512", "ES256", "RS256", "HS384", "ES512", "PS256", "PS512", "RS512"],
"id_token_encryption_alg_values_supported": ["RSA-OAEP", "RSA-OAEP-256", "RSA1_5"],
"id_token_encryption_enc_values_supported": ["A256GCM", "A192GCM", "A128GCM", "A128CBC-HS256", "A192CBC-HS384", "A256CBC-HS512"],
"userinfo_signing_alg_values_supported": ["PS384", "ES384", "RS384", "HS256", "HS512", "ES256", "RS256", "HS384", "ES512", "PS256", "PS512", "RS512", "none"],
"request_object_signing_alg_values_supported": ["PS384", "ES384", "RS384", "HS256", "HS512", "ES256", "RS256", "HS384", "ES512", "PS256", "PS512", "RS512", "none"],
"request_object_encryption_alg_values_supported": ["RSA-OAEP", "RSA-OAEP-256", "RSA1_5"],
"request_object_encryption_enc_values_supported": ["A256GCM", "A192GCM", "A128GCM", "A128CBC-HS256", "A192CBC-HS384", "A256CBC-HS512"],
"response_modes_supported": ["query", "fragment", "form_post", "query.jwt", "fragment.jwt", "form_post.jwt", "jwt"],
"registration_endpoint": "http://localhost:8080/auth/realms/myrealm/clients-registrations/openid-connect",
"token_endpoint_auth_methods_supported": ["private_key_jwt", "client_secret_basic", "client_secret_post", "tls_client_auth", "client_secret_jwt"],
"token_endpoint_auth_signing_alg_values_supported": ["PS384", "ES384", "RS384", "HS256", "HS512", "ES256", "RS256", "HS384", "ES512", "PS256", "PS512", "RS512"],
