1.配置静态NAT,内部网络的私有IP地址转换为公有IP地址,IP地址对是一对一,实现PC机可以访问Server1
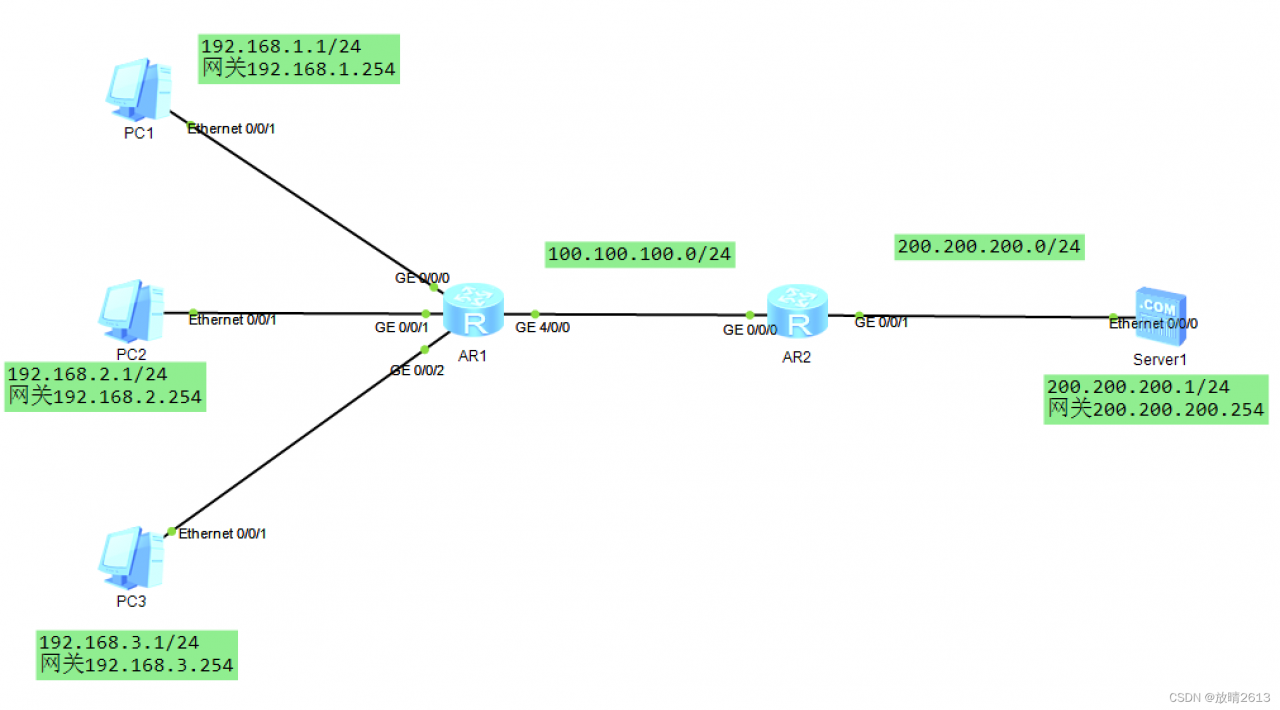
AR1:
interface GigabitEthernet0/0/0
ip address 192.168.1.254 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 192.168.2.254 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 192.168.3.254 255.255.255.0
#
interface GigabitEthernet4/0/0
ip address 100.100.100.1 255.255.255.0
nat static global 100.100.100.5 inside 192.168.3.1 netmask 255.255.255.255
nat static global 100.100.100.3 inside 192.168.1.1 netmask 255.255.255.255
nat static global 100.100.100.4 inside 192.168.2.1 netmask 255.255.255.255
#
ip route-static 0.0.0.0 0.0.0.0 100.100.100.2
AR2:
interface GigabitEthernet0/0/0
ip address 100.100.100.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 200.200.200.254 255.255.255.0
2. 配置动态NAT,基于地址池来实现私有地址和公有地址的转换,转换是随机的