"introspection_endpoint_auth_methods_supported": ["private_key_jwt", "client_secret_basic", "client_secret_post", "tls_client_auth", "client_secret_jwt"],
"introspection_endpoint_auth_signing_alg_values_supported": ["PS384", "ES384", "RS384", "HS256", "HS512", "ES256", "RS256", "HS384", "ES512", "PS256", "PS512", "RS512"],
"authorization_signing_alg_values_supported": ["PS384", "ES384", "RS384", "HS256", "HS512", "ES256", "RS256", "HS384", "ES512", "PS256", "PS512", "RS512"],
"authorization_encryption_alg_values_supported": ["RSA-OAEP", "RSA-OAEP-256", "RSA1_5"],
"authorization_encryption_enc_values_supported": ["A256GCM", "A192GCM", "A128GCM", "A128CBC-HS256", "A192CBC-HS384", "A256CBC-HS512"],
"claims_supported": ["aud", "sub", "iss", "auth_time", "name", "given_name", "family_name", "preferred_username", "email", "acr"],
"claim_types_supported": ["normal"],
"claims_parameter_supported": true,
"scopes_supported": ["openid", "offline_access", "email", "profile", "address", "microprofile-jwt", "web-origins", "phone", "roles"],
"request_parameter_supported": true,
"request_uri_parameter_supported": true,
"require_request_uri_registration": true,
"code_challenge_methods_supported": ["plain", "S256"],
"tls_client_certificate_bound_access_tokens": true,
"revocation_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/revoke",