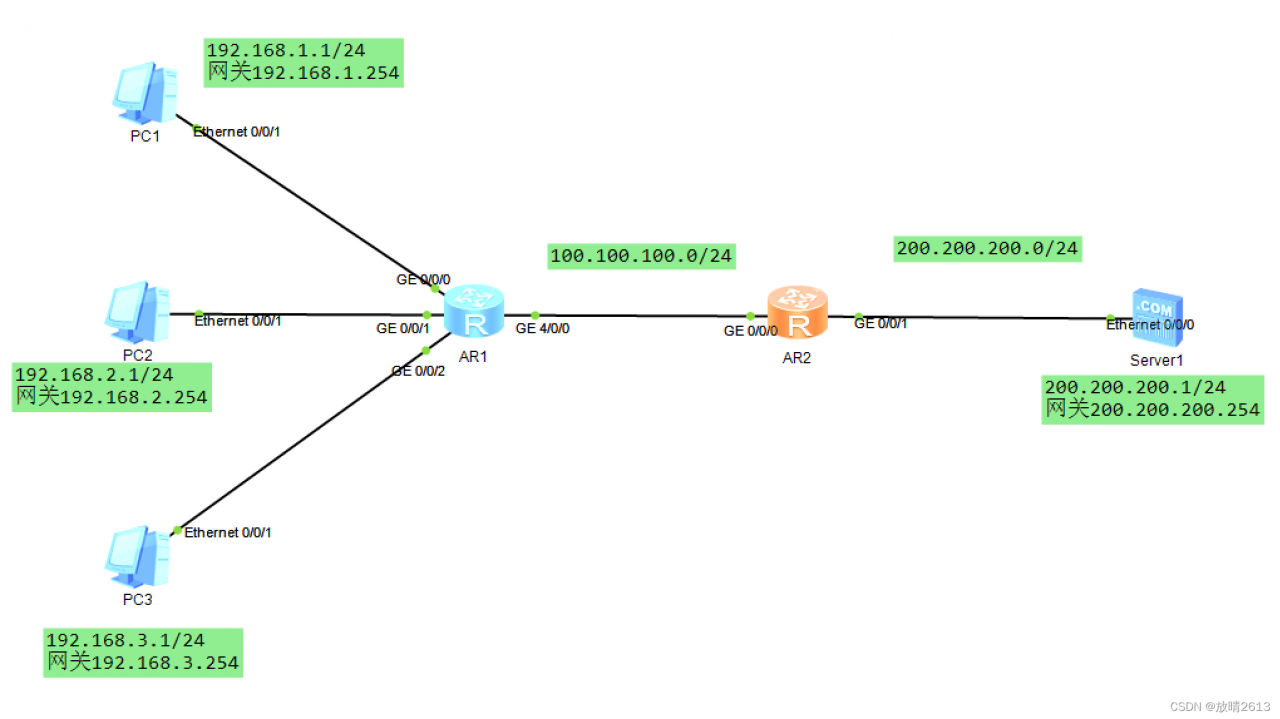
interface GigabitEthernet0/0/0
ip address 192.168.1.254 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 192.168.2.254 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 192.168.3.254 255.255.255.0
#
interface GigabitEthernet4/0/0
ip address 100.100.100.1 255.255.255.0
#
ip route-static 0.0.0.0 0.0.0.0 100.100.100.2
#设置公网地址池
nat address-group 1 100.100.100.3 100.100.100.254
#创建ACL
acl 2000
rule 5 permit source 192.168.1.0 0.0.0.255
rule 10 permit source 192.168.2.0 0.0.0.255
rule 15 permit source 192.168.3.0 0.0.0.255
#匹配ACL
interface GigabitEthernet4/0/0
nat outbound 2000 address-group 1 no-pat
AR2:
interface GigabitEthernet0/0/0
ip address 100.100.100.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 200.200.200.254 255.255.255.0
3. 配置Easy IP,转换成出接口地址
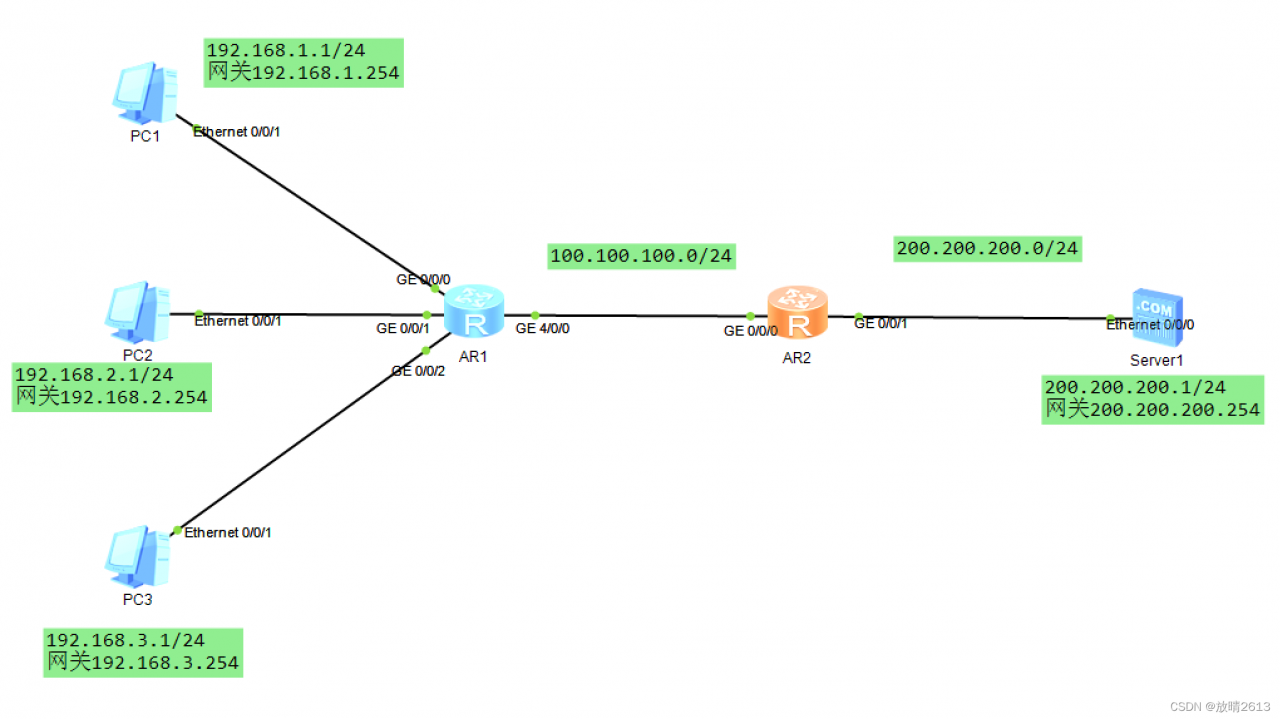
AR1:
interface GigabitEthernet0/0/0
ip address 192.168.1.254 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 192.168.2.254 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 192.168.3.254 255.255.255.0
#
interface GigabitEthernet4/0/0
ip address 100.100.100.1 255.255.255.0
#
ip route-static 0.0.0.0 0.0.0.0 100.100.100.2
#创建ACL
acl 2000
rule 5 permit source 192.168.1.0 0.0.0.255
rule 10 permit source 192.168.2.0 0.0.0.255
rule 15 permit source 192.168.3.0 0.0.0.255
#匹配ACL
interface GigabitEthernet4/0/0
nat outbound 2000
AR2:
interface GigabitEthernet0/0/0
ip address 100.100.100.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 200.200.200.254 255.255.255.0
4.NAT Server , 将内部的www服务器发布到外网,使其外部用户可以访问内部服务器www
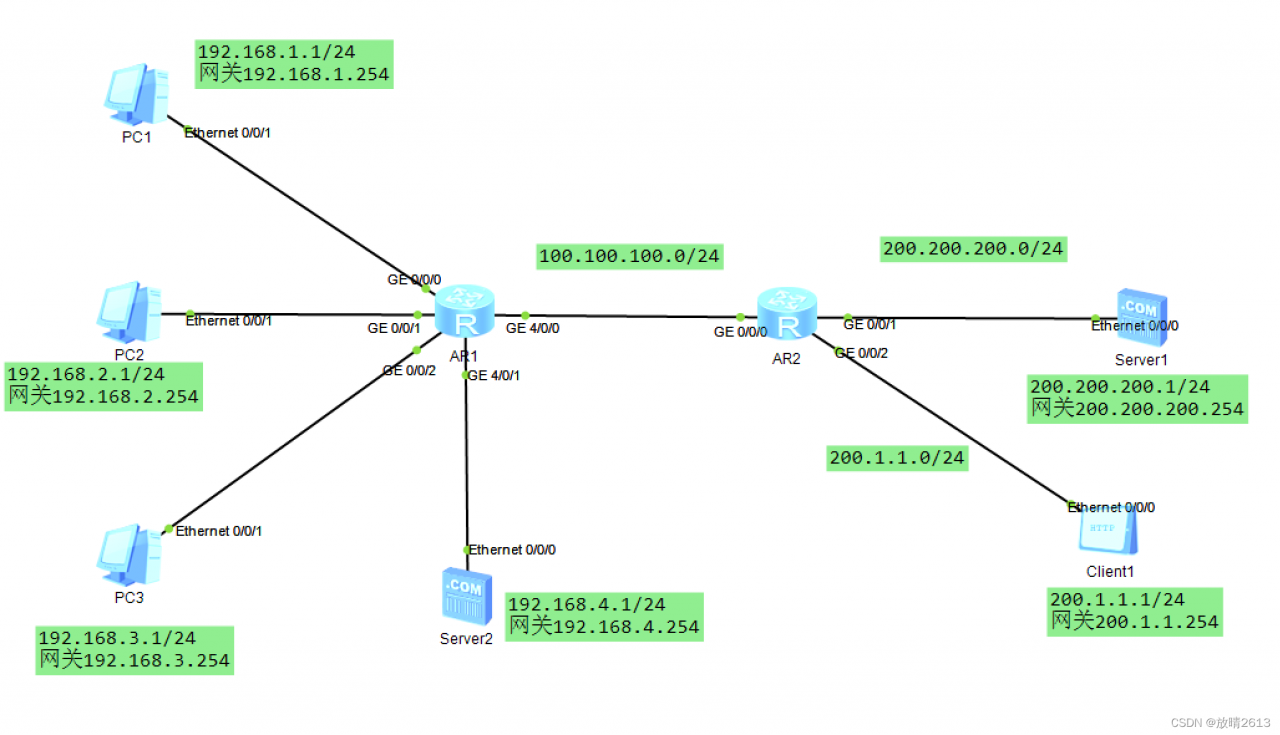
AR1:
interface GigabitEthernet0/0/0
ip address 192.168.1.254 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 192.168.2.254 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 192.168.3.254 255.255.255.0
#
interface GigabitEthernet4/0/0
ip address 100.100.100.1 255.255.255.0
#
interface GigabitEthernet4/0/1
ip address 192.168.4.254 255.255.255.0
#
ip route-static 0.0.0.0 0.0.0.0 100.100.100.2
#
acl 2000
rule 5 permit source 192.168.1.0 0.0.0.255
rule 10 permit source 192.168.2.0 0.0.0.255
rule 15 permit source 192.168.3.0 0.0.0.255
#
interface GigabitEthernet4/0/0
nat outbound 2000
nat server protocol tcp global 100.100.100.3 www inside 192.168.4.1 www (将内部的www服务器发布到外网,使其外部用户可以访问内部服务器www)
AR2:
interface GigabitEthernet0/0/0
ip address 100.100.100.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 200.200.200.254 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 200.1.1.254 255.255.255.0