"revocation_endpoint_auth_methods_supported": ["private_key_jwt", "client_secret_basic", "client_secret_post", "tls_client_auth", "client_secret_jwt"],
"revocation_endpoint_auth_signing_alg_values_supported": ["PS384", "ES384", "RS384", "HS256", "HS512", "ES256", "RS256", "HS384", "ES512", "PS256", "PS512", "RS512"],
"backchannel_logout_supported": true,
"backchannel_logout_session_supported": true,
"device_authorization_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/auth/device",
"backchannel_token_delivery_modes_supported": ["poll", "ping"],
"backchannel_authentication_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/ext/ciba/auth",
"backchannel_authentication_request_signing_alg_values_supported": ["PS384", "ES384", "RS384", "ES256", "RS256", "ES512", "PS256", "PS512", "RS512"],
"require_pushed_authorization_requests": false,
"pushed_authorization_request_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/ext/par/request",
"mtls_endpoint_aliases": {
"token_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/token",
"revocation_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/revoke",
"introspection_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/token/introspect",
"device_authorization_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/auth/device",
"registration_endpoint": "http://localhost:8080/auth/realms/myrealm/clients-registrations/openid-connect",
"userinfo_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/userinfo",
"pushed_authorization_request_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/ext/par/request",
"backchannel_authentication_endpoint": "http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/ext/ciba/auth"
}
}
测试client登录
官方示例点击:https://www.keycloak.org/app/进入如下界面,保存配置后即可通过我们本地搭建的keycloak进行登录测试
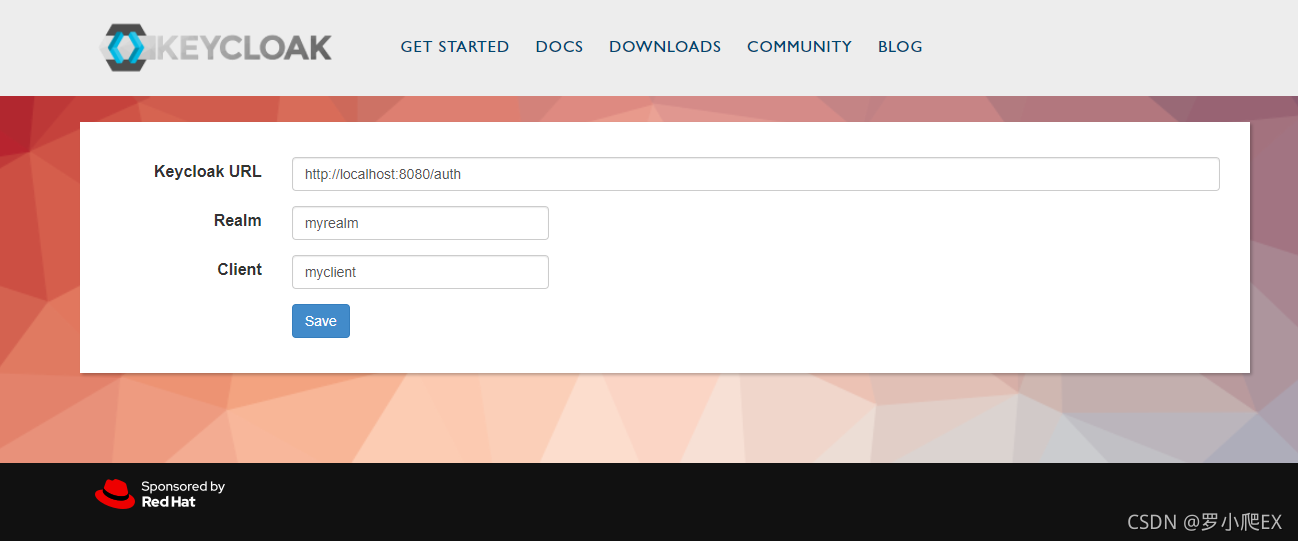
保存后即可通过Sign In、Sign Out按钮进行登录测试,如下图点击Sign In可进入登录界面
如下为登录界面URL
http://localhost:8080/auth/realms/myrealm/protocol/openid-connect/auth
?client_id=myclient
&redirect_uri=https://www.keycloak.org/app/#url=http://localhost:8080/auth&realm=myrealm&client=myclient
&state=0c7b6a30-3f40-444d-804b-e40eee8d2507
&response_mode=fragment
&response_type=code
&scope=openid
&nonce=47ad39dc-8969-40db-86c7-f48f927c7c07
使用我们刚才创建的user进行登录后即可进入到keycloak测试首页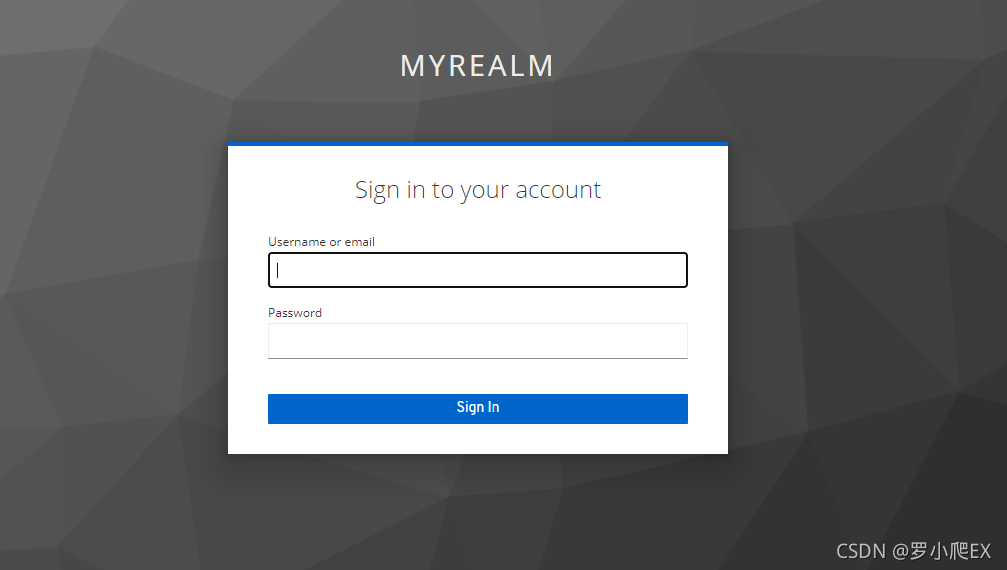
登录成功界面
设置client为confidential(即需要clientId+clientSecret进行验证)
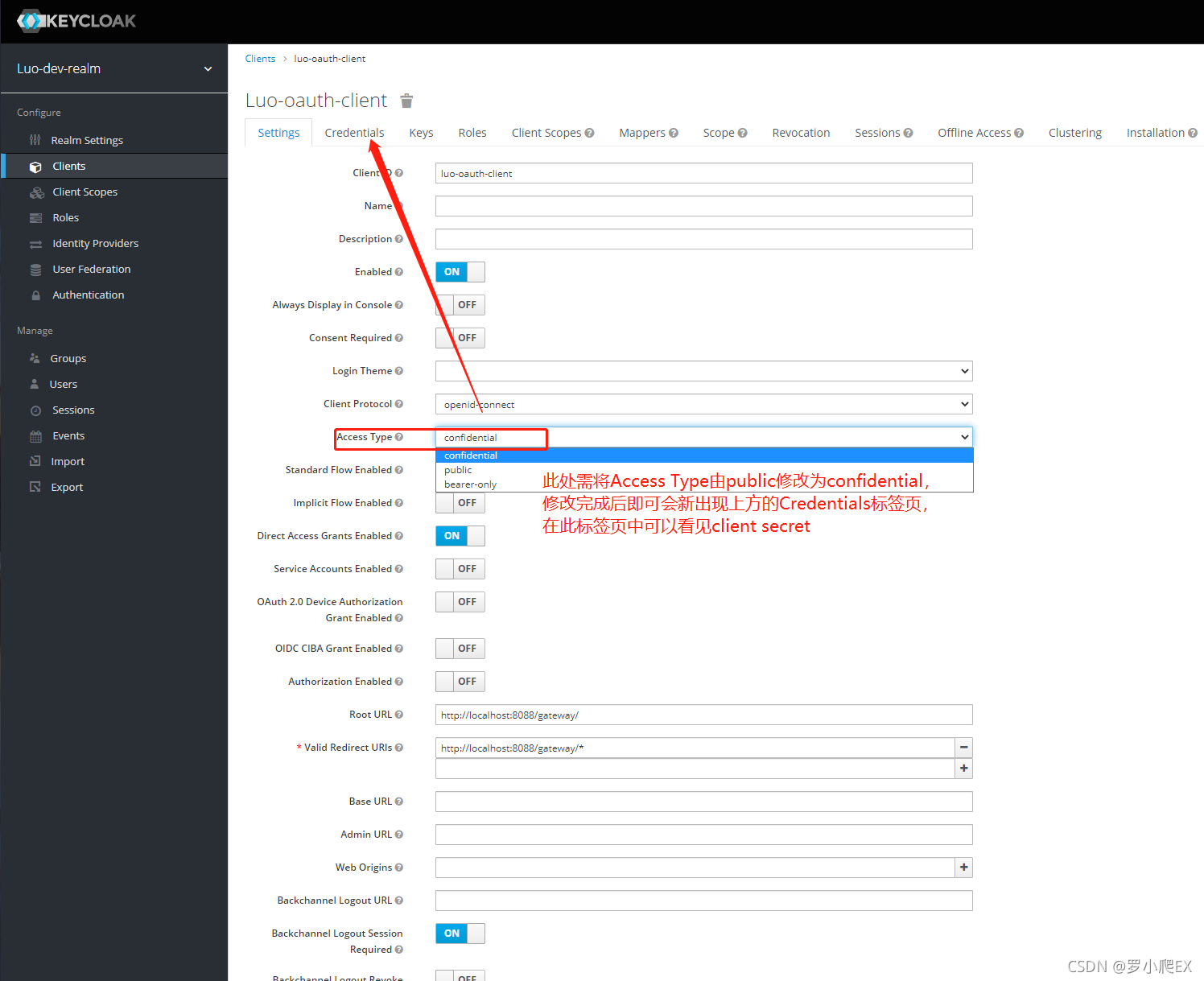
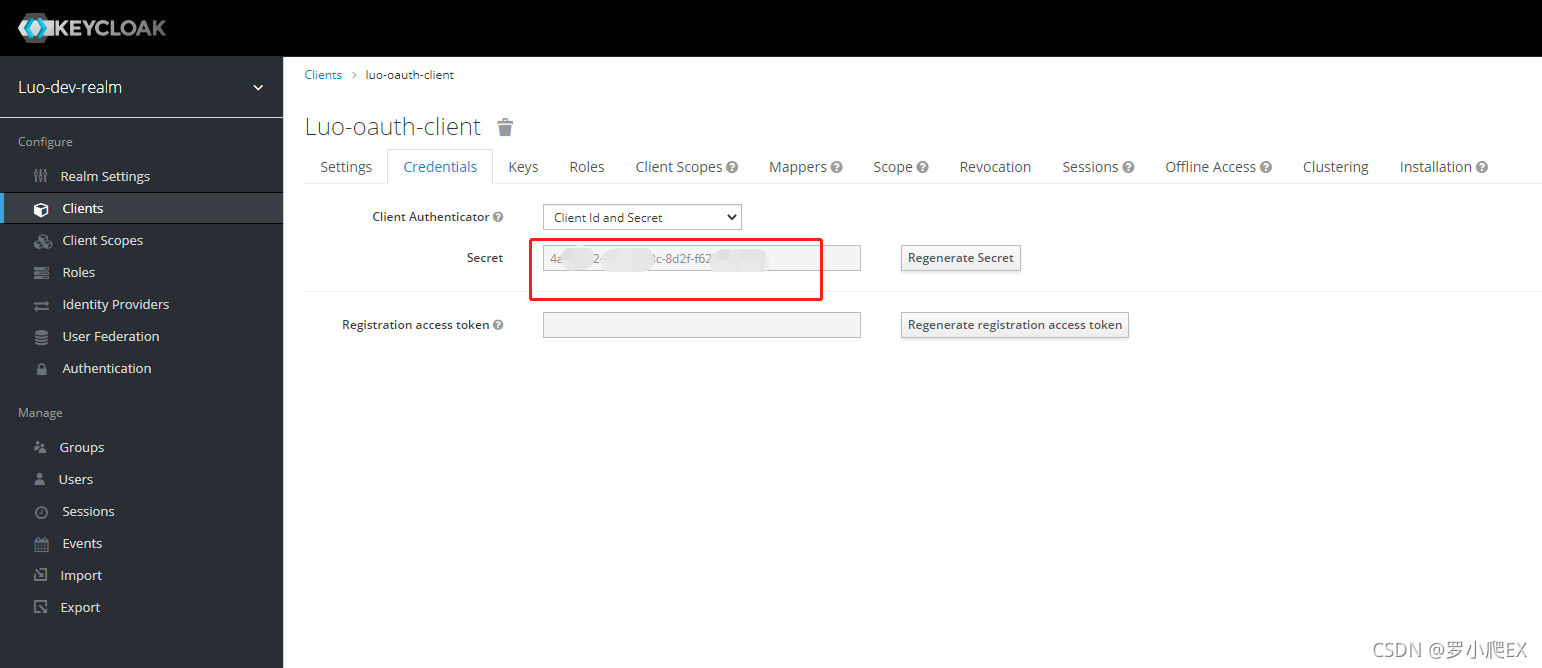
参考:
https://www.keycloak.org/
https://www.keycloak.org/getting-started/getting-started-zip
https://www.keycloak.org/docs/latest/server_installation/index.html#database-configuration
Top 5 Open Source Single Sign-On Software In the Year 2021
stackoverflow - 设置client Access Type为Confidential(机密的)